OSI model is basically a logical organisation. It tells us what are the different levels at which the data must travel from the client machine to the server machine at each level. What must be the input data and what must be the output data, let’s first see what client machine and server machine is, the machine that is sending a request is a client machine and the machine that is receiving that request is called the several machine. If there is node one and there is node two. If node one is sending a request to node two, so node one is the client machine and node two is the server machine. At any point of time, node one could become the client machine and node two could become the server machine. so OSI model is the physical and a logical organisation of the network. The network architecture takes care of how it must be implemented.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
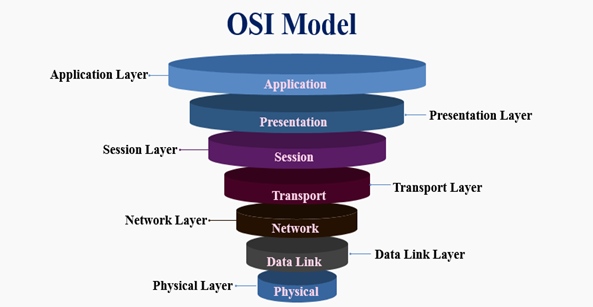
Let us see what the different layers of this OSI model are. There are seven layers, in the OSI model, they are physical layer, datalink layer, network layer, transport layer, session layer, presentation layer, and the application layer. Let us see how these layers are there at the client end and the server end.
Application layer
First and foremost is the application layer. In the application layer the client machine sends up a request on it wants to exchange some data, it can be a file, chat requests, sending or receiving of a video file, or multimedia file. The file as it is there at the application layer, the application layer decides that this can be done or cannot be done, and it sends this request or the file itself to the presentation layer.
For general support issues of home users please visit: https://www.computerepaironsite.com.au/
Presentation layer
The presentation layer is responsible for presenting that data in a form that is acceptable to the server machine, while the server machine has its own configuration, its own limitations of accepting a request, fulfilling a request. So, that must be taken care of by the presentation layer. The presentation layer then sends the file or the data to the session layer.
Session layer
The session layer is responsible for establishing a session. For example, the server machine is switched off, can we take that request? No, it cannot take that request. So, the session layer will decide whether the request can be fulfilled or not. If it can be fulfilled, then that session is established. That means, the server machine is ready to accept a request from the client machine. The session layer then will send it to the transport layer.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
Transport layer
Switching technique uses circuit switching or packet switching. In packet switching, the data is broken down into different smaller packets so that they can be sent over the network. Now in the OSI model, packet switching is used till the session layer. The file is in its own form, in the form that we want to send. At the transport layer, it will be broken down into smaller frames, smaller data packets that is what the transport layer will do.
Network layer
The network layer will break the data down into further smaller packets, adds the source address and the destination address. The network layer is also responsible for attaching a protocol to it so that it can travel to the next layer or the server machine. After the network layer, the data is sent to the data link layer.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
Datalink layer
The datalink layer has two functions. It will add a start and a stop lag at end of each datagram and the datalink layer will also check that in the way from application layer, presentation layer through network layer, there has not been any error in the message. If there has been any message error, then it will ask the upper layers to resend the file so that the correct file can be sent. After the data link layer, the data will come to the physical layer.
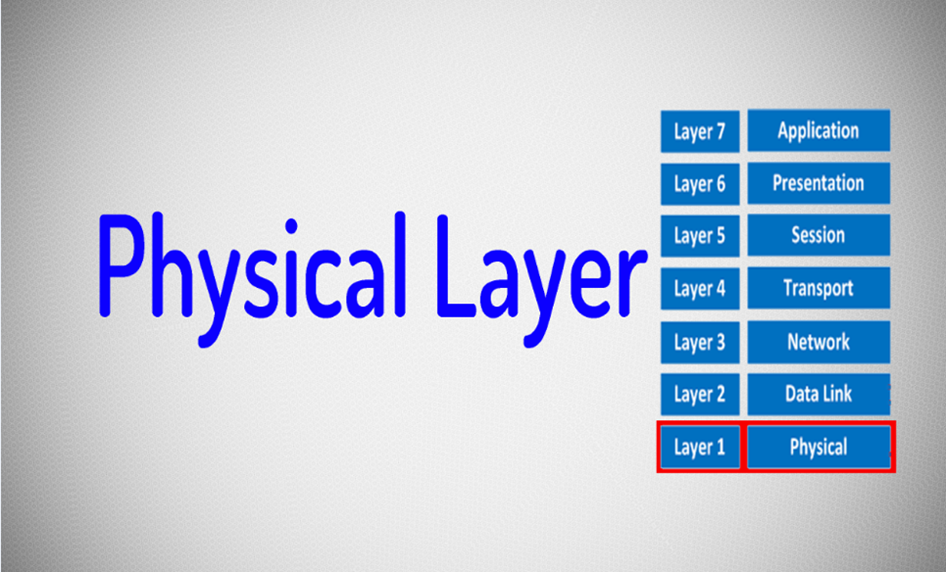
Physical layer
Physical layer is the actual layer where the actual transmission of data takes place through optical fibre cables, coaxial cables, radio waves, and infrared. Now the physical layer of the client machine data has started travelling, it will go to the physical layer of the server machine.
At the server end, the physical layer the data has reached in the form of bits and bytes. At the data link layer, something opposite will happen. At the client level data link layer was adding a start and a stop flag. Now data link layer of the server machine will take away those. At the network layer, they will be assembled because the client machine of the network layer was breaking it down so opposite was being done by the client machine levels and the server machine levels will be functioning. At transport layer, they will be assembled. Session layer, presentation layer exactly opposite to what was being done at the application layer. Finally, the whole file will come together in the form that was being sent by the client machine.
For cyber security related issues of businesses visit: https://www.benchmarkitservices.com/cyber-security/
This is how the server machine will accept the file, that it is not necessary for any network architecture to have all these layers. For example, if there is a Wi-Fi connection, the Wi-Fi connection will not need to have a network layer because network layer is concerned about the physical connection so that layer will not be required. The request is received by the application layer, the data proceeds to the lower layer after processing and breaking it down into datagrams or there are adding source destination addresses or there are adding start and stop flags. The data is transferred by the physical layer, the physical layer of the client machine sends it to the physical layer of the server machine. The data proceeds to the upper layer after processing, so client machine it has come down broken it will reach the server will be joined together and it will reach the final layer of the server machine. The request is shared with the workstation, this means that before the actual transmission can take place the session layer establishes that the server machine is ready to take that request.
For cloud-based solutions for the businesses like Google, AWS and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/