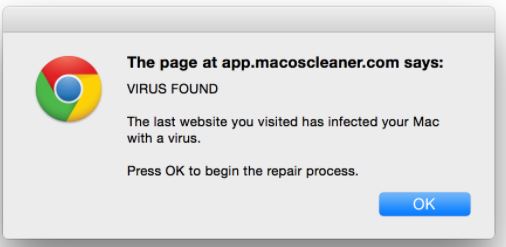
What is a web scripting virus?
Web scripting virus is spyware or Malware that can violate the security firewall of the web browser. However, unlike other viruses, this virus spread through webpages and ads as well. The feature that makes this more dangerous is that it can spread way faster than many other viruses such as a blaster, code-red, and others. The abbreviation of web scripting virus is WSV which will be used in this blog from time to time. As you can see the name of the virus, it is easy to tell where this virus lives, i.e., on the web page or portal. Anytime any website or page is open, the pop-up ads and infected web page ads are the most common reasons this virus usually spread. When these pop-up ads are open, this virus automatically enters your browser, skips the protective walls of your device, alters your storage, changes your browser page, steals personal data, and makes your device steady and slow-moving. This virus is actually of two types, i.e., persistent and non-persistent.
Persistent means that the person who wants to cross the security firewall, rob your cookies while making this attack, attackers can cause a real problem to the data and damage to your system by imitating.
The second one is non-persistent, which means that the strike takes place without the person’s knowledge as it runs in the background until it affects the user’s data ultimately.

What is a web scripting virus capable of?
The multiplication method of this virus is a system and grid breakability, which can cause harm and shoot spam emails and can cause damage to user’s data. It usually exists in numerous social platforms, communities, approved decision forums, and information boards. A WSV can grow on various devices very quickly and also very fast and rapidly. It usually uses a minor party JavaScript RSS feet to escalate itself. Furthermore, it also developed through the business chip, commercial sign, and added pop-up information. It also has the size to bring about online Malware and continue Distributed Denial of Service (DDOS) strike.
Moreover, it creates a lethal link that can quickly be sent to anyone as an attachment through the emails that WSV sent automatically. The most dangerous effect of this is that it makes your machine restarts automatically. While surfing, it can automatically redirect the searches to inappropriate websites. It can make changes to the setting of the user’s machine, i.e., the background and the color scheme, and it can at times remove the drivers and quickly affect the data and damage the windows.
How to protect your device from web scripting viruses?
This virus typically activates from the activity or working of the user or the person running the device, i.e., by opening junk and encrypted appended files, dwelling damaged web pages, and clicking on virus-containing corrupt promotional ads, etc.
Does the main course of action to guard your gadget is to backup and ensure some sterility rules, which are as follows:
- Be very careful when using or working in highly unsafe cyberspace.
- You do not have to check or open every email sent by obscure, doubtful, and skeptical references.
- Keep away from dwelling minor party, forum, or web pages.
- Only operate certified and authorized web pages for uploading any program or groupware.
- Avoid or prohibit going over to watch any extra commercial that appears on your search engine.
Besides, specialists in safety and reliability also advise the utilization of reliable security software that can go through your system to search for any dangerous virus and guarantee the complete protection of the system. In addition to this software, they also search any unauthorized or contaminated sites which stop you from going and opening the side by assuring immediate protection to the system.
There is also another possibility to avoid endangering the device by using well-organized ad blockers and good antivirus and anti-malware so that it can protect the system from any unwelcome and undesired commercials as keep compromised banners away from your web directory.