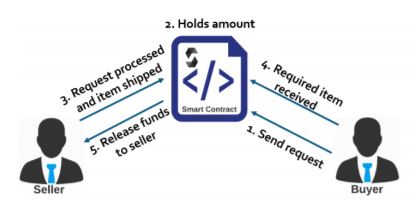
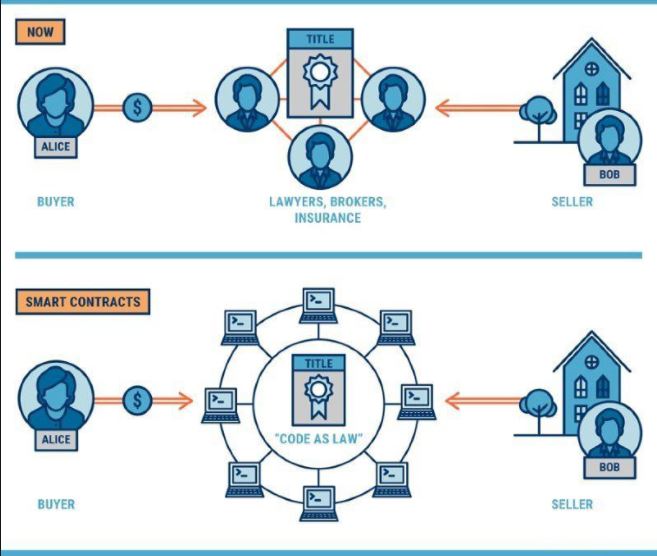
A smart contract is an accord among two people in the shape of computer code. They work on the cryptographic ledger, so they are saved on a public database or data set and cannot be modified. The dealings that occur in a smart contract are defined by the blockchain, which means that the transactions are done directly but not with a third party’s involvement. The deal only took place when the terms in the agreement are made. Dealing took place automatically, so there is no need for a third party, hence no trust issue.
It is a way to operate the business transaction to ensure that they are secured, precise, speedy, and cheap, all without the interference of a third party such as a bank. The pros of smart contracts are that they are detectable, apparent, and irreparable.
How does it affect?
The smart contract has its benefits, but there are some safety matters immanent to the procedure. Smart contracts depend on the blockchain, which supplies data keeping for the cryptocurrency platforms or bitcoin network. Smart contracts reside in suburbanized blockchain web, which means that information safety depends on the agreement enforced to keep it safe.
Ethereum, the second-largest cryptocurrency base, has over 32000 smart contracts with poor coding, making them vulnerable to hacking.
According to the researchers, one in every twenty smart contracts is at risk and vulnerable to hacking. Three types of smart contracts are especially and highly vulnerable: “greedy, prodigal, and suicidal” contracts. These smart contracts either lock or seal the funds considerably, disclose them to random customers or be liable or sensitive to be destroyed by any customer or buyer.
Prodigal Contracts:
When it comes under attack, the owners get refunded quite often due to contracts, whether it is lotteries or bounties. Whenever Ether was sent to the contract’s random address and that random address is not the owner or never invested in the contract and never given any specific information or data to the third party. We count it as a weakness and call it prodigal.
Greedy Contracts:
Greedy contracts are those contracts that remain active and hold the Ether and permit it to be accessible under no circumstances.
For example, in Parity contracts, several other multi-sig wallets have Ether, were found using a few of the functions provided by the Parity library contract to free finances to their users. Once the parity contracts were finished, the wallet contracts could not use the library and become greedy. This whole scenario resulted in $200M US worth of Ether.
Suicidal Contract:
A contract often allows a security fallback choice of being wiped out by its holder or the contracts any other trusted buyer in a crisis, like when the Ether is unloading or clearing out from contracts due to the attacks contract or system is crashing. When any joint account destroys the contract, the contract is then vulnerable, called suicidal.
Which three smart contract hacks are most famous?
Following are three of the major smart contract hack that you should know.
- The DAO hack:
The most famous smart contract hack of 2016 is the DAO hack. DAO – decentralized autonomous organization is an organization that works through guidelines encrypted as a computer application called smart contracts.
The DAO contains a sequence of smart contracts expected to regularize how Ethereum projects are financed. When notice or suspect the vulnerability, a cybercriminal or hacker thieves as much Ether as they want by manipulating the backup task in the code that was revealed to reentrancy. To retrieve the finances, the Ethereum data source had to be restored through a hard fork, leading to the formation of both Ethereum and Ethereum classic as two individual chains. - Parity’s Multi-signature Wallet Hack:
In 2017 Parity build a multi-signature wallet for the administration of Ether Bitcoin or decentralized money. These multi- signs wallets are connected to smart contracts provided on an unlock origin base that need more than one digital signature before the Ether connected with them can be authorized to transmit. - Parity User Triggered Wallet Freeze:
After the hack of the 2017 Parity smart contract, the bribery code was freeze accidentally soon after the hacking, making the multi-sign wallets incapable of transmitting any Ether saved. Researchers guessed that roughly about 45% of smart contracts written in Ethereum’s programming language, i.e., Solidity are unsafe or open for the cybercriminals for hacking.
Hope the readers would have more clarity after reading this piece. Any comments or suggestions are welcome as we strive to make technology easier for everyone.