There are various networking devices available. They are N devices and intermediary devices or networking devices in a computer network. Let us see the various networking devices.
Repeater
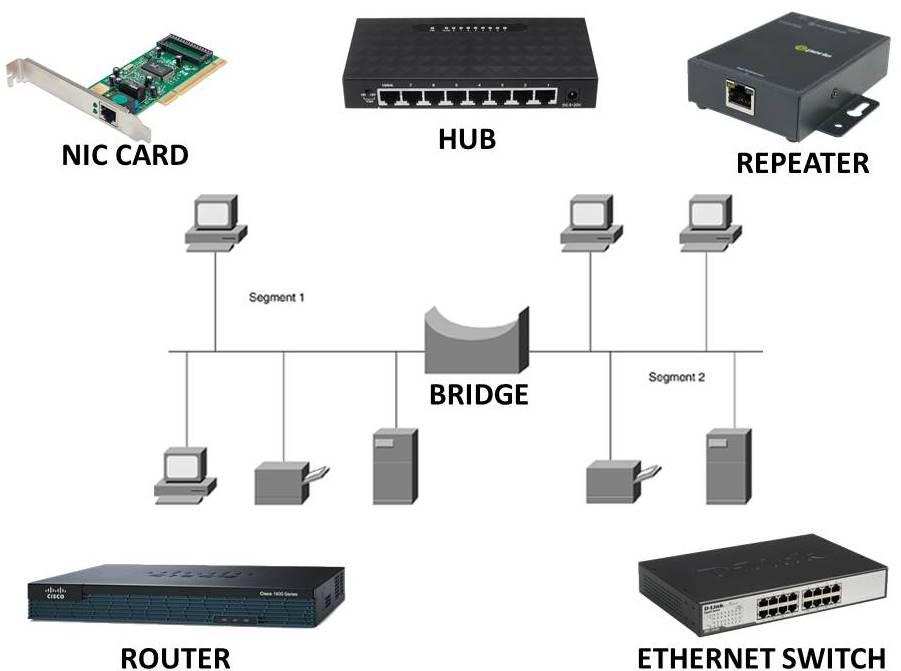
The first networking device that we would like to address is a repeater, it is a layer one device, it means it operates at physical layer. It just regenerates the signal in a single local area network. A repeater receives and retransmits incoming electrical wireless or optical signals with physical media like ethernet or wi-fi, data transitions can only span a limited distance before the quality of the signal. This signal degrades repeaters attempt to preserve signal integrity and extended distance over which data can safely travel. Repeaters are cost effective, simple to connect and can strengthen signal.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
Hub
The second networking devices is the hub, hub is a local area network device. It operates at physical layer that is, it is a layer one device and whatever it receives it always just broadcasts and that is the drawback of a hub. Hub will be used to send the data packets to all the connected devices.
Switch
The third networking device is the switch. A switch is also a local area networking device, and it connects devices in a single local area network. It is a layer two device, and it operates at data link layer switches and intelligent device. It stores the Mac address table unlike hub switch does unicasting it means it can send the data to the exact recipient whereas hub w broadcast today to all the recipients. Switch will send good data packet to the correct port and if the packets contain some error automatically those packets will be ignored. So in switch, error checking will be done.
Bridge
The next networking device is the bridge. A bridge is also a layer two device it operates at the data link layer. A bridge connects to local area network segments that are running with the same protocols. A bridge can also regenerate the signals because, a bridge is a combination of a repeater and Mac address reading capability. So, it interconnects two LANS working on same protocol.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
Router
The next networking device is the router. A router is a layer three device it operates at the network layer. Routers take forwarding decisions based on the IP addresses and router is a networking device that can connect two or more different LANS that are two or more different protocols so one side if it is Ethernet another side if it is Wi-Fi and router can connect these two different technologies as well. Packets will be sent to the destination by using the different routing algorithm. Dynamically the routing will be changed from one packet to other, as it selects the best path.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
Multilayer switch
The next networking device which is a multilayer switch or a layer three switch. Generally, switches are layer two switch, it means it works at the data link layer and it takes forwarding decisions based on MAC addresses. We have a contemporary switch which is a multilayer switch it can be a layer two switch as well as layer three switch, so it does the functionalities of a switch as well as the functionality software router to some extent. So multilayer switch or a layer three switch can act as a router as well as a switch.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
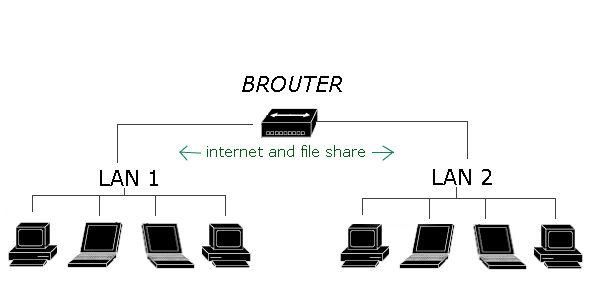
Brouter
The next networking device which is a brouter. A brouter is a combination of a bridge as well as a router. A bridge can connect two different LAN segments of same protocol. A router can connect to our more different protocols but brouter is a combination of a bridge as well as a router it means it can act as a layer two bridge or it can act as a layer three router.
Modem
The next networking device it is the modem. Modem means modulator and demodulator. Modulator means the digital information is going to be carried on an analogue carrier signal and demodulator just retrieves the transmitter signal that is the transmitter digital information. For example, in a traditional landline phones that is exclusively for carrying a voice signals, that is analogue signals. But we can send our digital information using modem. So, modem does both modulation as well as demodulation tasks.
For cloud-based solutions for the businesses like Google, AWS, and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/
Gateway
The next networking device is the gateway. It passes the data from one network to another network which are handled in different parts which are using the different protocols or a different network model. Gateway is a network device which is used to connect two or more dissimilar networks which uses different set of protocols. It also uses the packet switching.
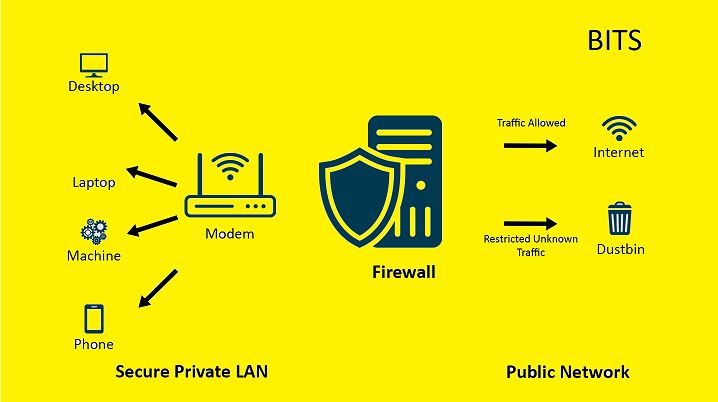
Firewall
The last networking device that is the firewall. This firewall is a networking device only, but still it is mainly used for providing security to the network. For example, if it deploys a firewall in our campus or in our network. This firewall filters the packet. It filters the packets based on the IP addresses, based on port numbers, based on the application data, in the network you don’t want any malicious things to happen. So, you can protect your network by installing a firewall. So, in a network firewall filters the incoming traffic as well as outgoing traffic. Firewall is nothing but a set of passive rules which are defined to enable the set standards of communication between the internal and the external network. Through this firewall only a specific set of communications can happen. If you want to allow any sort of communication through the firewall, we have two options we can either configure DMZ or a port forward.
For general support issues of home users please visit: https://www.computerepaironsite.com.au/
We have listed various network devices repeater, hub, switches, bridges, routers, multilayer switches so layer three switch brouters modem firewall.