In today’s digital world, social engineering attacks have become increasingly common. These attacks are a type of cybercrime that uses psychological manipulation to deceive users into divulging confidential information or performing actions that may result in the theft of their personal data. Social engineering attacks are a significant threat to individuals, businesses, and organizations worldwide. In this blog, we’ll explore what social engineering attacks are, how they work, and how to protect yourself from them.
What are Social Engineering Attacks?
Social engineering attacks are a type of cyber attack that uses deception to manipulate users into divulging sensitive information or performing actions that may lead to data theft. These attacks can take many forms, such as phishing, pretexting, baiting, and tailgating. Phishing attacks are the most common type of social engineering attack, where an attacker impersonates a legitimate organization or individual to trick the user into providing their personal information or clicking on a malicious link.
How do Social Engineering Attacks Work?
Social engineering attacks work by exploiting human emotions such as fear, curiosity, greed, and trust. The attacker may pose as a trusted individual or organization and trick the user into providing their personal information, such as login credentials, bank account details, or credit card numbers. The attacker may also use psychological tactics like urgency or fear to pressure the user into taking a particular action, such as clicking on a link or downloading an attachment.
Social engineering attacks can take many forms, but they all share a common goal: to trick the user into divulging sensitive information or performing actions that may lead to data theft. Attackers often use psychological tactics to manipulate their victims. Some common tactics include:
- Authority: The attacker may pose as someone with authority, such as a company executive or IT administrator, to gain the victim’s trust.
- Urgency: The attacker may create a sense of urgency, such as threatening to close the victim’s account or promising a reward for quick action.
- Fear: The attacker may create a sense of fear, such as threatening legal action or implying that the victim’s security has been compromised.
- Curiosity: The attacker may pique the victim’s curiosity, such as offering exclusive access to new information or media.
Some common types of social engineering attacks include:
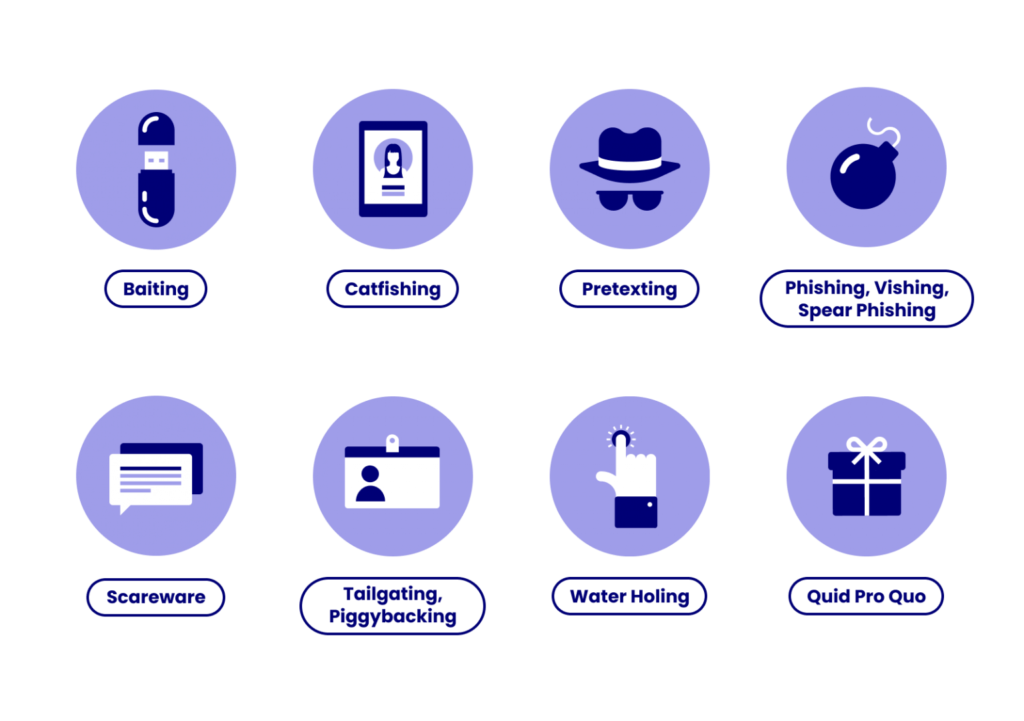
- Phishing: Attackers send emails that appear to be from a legitimate company or organization, often with a sense of urgency, and ask the recipient to provide sensitive information, such as login credentials or credit card information.
- Pretexting: Attackers create a false scenario to obtain sensitive information from the victim. For example, they may pose as a bank representative and request account information.
- Baiting: Attackers offer a tempting reward, such as a free movie download, in exchange for the victim’s personal information.
- Tailgating: Attackers follow the victim into a secure area, such as an office building, and gain access to sensitive information or systems.
Avoiding the Social Engineering Attacks
Here are some tips to help protect yourself from social engineering attacks:
- Be cautious of unsolicited emails, phone calls, or text messages. If an email or message seems too good to be true or creates a sense of urgency, it is likely a social engineering attack.
- Never share personal information like passwords, social security numbers, or bank account details with anyone online or over the phone.
- Verify the identity of the person or organization you’re interacting with. If you receive an email or message from a company you trust, verify the sender’s identity by calling the company’s customer service number.
- Use strong and unique passwords for all your accounts. Avoid using the same password across multiple accounts.
- Keep your software up to date with the latest security patches and updates.
- Use a reliable antivirus software that can detect and prevent social engineering attacks.
- Educate yourself and your employees about the different types of social engineering attacks and how to recognize them.
In conclusion, social engineering attacks are a significant threat to individuals and organizations worldwide. These attacks use psychological manipulation to deceive users into divulging sensitive information or performing actions that may lead to data theft. By being cautious and taking preventive measures like using strong passwords, verifying identities, and educating yourself about these attacks, you can protect yourself from social engineering attacks. Remember, prevention is the best defense against social engineering attacks.
