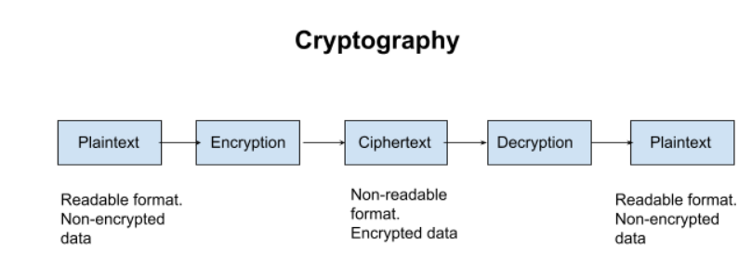
What is Cryptography?
Encryption is the art of encrypting data and communications so that only the intended audience can read and understand them.
In computer science, the term “cryptography” refers to secure information and communication methods that use mathematical principles and rule-based computing systems or “algorithms” to modify messages in ways that are difficult to read. These predefined algorithms create encryption keys, digital signatures, online web browsing, and private communications such as email and credit card transactions.
Security Terms
Encryption: Information is locked up using cryptography in the process of encryption. This method of locking information encrypts the data.
Decryption: The technique of utilizing cryptographic methods to decrypt the information.
Key: A password-like secret used to encrypt and decrypt data in cryptography, a few different key types are employed.
Steganography: It is the science of concealing information from prying eyes. Steganography differs from encryption in that potential prying eyes might not even be aware that any information is being hidden.
Cryptography techniques
Cryptology, cryptanalysis, and cryptography are all closely linked fields of study. It covers methods for hiding the data in storage or transit, such as microdots, word-image fusion, and various ways to combine words and images. However, in today’s computer-centered society, cryptography is most frequently connected to converting plaintext (standard text, also known as cleartext) into ciphertext and then back again (known as decryption). The professionals in this subject are referred to as cryptographers.
Cryptographic Algorithms
Cryptographic algorithms encrypt messages to encrypted messaging between computer systems, devices, and applications, and cryptosystems use a collection of techniques known as cryptographic algorithms or ciphers.
Cipher suites use three algorithms:
One for encryption, one for message authentication, and one for key exchange. This procedure is performed using protocols built into the software and executed by networked computer systems and operating systems (OS). It includes the following steps:
Key exchange enables digital signature and validation of messages using public and private keys for data encryption and decryption.
Single-key or Symmetric key encryption
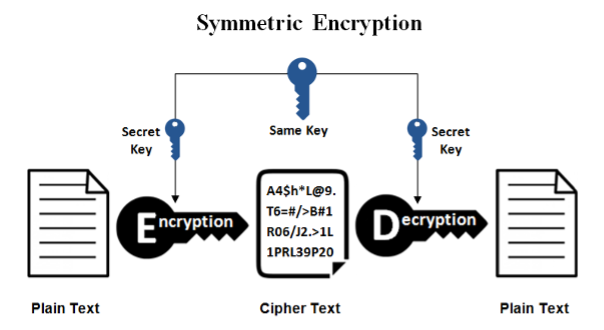
In single-key or symmetric-key cryptography, the originator/sender encrypts data, and the recipient uses a private key to decrypt the data to generate a fixed-bit-length block cipher. Increase. Advanced Encryption Standard is a variant of Symmetric Key Encryption (AES). The NIST named the US National Institute of Standards and Technology, published the AES specification in November 2001 as FIPS 197, which is considered Federal Information Processing Standard for protecting sensitive data. This standard is widely used by businesses and is mandated by the US government.
The US government granted AES permission to use classified information in June 2003. It is a specification that is freely used in hardware and software worldwide. AES has replaced the Data Encryption Standard (DES) and DES3. Use more considerable key lengths (128-bit, 192-bit, and 256-bit) to avoid brute force attacks and other attacks.
Public key or asymmetric key encryption
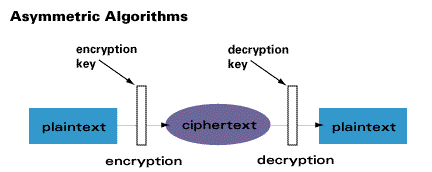
Public-key or asymmetric-key cryptography uses two keys:
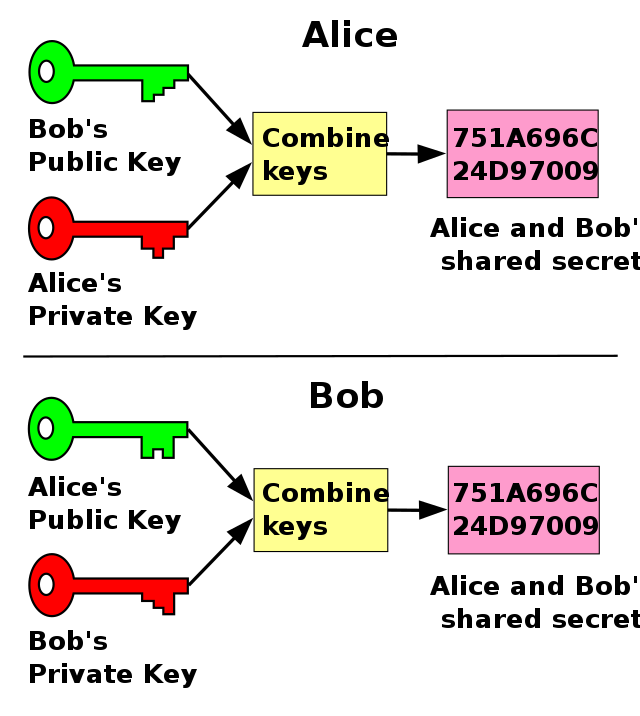
A public key is associated with the originator or recipient for encrypting a message. A private key is known only to the sender to decrypt the message (until revealed or chosen to share). Public key cryptography uses an example like this:
The Digital Signature Algorithm (DSA), recognized by NIST as a federal data processing standard for digital signatures in FIPS 186-4, is used in Bitcoin and is the Elliptic Curve Digital Signature Algorithm (ECDSA) widely used on the Internet. Is.
Diffie-Hellman key exchange
To preserve data integrity in cryptography, data is mapped to a defined data size using a hash function (SHA) that produces deterministic output from input values. For example, SHA-1, SHA-2, and SHA-3 are secure hash Algorithm 1, secure hash Algorithm 2, and secure hash Algorithm 3, respectively.
Benefits of encryption
Encryption is an essential tool for information security. We provide four of the most basic information security services.
Confidentiality – Encryption processes can protect data and communications from unauthorized access or disclosure. Credentials can be protected against spoofing and counterfeiting using cryptographic techniques such as MAC and digital signatures.
Data Integrity Cryptographic hash functions are essential for users to be confident of the correctness of their data.
Non-repudiation – Digital signatures provide a non-repudiation service, protecting against disputes arising from the sender’s refusal to deliver the message.
With the help of all these essential functions that cryptography offers, it is now possible to use computer systems to conduct business over networks effectively and efficiently.
Disadvantages of encryption
Cryptography does not protect against the dangers and vulnerabilities of the shoddy system, protocol, and method design. These require proper formatting and building a protective infrastructure that needs fixing.
Encryption is not free. Costs include both time and money.
Adding an encryption algorithm causes a delay in processing information.
Deploying public key cryptography requires building and maintaining significant public infrastructure. This requires a large financial investment. The computational complexity of a mathematical problem is the basis of the security of cryptographic procedures. Any mathematical solution or increased processing power to these problems could render the encryption scheme insecure.
The future of cryptography
- elliptic curve cryptography
Elliptic Curve Cryptography (ECC) was developed, but its strengths and weaknesses still need to be fully understood. Using ECC significantly reduces the time it takes to encrypt and decrypt, allowing you to send more data securely. However, ECC must also be tested and proven safe before governments, businesses, and individuals approve it.
2. Quantum computing
The latest trend is quantum computing. Quantum computers store data using a quantum superposition of multiple states, unlike modern computers, which use a binary format called a ‘bit’ that can keep ‘1’s or ‘0’s. A “qubit” or “qubit” stores many valuable states. This allows them to compute numbers orders of magnitude faster than traditional transistor processors.
Consider the 193-digit number RSA-640, which can be calculated by eighty 2.2GHz processors over five months, to understand the capability of a quantum computer. One quantum computer would calculate the number in less than 17 seconds. With a fully built quantum computer, calculations ordinarily take billions of years and may be completed in hours or even minutes.
In light of these realities, modern cryptography must search for computationally more challenging issues or develop new approaches to archive modern encryption’s current purposes.