Layer 2 technologies means OSI data link layer. Today’s enterprises replace the hubs with switches to share resources over the internet to create switched technology. In hubs all the devices share the network causes the collision while data is transmitting. On the other hand, switches broadcast domain will share resources with other devices without any collision occurrence. Switches operates in full duplex and half-duplex as well. Provides greater than 10mbps bandwidth and small increase in cost gives greater and high availability.
Virtual LANs: Virtual LANs can be created to have different broadcast domain with in the switch which broadcast frame propagates through the network. VLANS are virtually created in one physical switch. One VLAN can not access the other VLAN without the router tokens. Must have to have a router token to pass into other VLAN.
[1]
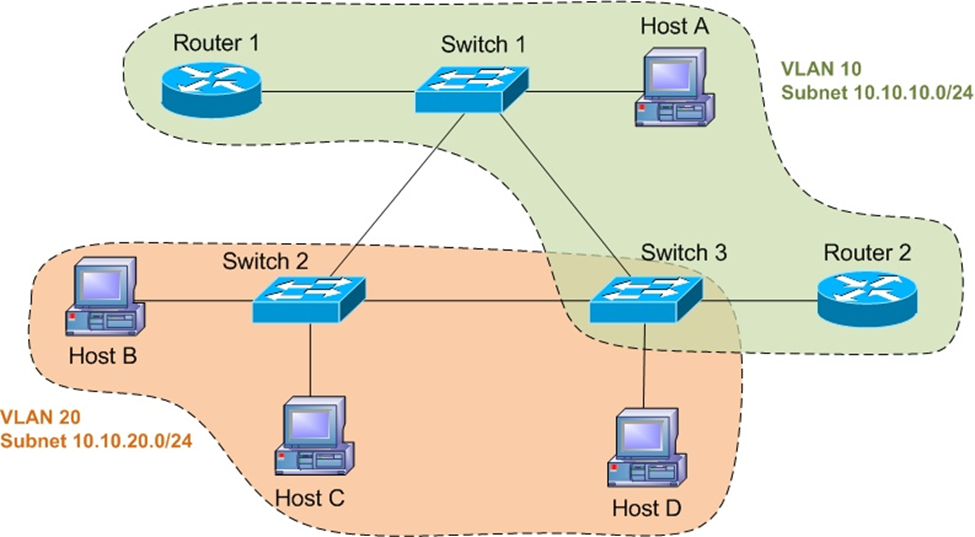
Each port can support only one VLAN. When a port broadcasts a frame other port within the VLAN can only receives it. The above diagram has switch 1 has host A which wants to communicates with host B in switch 2. Both are in different VLANs with different subnets. These 2 devices can only communicate via trunk 802.1Q technology.
[1]
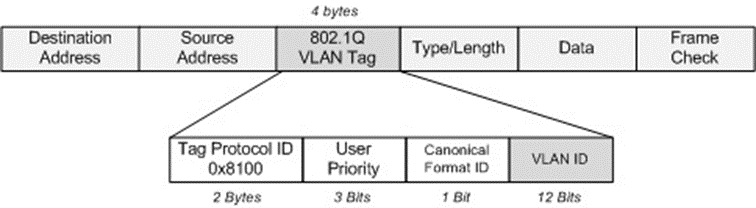
802.1Q is 32-bit tag frame. In that last 12 bits are used to carry VLAN id field which starts from 0 to 4095 maximum number can assign to VLAN. The port that carries data for multiple VLANs called trunk port. It can be configured on a switch to carry data over the cables. It uses either ISL or 802.1Q protocols. The concept of 802.1Q is in native VLAN and switch ports are all in native VLAN 1 by default. This protocol allows native VLAN to carry multiple VLANs data on a single link. In case of other switches does not support trunking concept still can send the data over single link. The most important reasons for using VLANs network security, broadcast distribution and bandwidth utilization. Another benefit of VLANs creation is any other group user who must not to receive the data can be prohibited by VLAN.
Spanning Tree Protocol: Spanning tree protocol is a loop prevention protocol enables switch to talk over the network with other switches to find physical loops. If any loop found STP protocol specifies switch to use a loop free logical topology.
[1]
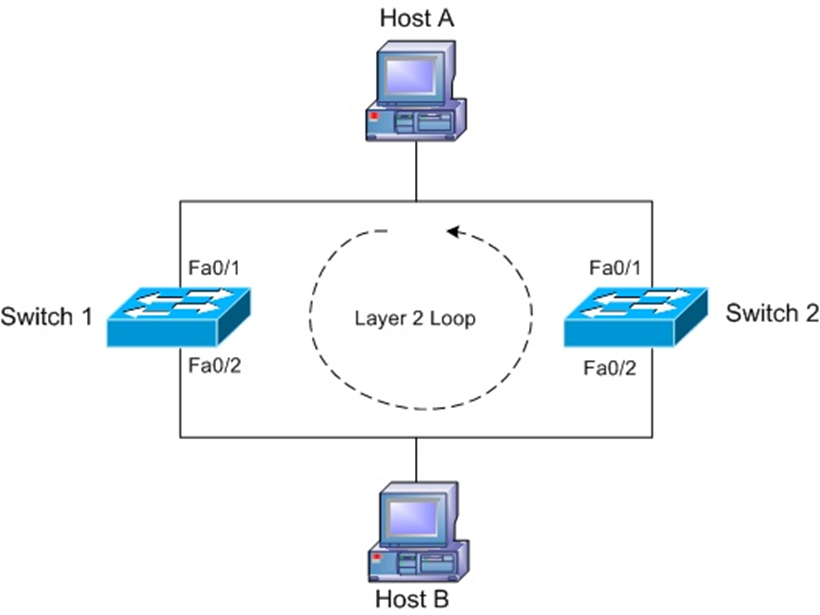
From above diagram Host A wants to communicates with host B. then it floods frame to both switch 1 and 2 with broad cast mac address FF:FF:FF:FF:FF:FF. Switch 1 receives on its fa0/1 and switch 2 on its 0/1 the broadcast frame gets received. Switch 1 floods the frame from its fa0/2 port and switch 2 does the same thing from its port fa0/2. Then both the switches receive the flooded frame on its port fa0/2. Switch 1 receives frame which was flood from switch 2 fa0/2. And switch 2 receives a frame on its fa0/2. This frame again flood from fa0/1 port of both the switches and the process is a never ending.
These loops are dangerous than routing loops, the reason why is routing packets has TTL (Time To Live) when the TTL reaches 0 the packets get dropped. Switch loops does not have any TTL. So, it makes the switches shuts down. Layer 2 loops are never ending and increases the network complexity because of its growth is exponentially rose. The CPUs has to process the frames in all the devices which may causes deplete their resources until the frames get removed from network.
STP calculations based on two key concepts:
Bridge id and path cost.
| Bandwidth | STP cost |
| 10 Mbps | 100 |
| 45Mbps | 39 |
| 100Mbps | 19 |
| 622Mbps | 6 |
| 1Gbps | 4 |
| 10Gbps | 2 |
Bridge id is an 8byte field of two subfields. 2 bytes are bridge priority subfield from 0 to 65535 value. Other 6 bytes are lower order MAC address which is in hexa-decimal format. 32768 is a default bridge priority value.
Switches assess their proximity to other switches using the notion of cost. In the original 802.1D standard, cost was specified as 1000Mbps divided by the link’s capacity in Mbps. For instance, a 10Mbps link would cost 100, while a Fast Ethernet link would cost 10. Lower STP costs are preferable. However, because the cost was simply stored as an integer value, an issue arose when higher bandwidth connections began to become more and more common. This option was deemed invalid because it would reduce the accuracy of the STP cost computations by applying a cost of 1 to all lines faster than 1Gbps. So that IEEE decided to modify the cost values as shown in above table.
To process the loop free STP logical topology, a four-step sequence is there.
a. lowest root BID
b. Lowest Path cost to Root Bridge
c. Lowest sender BID
d. Lowest Port ID
Switches use BPDUs (Bridge Protocol data Units) to convey STP information. Switches retain the best BPDU observed on each port after evaluating all BPDUs received on that port. Each BPDU that is received on a port is compared to the current BPDU saved for that port to see if it is more desirable by following the four-step process.
When a switch port becomes active, it starts sending BPDU frames for every 2 seconds. If a port hears a BPDU from another switch which is lowest STP value. It stops sending BPDUs. If it does not receive any BPDU packets with in a period of 20 seconds, the local port becomes active.
STP initial convergence process:
1. Root bridge election
2. Root ports election
3. Designated ports election
[1]
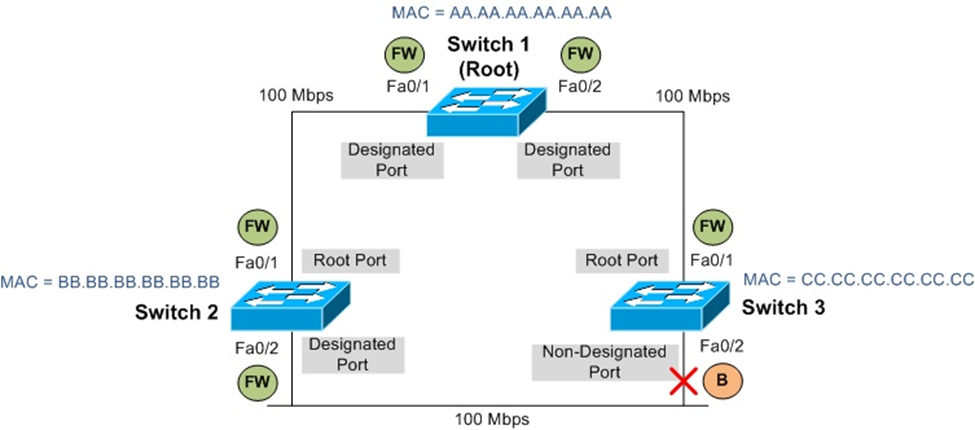
In above diagram switch 1 has lowest bridge ID of32768 and AA.AA.AA.AA.AA.AA and is elected as root bridge because of its lowest mac address ( assuming all the switches have same BID=32768 default).
Switch 1 has lowest BID and elected as root bridge. Both switches 2 and 3 have a cost of 19 for fast ethernet ports. Switch 2 has lower MAC address becomes f0/2 is root port and f0/2 for switch 3 became non designated port.
STP ports has 4 port states:
| State | Purpose |
| Forwaeding | Sending/receiving data |
| Learning | Building bridge table |
| Listening | Building active topology |
| Blocking | Receives BPDUs only |
| Disabled | Administratively down |
References
| [1] | “HOWTONETWORK,” [Online]. Available: https://www.howtonetwork.com/comptia-network-study-guide-free/routing-protocols-and-switching/. |
