What is the polymorphic virus?
In old times, computer viruses had such a structure that antivirus software could be used to detect any other virus of such type in the computer once the actual virus is detected and treated by some antivirus. Nevertheless, nowadays, the viruses are so sharp that they could self-configure themselves and even have the capability of changing their functionality pattern and make it hard for antivirus to detect them. A polymorphic virus is a virus of such type. It is a destructive, intrusive, and harmful kind of Malware or bug that can “morph” or alter, causing it to be hard to find through antimalware software or program. The development of malicious and harmful code can happen in many ways, like changing the file’s name, file compression, and encoding with changeable keys. It is a bug that can change itself every time it runs without changing its actual function. To differentiate the makeup of its physical file in the course of every invasion, it encrypts the codes and utilizes other encryption keys each time. It is a very complex computer infector that influences data types and computer functions. It duplicates itself, upon infection, by making usable, although a bit modified, a clone of itself.
How is polymorphic code generated?
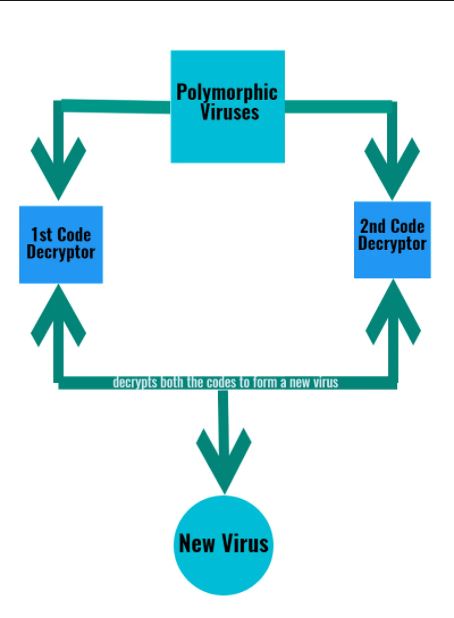
The polymorphic virus usually utilizes a mutation engine that contains basic malicious code. The basic code does not get altered by the mutation engine; instead, it creates a new decryption pattern for the virus or code. The polymorphic viruses file name could get changed by the mutation engine. Due to which the mutation engine creates a new decryption pattern.
How polymorphic virus works?
Polymorphic virus depends upon modification agent to change decryption procedures, each time they attack some device. Hence traditional and old security techniques cannot easily detect them; as for their working, they do not make use of static, unvarying code. The usage of complicated mutation engines that give rise to many decryption procedures makes this virus more difficult to find out. As with every “mutation,” the code appearance in polymorphic virus differs, but the primary function generally does not change; it remains as it is. For instance, spyware software is supposed to work as a key logger that will keep performing the task or function even if the program’s signature is changed. If by chance the program is detected by some antivirus software or program and the virus’s signature is attached with a downloadable database, the antivirus program will be of no use and will not track the rogue and harmful code once the signature changes, just like that a brand-new spyware program has appeared. Hence, Trojan makers become more substantial than the security seller who used the same old traditional signature-based diagnosis to detect and block malicious code.
How polymorphic virus spreads?
This type of virus is generally spread through spam messages or emails, infected websites, or because of using other different Malware. AIRLOCK, BAGLE, URSNIF, UPolyx, and VOBFUS are the most discreditable and dangerous polymorphic viruses that currently exist. When collaborated with any other harmful or destructive routines, it can even be a higher risk to its sufferer. Research conducted in March of 2015 has a finding that when VIRLOCK combine with ransomware routines, it made it a great challenge to find out, treat and remove the virus.

How can polymorphic viruses be detected and removed?
Eliminating this virus needs programmers to rewrite language strands, which could be complicated, i.e., consuming and expensive. For detecting polymorphic virus, a substantial string noticing scanner is required, making it able to scan many different strings, having one for every possible and imaginable decryption scheme. It is necessary to remove this virus as it is a hazardous virus that can be applied widely.
How can we prevent this virus?
The most suitable way of defending this virus is to use numerous and varied layers of data and information security Criteria and measures like antimalware programs and risk detection. Such type of software must be kept active and current and must run often. If auto protects attributes are available, then they should be enabled.

