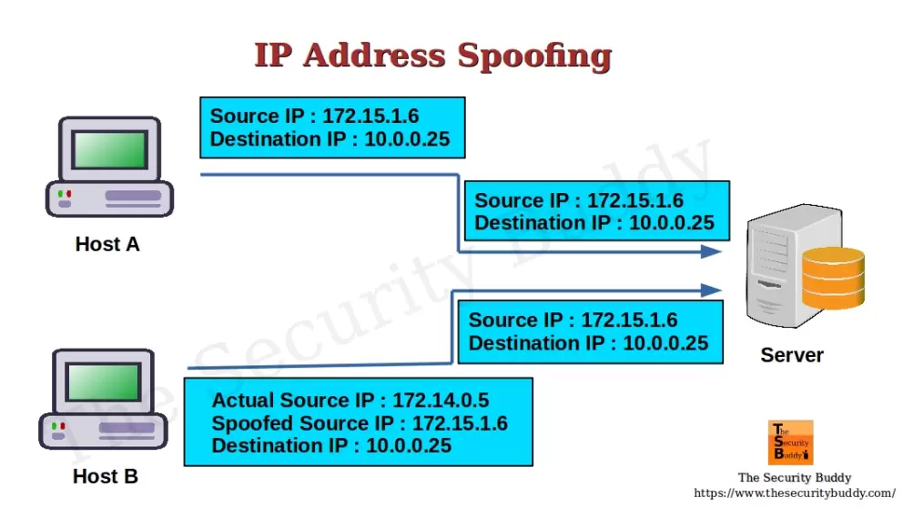
What is IP Spoofing
A hostile attack hides the IP packets’ natural source, known as Internet Protocol (IP) spoofing, which makes it challenging to pinpoint their point of origin. The attacker creates packets while altering the sending IP address to imitate a different computer system, hide the sender’s identity, or both. The header of the spoofed packet has a source IP address field that has a different address from the actual source IP address.
Figure1: https://www.thesecuritybuddy.com/dos-ddos-prevention/how-does-ip-spoofing-work/
How does this work
Delivering data over the internet involves splitting the data into several packets, which are then transmitted separately and concatenated at the other end. Each packet’s IP (Internet Protocol) header contains two pieces of data: the IP addresses of the source and the destination. IP spoofing use tools to alter the source address in the packet header to deceive the receiving computer system into thinking the packet originates from a trustworthy source, such as a different machine on a reliable network, and convince it to accept it. Because this takes place at the network level, there are no apparent signs of meddling.
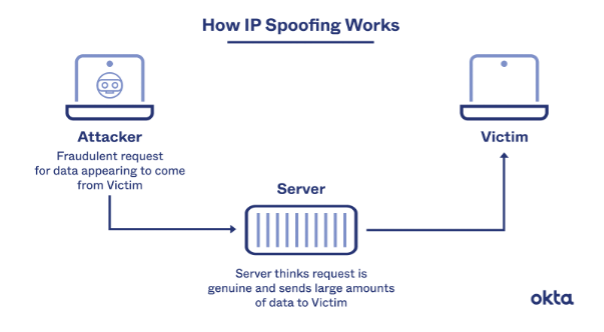
Figure 2: https://www.okta.com/uk/identity-101/ip-spoofing/
Types of IP Spoofing
• Man-in-the-middle attacks
Man-in-the-middle attacks are another malevolent IP Spoofing strategy that hinders communication between two computers. It changes the packet and transfers without the sender or recipient knowing. If an attacker gets into someone’s computer using a spoofed IP Address, the attacker can access all the information stored in the computer.
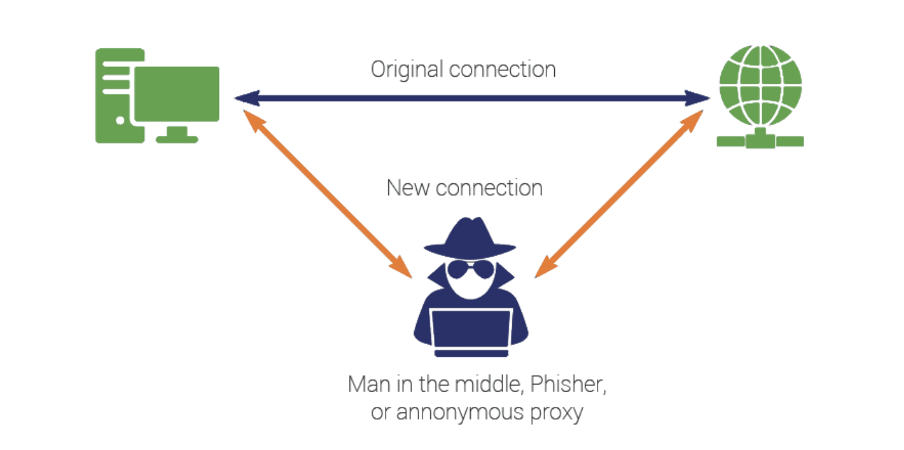
Figure 3: – https://www.thesslstore.com/blog/man-in-the-middle-attack-2/
• Masking botnet devices
Botnets that hide their presence can access computers by using IP spoofing. A group of computers that hackers manage from a single location is known as a botnet. Each machine runs a dedicated bot that commits evil deeds for the attacker’s benefit. IP spoofing enables the attacker to conceal the botnet because each bot in the network has a fake IP address, making it difficult to track the malicious performer. By doing this, an assault will last longer to reap more benefits.
A hostile person will initially try DNS spoofing to gain access to a network. In spoofing, a malicious actor can change the domain name is an IP address in the DNS. It may launch various further attacks from here, but a malware infection is a standard option. It is simple to infect another computer since it effectively redirects traffic from trustworthy sites to malicious ones without being noticed. From there, other machines will contract the virus and develop the botnet, effectively executing the DDoS assault.
After DNS spoofing, an attacker will employ several IP address spoofing strategies to hide the specific malware within the network better. After a continual randomization process, this commonly occurs. Because of this, the Internet protocol only stays steady for a short time, making identification and monitoring difficult.
This attack on the network level is undetectable to an end user. It is an intelligent way to carry out malicious assaults without being discovered.
• Distributed Denial of Service (DDoS) attacks
Hackers employ fake IP addresses to flood computer servers with data packets during a DDoS attack. With their identities hidden, they can use this to stealthily slow down or break a network or website that receives a lot of internet traffic.
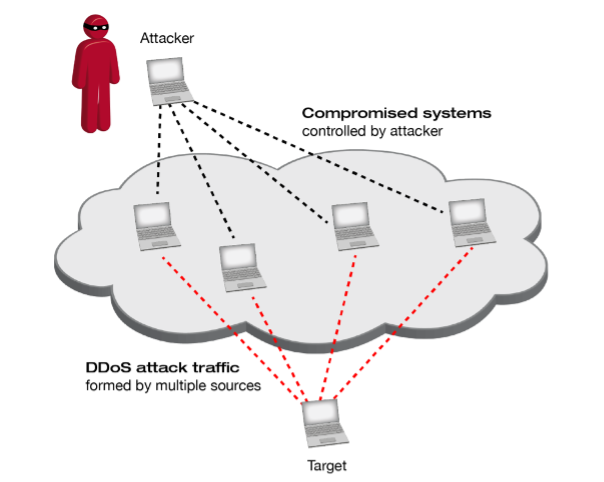
Figure 4:https://www.xantaro.net/en/tech-blogs/complexity-of-multi-vector-ddos-threats/
There are several strategies to lessen the consequences.
These contain a variety of interconnected spoofing attacks and techniques that combine to make up the overall attack.
A hostile person will initially try DNS spoofing to gain access to a network. In spoofing, a malicious actor can change the domain name is an IP address in the DNS. It may launch various further attacks from here, but a malware infection is a standard option. It is simple to infect another computer since it effectively redirects traffic from trustworthy sites to malicious ones without being noticed. From there, other machines will contract the virus and develop the botnet, effectively executing the DDoS assault.
After DNS spoofing, an attacker will employ several IP address spoofing strategies to hide the specific malware within the network better. After a continual randomization process, this commonly occurs. Because of this, the Internet protocol only stays steady for a short time, making identification and monitoring difficult.
This attack on the network level is undetectable to an end user. It is an intelligent way to carry out malicious assaults without being discovered.
Toxicology ARP
ARP spoofing sometimes referred to as “poisoning,” is another method for starting DDoS attacks. It launches an attack using IP spoofing and masking botnets, which is far more complex than brute force alone.
To change the pre-set IP addresses in a MAC table, what will send malicious ARP data packets to a LAN during an assault? It is a straightforward method for attackers to access several machines at once. ARP poisoning attempts to direct all network traffic via a compromised system. Attackers can deploy a DDoS or a MITM assault to do this quickly using their computer (Machine- in –middle).
To detect IP Spoofing, we can use network monitoring tools to Analyse the traffic and filter packets. Usually, these packets include in routers and firewalls to distinguish irregularities between the packet IP address and desired IP Address point by point on getting to control records (ACLs)
People can pay much more attention to the emails and text messages they receive to prevent getting attacked. For instance, an email spoofing phishing attempt can utilize strange syntax, misspelled words, or odd phrasing. These messages seem urgent, frighten people, and instruct people to act quickly.
If people pay attention to those, they also can see that the URLs included in the messages are slightly different than they should be or that the sender’s email address is wrong by one letter. They can notice these and decide whether these links are clickable or not. Make sure to click on what we can trust.
What are the things that end users can do to prevent IP Spoofing?
Always try to use a high-quality anti-virus to protect from online threats and keep that software up to date.
Make sure to use websites that start the URL with HTTPS. Because some websites do not have an SSL certificate, and their URL starts with HTTP. Always check the lock icon in the browser before entering a website.
Set up home Wi-Fi securely. Some people leave the default password and username for a long time for their router instead of changing the password to something complex, which is risky when thinking about the results.
Maintain a strategic distance from carrying out exchanges on unsecured public Wi-Fi.
Always be aware of phishing emails. These emails contain links and mostly ask to update passwords or bank details. So, avoiding clicking these links can prevent everyone from getting hacked.
Try to use IPv6 (Internet Protocol version 6) than IPv4 (Internet Protocol version 4). In that it offers the unique IP addresses required for Internet-enabled devices to interact, it works similarly to IPv4 but is more secure than IPv4.