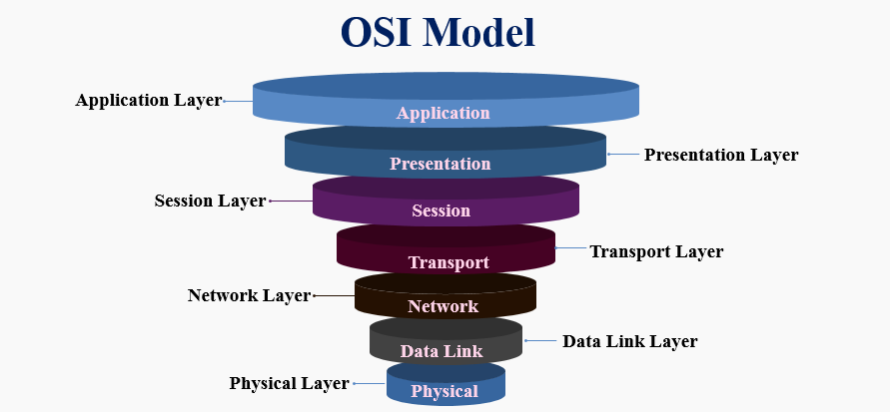
The OSI Model: What Is It?
The Open Systems Interconnection (OSI) model describes the seven levels that computer systems use to communicate over a network. Early in the 1980s, all significant computer and telecommunications businesses accepted it as the first industry standard for network communications.
The simplified TCP/IP model, rather than OSI, is the foundation of the modern Internet. The OSI 7-layer model is still extensively used, nevertheless, as it aids in isolating and troubleshooting networking issues as well as helping to depict and convey how networks function.
The OSI Model is divided into layers, each performing a specialised task and interacting with layers above and below. The application layer attacks target layer 7, while the protocol layer attacks target layers 3 and 4. DDoS assaults target particular network connectivity tiers.
Why is the OSI model relevant?
The OSI Model is still beneficial for diagnosing network issues even though the modern Internet doesn’t precisely adhere to it (instead, it closely follows the less complex Internet protocol suite). The OSI Model can assist in deconstructing the issue and identifying the troubleshooting step, whether it concerns one person unable to connect their laptop to the Internet or a website unavailable to thousands of users. Users can avoid a lot of pointless labour if the issue is limited to a single model layer.
1. Physical Layer
The physical layer is in charge of the wired or wireless connections that physically connect network nodes. It is responsible for bit rate regulation and the transmission of raw data, which is merely a stream of 0s and 1s, in addition to specifying the connection, electrical cable, or wireless technology interconnecting the devices.
OSI was first presented in 1983 by executives from the most prominent computer and telecom firms, and it was accepted as an international standard in 1984 by ISO.
2. Data Link Layer
The data link layer creates and breaks connections between two network nodes that are physically close. Frames are made from packets, which are then sent from source to destination. This layer comprises two components: Media Access Control (MAC), which utilises MAC addresses to connect devices and specifies permissions to transmit and receive data, and Logic Link Control (LLC), which identifies network protocols, does error checking and synchronises frames.
3. Network Layer
The network layer serves two primary purposes. One divides segments into network packets and puts them back together. The alternative packet routing method involves finding the optimum route through a physical network. To route packets to a destination node, the network layer needs network addresses, commonly Internet Protocol addresses.
4. Transport Layer
Data transferred in the session layer is divided into “segments” by the transport layer at the receiving end. On the receiving end, it combines the segments to create data that the session layer may use. The transport layer performs error control, which determines whether received data is received wrongly and, if not, requests it again, as well as flow control, which sends data at a pace that matches the connection speed of the receiving device.
5. Session layer
The session layer establishes sessions, or channels of communication, between devices. It is in charge of starting sessions, ensuring they are active and open while data is being exchanged, and shutting them down once communication is complete. The session layer can also create checkpoints during data transmission to enable devices to continue where they left off if the session ends.
6. Presentation layer
Data is prepared for the application layer by the presentation layer. It describes how two devices should encrypt, encode, and reduce data to be securely received on the other end. The presentation layer processes any data transmitted by the application layer before being delivered via the session layer.
7. Application layer
End-user applications like web browsers and email clients operate at the application layer. It offers protocols that let computer programs transmit and receive data and give consumers helpful information. The Hypertext Transfer Protocol is an example of an application layer protocol (HTTP). Also, File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol, which is known (as SMTP), and Domain Name System (DNS) are considered examples.
How data flows through the OSI model
To transfer human-readable data from one device to another over a network, data must flow down the seven layers of the OSI Model on the transmitting end and then up the seven layers on the receiving end.
Mr Cooper wishes to email Ms Palmer. His email application will send the message to the application layer, selecting SMTP protocol and sending the information to the presentation layer. The presentation layer will compress the data when the data reaches the session layer.
When the data reaches the sender’s transportation layer, it is segmented there before being divided into packets at the network layer and then further into frames at the data link layer. The physical layer will take those frames from the data link layer and turn them into a bitstream of 1s and 0s before sending them across a physical media, such as a wire.
The data will pass through the identical set of layers on Ms Palmer’s device, but in the opposite sequence, after her computer receives it via physical media (such as her wifi). The physical layer will first transform the bitstream of 1s and 0s into frames before being transmitted to the data link layer. The data link layer subsequently reconfigures the structures into packets for the network layer. The transport layer will reassemble the segments into a single piece of data after the network layer has divided the packages into parts.
The communication session will then end as the data is passed from the presentation layer to the receiver’s session layer. The application layer will then receive the basic information once the presentation layer has removed the compression. Ms Palmer can see Mr Cooper’s email on her laptop screen after the application layer passes the human-readable data to her email program.
http://grewquartersupporting.com/6ecf6c8c?key=9ca601a9f47c735df76d5ca46fa26a66&submetric=14925975