Before learning network security, let us learn about security in general, then we will learn network security, CIA confidentiality integrity and availability which is basically the goal of network security, some of the controls which are needed for network security, then we will learn network security need why it is important in today’s world and will investigate cybercrimes by industry and country.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
Security in general
Security is about protection of assets. An asset is any resource owned by the business or person that have an economic value, if there is an economic value tide to the asset it makes perfect sense to take prevention, detection and reaction measures so we can safeguard the asset. For example, prevention prevents your asset from being damaged or stolen by installing locks at doors, window bars, securing the walls around the property or potentially hiring a security guard. Detection detects when, how, and by whom an asset has been damaged or stolen by installing burglar alarms or security cameras. Reaction helps you react so you can recover your assets by calling the police, making an insurance claim, or replacing the stolen items.
For general support issues of home users please visit: https://www.computerepaironsite.com.au/
Network Security
These are basically set of rules and configurations designed to protect the integrity, confidentiality, and availability of computer networks and data using both software and hardware technologies. Basically, network security combines multiple layers of defences at the edge of the network and within internal network, so only authorised users gain access to the network resources, but malicious actors are blocked from carrying out exploits and threats. The goal of network security is to protect the integrity, confidentiality, and availability of computer networks.
For Network Security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
CIA
Confidentiality means that only authorised individual can view sensitive or classified information and unauthorised individual should not have access to the confidential information. Integrity means that changes made to the data are done by only authorised engineers and corruption of data is failure to maintain data integrity. Availability on the other end ensures that the system work promptly, and service is not denied to authorised users. For example, if the network or data is not available to authorised user perhaps because of denial-of-service attack or maybe because of general network failure that impact may be significant to companies and user who rely on network as a business tool. There are many layers to consider when addressing network security across an organisation and attacks can happen at any layer in the network security layer model so it’s crucial that the network security architecture should be designed in a way that it should address each area.
Controls of Network Security
For cloud-based solutions for the businesses like Google, AWS, and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/
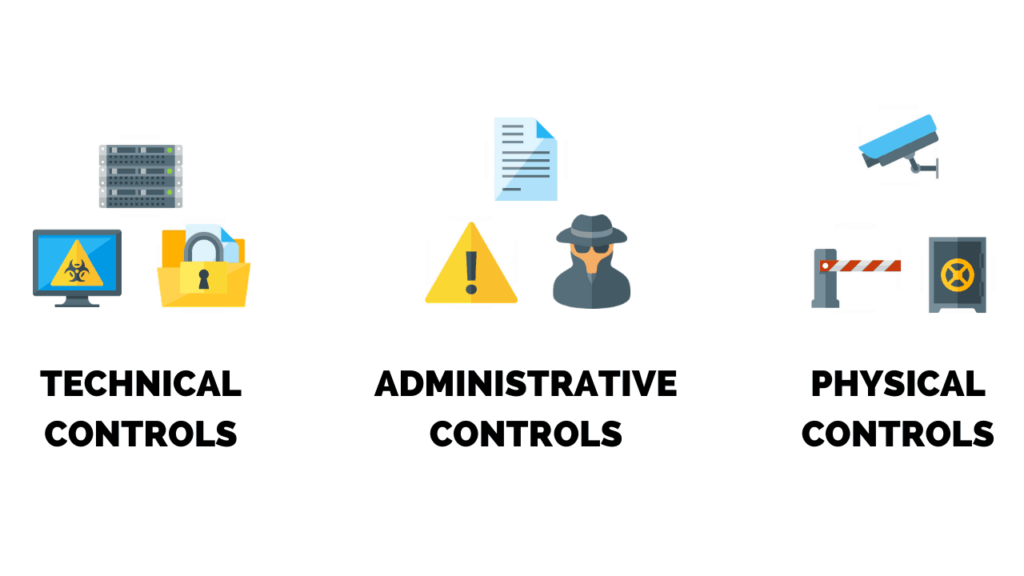
Network security typically consist of three different controls physical, technical, and administrative Physical network security basically it’s designed to prevent unauthorised personnel from gaining physical access to network components such network cabinets, routers, switches, firewalls within those cabins so controlled access such as logs biometric authentication and other devices is essential in any organisation. Technical network security control protects data that is stored on the network also known as data at rest or which is in transit also known as data in an out of the network. The protection is twofold here, first of all the security administrator needs to make sure that it protects the data or system from unauthorised personnel and also protect against the malicious activities from internal employees and lastly administrative network security, it consists of security policies and processes that control the user behaviour including how the user is getting authenticated to the network, their level of access on the network, and how IT staff member implement changes to the infrastructure. We need network security because there is no privacy on the Internet and Internet has made information available for everyone. For an organisation to protect its confidential information, network security is needed.
Digitalization has transformed our work how we live, work, play, and learn all have changed. Every organisation that wants to deliver the services that customers and employees demand must protect its network and ultimately protecting its reputation. According to one statistics report there will be close to 6 billion Internet users by 2022 and the other most important thing to consider is the increasing amount of large scale well publicised security breaches which are going up every year. In 2016 three billion yahoo accounts were hacked in one of the biggest breaches of all time. In 2016 again Uber reported that hacker stole the information of over 57 million riders and driver. In 2017 412 million user accounts were stolen from Friend Finder sites and in 2017 again 147.9 million consumers were affected by Equifax breach. If we see the average general cost of cybercrime by country, you can see that from last year in 2018 is the number of cybercrimes is just increasing. In United States it’s been increased by 29%. There are multiple types through which we can implement network security and here will be discussing just few of them.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
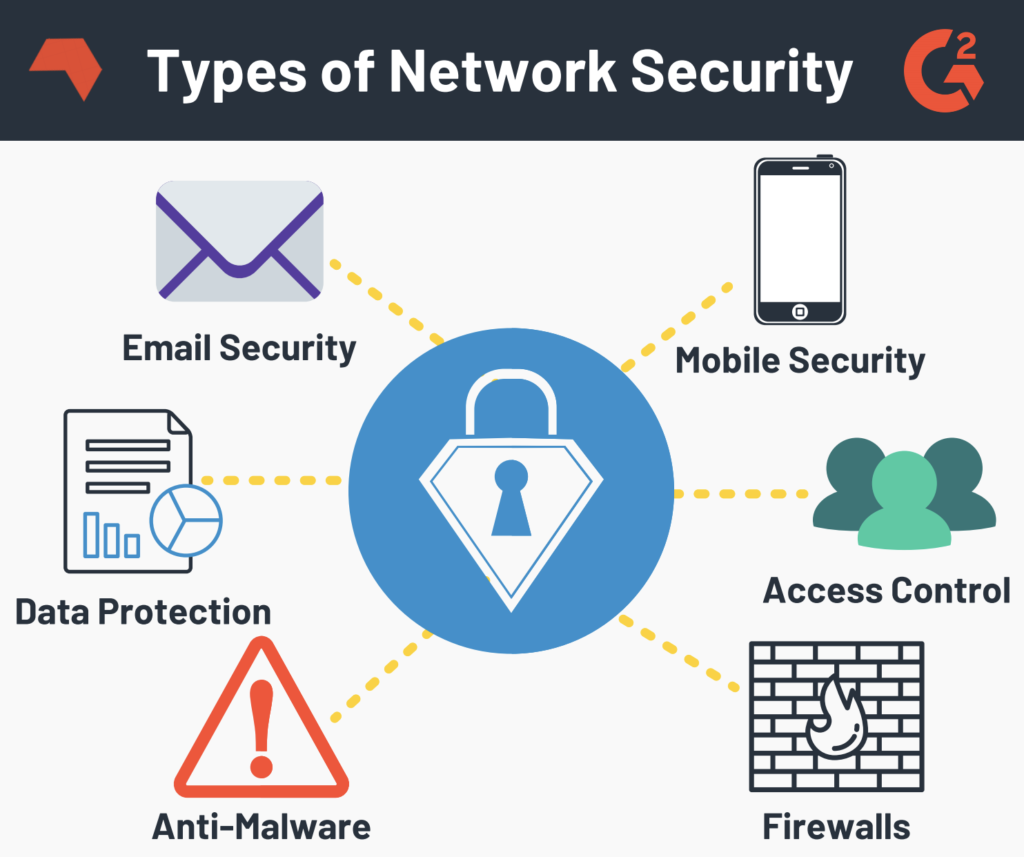
Types of Network Security
Starting with network access control and network access control of appliance let authorised users and devices connect to the network, and they keep out potential attackers. In an appliance administrator, they need to recognise each user and each authorised device so then an enforcement through policies can be applied based on their level of access. Antivirus and anti-malware software, malware short for malicious software which include viruses, worms, trojan ransomware, and spywares. Sometimes malware infect in network but lie dormant for days or even weeks, so the job of the security administrator to select a software that not only select the malware on entry but also continuously track file afterwards. Firewalls put up a barrier between trusted internal network and untrusted outside network such as Internet. In a firewall administrator they basically define rule which traffic is allowed to get into the network in which traffic is blocked. A firewall can be a hardware appliance, software or they both based on the need in the network. VPN, a virtual private network encrypts the connection from an end point to a network often over the Internet typically our remote access VPN uses IP sack or secure socket layer to authenticate communication between device and network. SIEM stands for security information and event management SIEM products pull together the information that infosec department needs to identify and respond to threats. These devices come in various forms including physical or virtual appliance and wireless security, so wireless networks are not as secure as wired one and without strong security measures installing a wireless LAN can be as like putting an Ethernet board everywhere so it’s crucial to select the right encryption and authentication type when deploying wireless within the organisation.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au