Networking devices are hardware devices that are used to connect, manage and control computer networks. They are used to facilitate communication between devices on a network, ensuring that data is transmitted reliably and securely. There are several types of networking devices, each with their unique functions and uses. In this article, we will explore some of the most common types of networking devices and their uses.
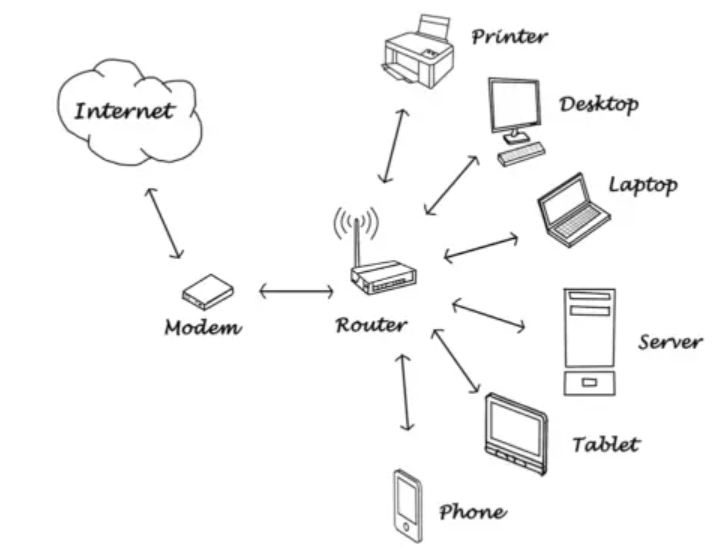
- Router
Routers were introduced in the late 1980s and early 1990s as a way to connect multiple LANs together into a wide area network (WAN). Routers were designed to provide intelligent routing of network traffic between different LANs and to provide security features such as access control and firewall capabilities. A router is a networking device that is used to connect multiple networks and direct traffic between them. It is responsible for directing data packets between networks based on their IP addresses. Routers can be used to connect devices on a LAN (Local Area Network) to the Internet, or to connect different LANs to create a WAN (Wide Area Network).
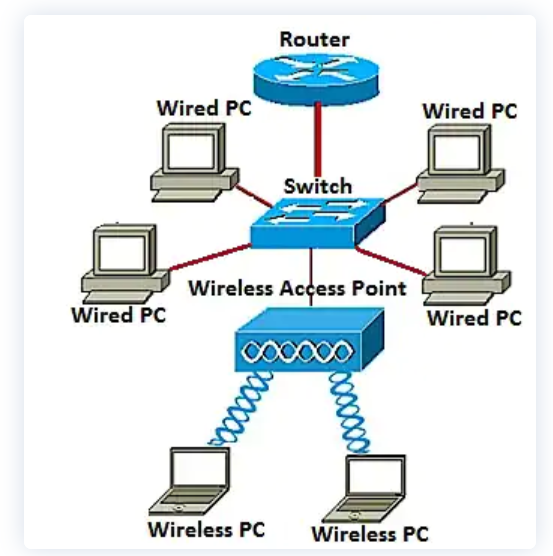
- Switch
Switches were introduced in the 1990s as an improvement over hubs. They allowed for higher bandwidth and provided the ability to segment network traffic. They were faster and more efficient than hubs and quickly became the standard for local area networks (LANs). A switch is a networking device that is used to connect devices on a LAN. It is responsible for directing traffic between devices on the same network. Switches work by creating a network of connections between devices, allowing them to communicate with each other directly.

- Hub
Hubs were one of the first networking devices and were widely used in the 1980s and 1990s. They were simple devices that connected multiple computers together in a network. However, they had limitations, such as low bandwidth and no ability to segment network traffic. A hub is a networking device that is used to connect devices on a LAN. It is similar to a switch in that it creates a network of connections between devices. However, unlike a switch, a hub broadcasts data to all devices connected to it, regardless of the intended recipient. This can lead to slower network speeds and decreased network security.

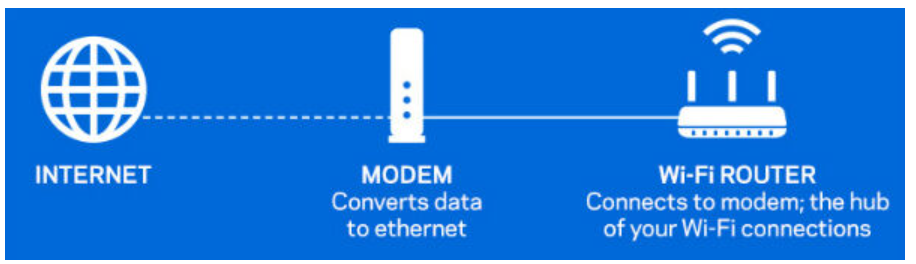
- Modem
A modem is a networking device that is used to connect a computer or other device to the Internet. It works by converting data from digital format to analog format and back again, allowing data to be transmitted over telephone or cable lines.
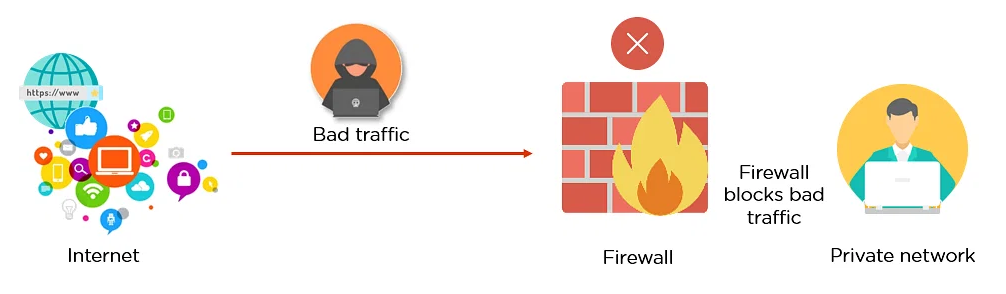
- Firewall
Firewalls were introduced in the mid-1990s as a way to provide network security. They were designed to filter network traffic and block unauthorized access to a network. Today, firewalls are an essential component of network security, and most networks use them to protect against cyber threats. A firewall is a networking device that is used to protect a network from unauthorized access. It works by monitoring incoming and outgoing network traffic and blocking any traffic that does not meet predetermined security criteria. Firewalls can be used to protect both wired and wireless networks.
- Access Point
Wireless access points (WAPs) were introduced in the early 2000s as a way to provide wireless connectivity to networks. They allow devices to connect to a network without the need for a physical cable. Today, WAPs are a standard part of most networks, and they provide fast, reliable wireless connectivity. An access point is a networking device that is used to create a wireless network. It works by broadcasting a wireless signal that allows devices to connect to the network without the need for cables. Access points are commonly used in public places such as airports, cafes, and hotels.
- Repeater
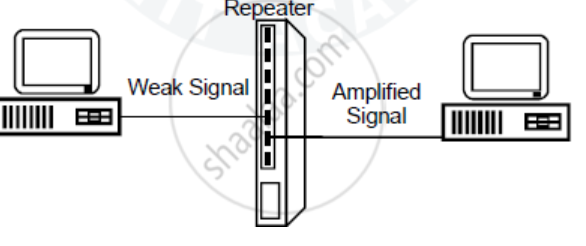
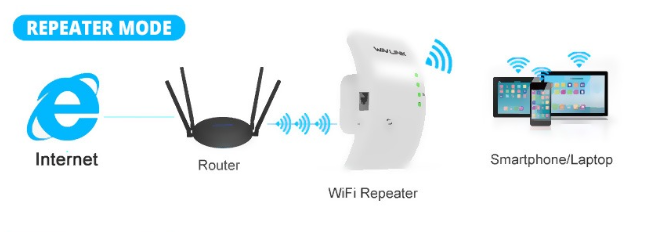
A repeater is a networking device that is used to extend the range of a wireless network. It works by amplifying the wireless signal, allowing it to reach devices that are located farther away from the access point. Repeaters are commonly used in large buildings or outdoor areas where the wireless signal may be weak.
Virtual Private Networks:
Virtual private networks (VPNs) were introduced in the 1990s as a way to provide secure remote access to a network. They allow remote users to connect to a network using an encrypted tunnel, providing a secure connection to the network. Today, VPNs are widely used in businesses of all sizes to provide secure remote access to their networks.
Conclusion
Networking devices are essential for creating and managing computer networks. Each device has its unique functions and uses, and understanding how they work is essential for building and maintaining a reliable and secure network. Whether you are setting up a home network or managing a large enterprise network, using the right networking devices is key to ensuring that your network runs smoothly and securely.
