In today’s world, the security of information technology (IT) systems has become a major concern. As more and more sensitive information is stored electronically, the threat of theft or misuse of that data has increased. While many organizations focus on cybersecurity measures, physical security is often overlooked. Physical security refers to the protection of physical assets, such as equipment and data centers, from unauthorized access or damage. In this blog, we will discuss the importance of physical security measures in the information technology sector as well as discuss the benefits of implementing physical control measures in the information technology sector.
Importance of physical security measures
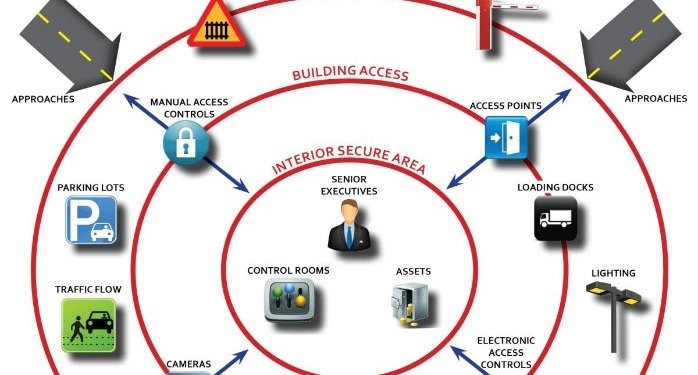
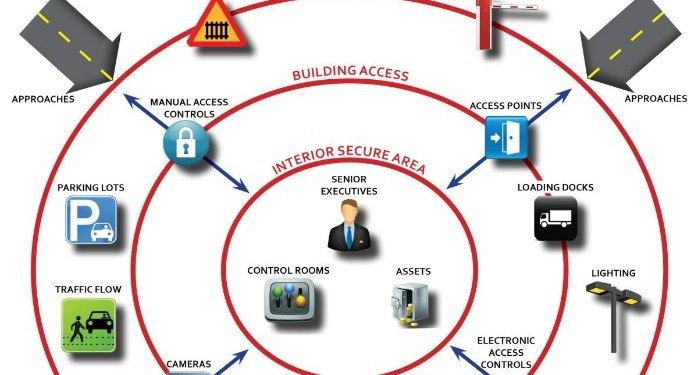
Access Control
Access control is the process of limiting access to a specific area or data center. Access control systems can include measures such as card readers, biometric scanners, or PIN codes. These systems ensure that only authorized personnel can access critical areas of the IT infrastructure. Access control also helps to prevent theft or damage to sensitive data.
Video Surveillance
Video surveillance is a crucial component of physical security in the IT sector. Cameras can be placed at key locations to monitor activity and deter theft or vandalism. Video surveillance can also provide evidence in the event of a security breach or theft.
Environmental Controls
Environmental controls refer to measures that ensure the physical environment of the IT infrastructure is optimal for the equipment. This can include measures such as temperature control, humidity control, and fire suppression systems. Proper environmental controls can help prevent equipment failure and data loss.
Backup Power
Backup power is essential in the event of a power outage. Uninterrupted power supplies (UPS) and generators can provide backup power to critical IT infrastructure, ensuring that operations continue uninterrupted.
Benefits
In today’s digital age, information technology (IT) systems are critical to the functioning of almost all industries. With the increase in the amount of sensitive data being stored electronically, the importance of protecting that data from theft, damage or unauthorized access has become paramount. While cybersecurity measures are essential to safeguarding the IT infrastructure, physical security measures are often overlooked. In this blog, we will discuss the benefits of implementing physical control measures in the information technology sector.
Protection against theft and unauthorized access
Physical security measures such as access control systems and video surveillance cameras help prevent theft and unauthorized access to critical areas of the IT infrastructure. These measures ensure that only authorized personnel can access sensitive data and equipment, thus reducing the risk of data breaches and theft.
Minimizes downtime and data loss
Environmental controls such as temperature and humidity control, and backup power systems such as UPS and generators, help ensure that the IT infrastructure remains operational even in adverse conditions. This minimizes downtime and the risk of data loss due to equipment failure or power outages.
Compliance with regulations
Many industries such as healthcare, finance, and government have strict regulations governing the protection of sensitive data. Implementing physical security measures such as access control and video surveillance can help organizations comply with these regulations and avoid costly penalties and reputational damage.
Enhanced employee safety
Physical security measures such as panic buttons, emergency exits, and fire suppression systems, help ensure employee safety in the event of a security breach, natural disaster, or other emergency situation.
Protection against natural disasters
Natural disasters such as floods, earthquakes, and hurricanes can cause extensive damage to IT infrastructure. Physical security measures such as environmental controls and backup power systems help protect against such disasters and reduce the risk of data loss and downtime.
Determining level of risk with Matrix
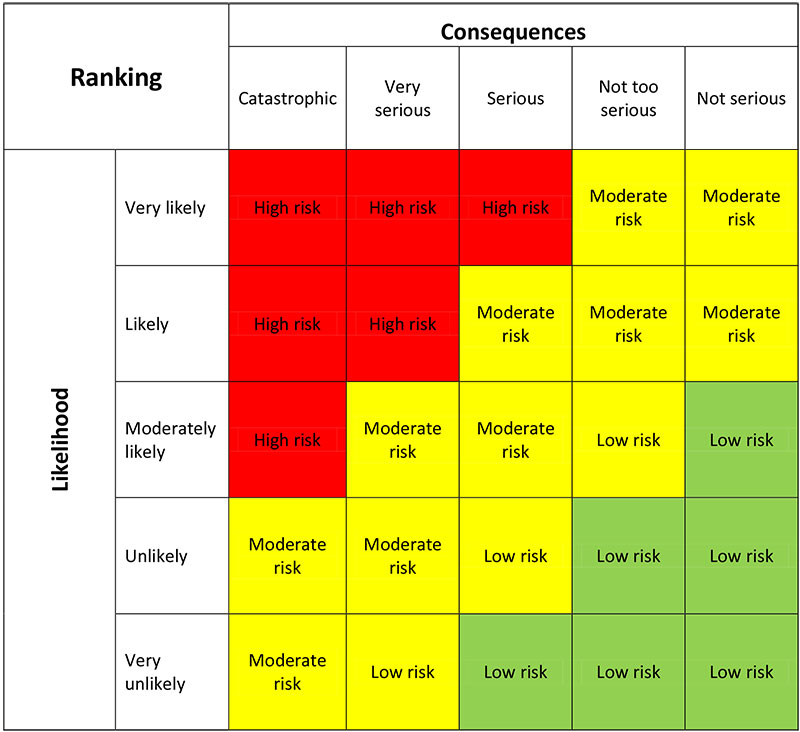
Level of security risk = Likelihood x Consequences
Conclusion
In conclusion, physical security measures are essential in the information technology sector. They help protect against theft, unauthorized access, downtime, and data loss, and ensure compliance with regulations. By implementing access control systems, video surveillance, environmental controls, backup power, and emergency response systems, organizations can significantly reduce the risk of security breaches and safeguard their critical IT infrastructure.