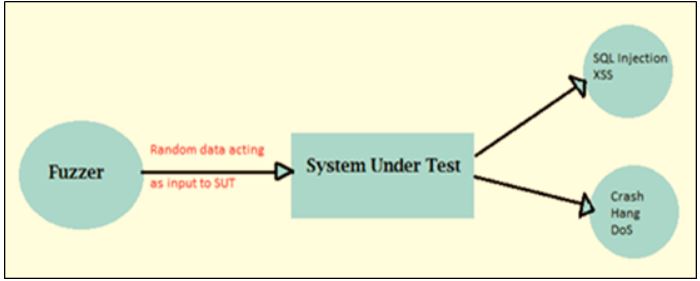
First of all we need to what is AI fuzzing?
AI fuzzing is the main element in examining operations or organizations for weaknesses. Fuzzing is an automatic examining approach that utilizes unanticipated or worthless data to see or explain how an organization breaks.
Fuzzing is out in the market for quite a time now; it is hard to do and did not get much attention from the companies. Adding AI in it, it promises to make this tool more adjustable and straightforward to utilize.
There is both an advantage and disadvantage of using AI fuzzing. The advantage is that the companies and groupware sellers have it easy and less time-consuming in searching possibly applicable vulnerabilities in their organizations so they can mend or repair them before the hacker or cyber criminals reach them.
The disadvantage is that the cybercriminals then have the key to enter this machinery and start searching for the zero-day vulnerabilities on a considerable scale.
How AI fuzzing works?
In traditional fuzzing, one gives rise to many instructions intending to break down and consider that every function has a different method and process to receive or take the instructions, which sometimes end up needing a lot of physical startups. You cannot just attempt every imaginable input to see or examine how the system reacts, which will take a very long time. Practically putting every application is more compound, so fuzzers make an effort to do it aimlessly and apply different methods to make an effort for the most possibilities. Fuzzing technology is not new, but it has never been used outside the academic community.
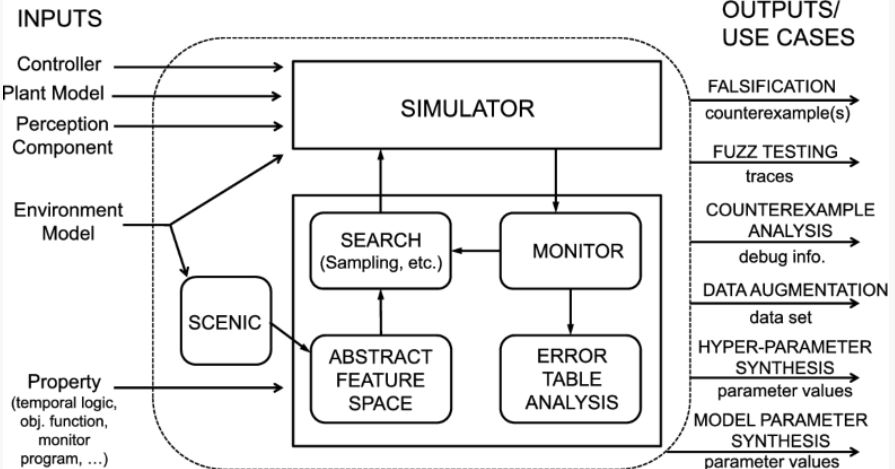
What are the tools of AI Fuzzing?
Companies are presenting fuzzing as a facility making the technology easy to install.
The top AI fuzzing tools include.
* Microsoft Security risk detection.
* Google’s cluster fuzz.
* Defensics Fuzz Testing by the synopsis.
* Peach fuzzer by Peach Tech.
* Fuzzbuzz.
What are the benefits of AI fuzzing?
Criminal mentality continues to develop, which increases the requirement of security testing tools. If companies need to be ahead of the cyber hacker, they need to promote a cyber-security master plan which encourages fuzzing at every phase of making or developing software. Here are five benefits of including fuzzing to the intelligence trial toolbox.
* A cost-effective security test:
AI fuzzing testing method is not costly than the other security testing method, which makes it preferably suitable for the businessman with a limited budget.
* Guards against zero-day vulnerabilities:
Zero-day vulnerabilities are like a bad dream of every chief information security officer (CISO). Never the less when an organization’s black box testing is accomplished, fuzzing then help you lower the chance of zero-day vulnerabilities.
* Discovers coding errors at the early stage of your software development life cycle (SDLC):
As we apply fuzz testing in different phases of SDLC, we will find the input mistake in the early stage, i.e., during the growth or quality verification stage, which will cost less than finding the error in the production stage.
* Improves security testing results:
Although fuzz testing is not complete security examining solution, when install or used as part of the black box protection examining strategy, it will boost the ending result of security testing.
* Ensures that all potential security vulnerabilities are explored:
The idea of fuzzing works so that all possible loopholes are inspected and tested and found unknown weaknesses.
How are hackers using AI fuzzing?
It is generally discussed how AI Fuzzing is excellent and valuable in companies to lower their cybersecurity risk, but it is very little thought that it is beneficial for hackers. Cybercriminals use AI to develop the system through which they can continue or carry on their illegal works very swiftly.
Cybercriminals can use AI for two stages, i.e., for exploration and exploitation.
Initially, hackers scan and examine the functions of the system, which is a target. After designing that specific system, cybercriminals then started to intentionally attack the program, show it with data, start to view and examine the result, and use AI to recognize the target’s weaknesses. By doing this method, cybercriminals can find more zero-day vulnerability and can damage or break them again and again.
Hope the readers would have more clarity after reading this piece. Any comments or suggestions are welcome as we strive to make technology easier for everyone.