Title: Principles, Strategies, and Best Practices for Mastering Network Architecture and Design
Overview of Network Design and Architecture:
Strong, effective, and secure communication infrastructures are built using network architecture and design as a guide. We will delve into the complexities of network architecture, investigate the design principles that drive it, look at different network topologies, and provide best practices for building scalable and resilient networks in this comprehensive guide.
The Basics of Network Architecture:
Fundamentally, network architecture establishes the composition, arrangement, and structure of a network, guiding the management, routing, and transmission of data. Designing efficient communication systems requires an understanding of the core components of network architecture:
[1]
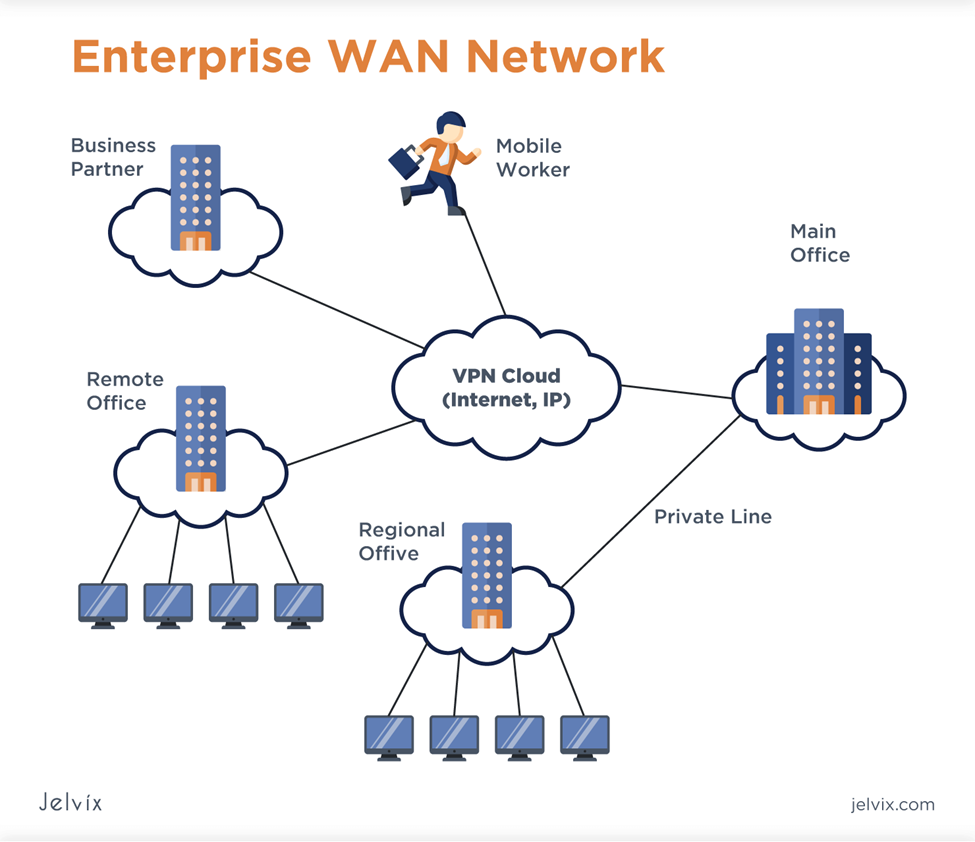
1. Network components are the fundamental elements that make up a network infrastructure. They consist of servers, routers, switches, firewalls, and access points. Each part helps with resource access, security enforcement, and data transmission in a unique way.
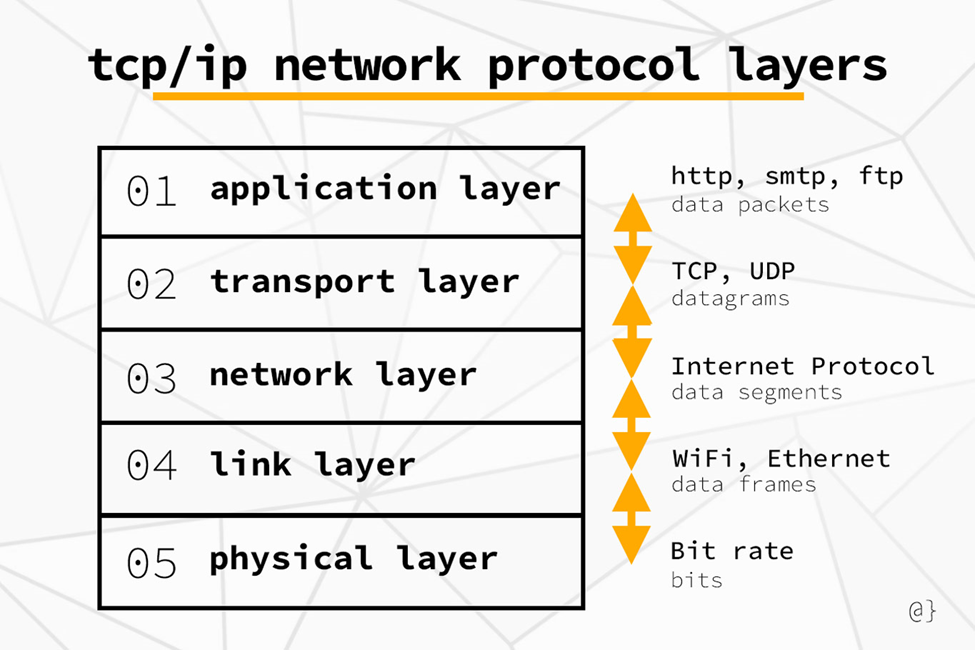
2. Network protocols: These include TCP/IP, UDP, HTTP, and DNS. They control the format, transmission, and reception of data over networks. Understanding these protocols is essential to guaranteeing smooth system and device communication and interoperability.
[2]
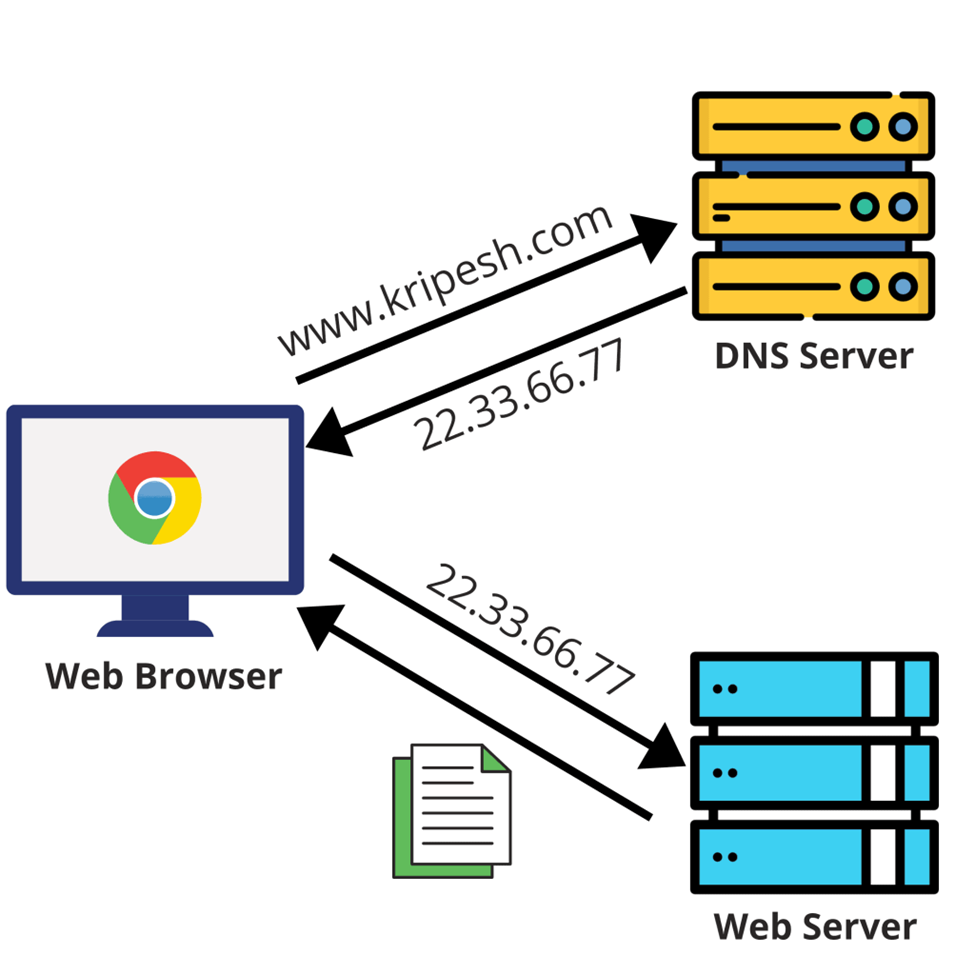
3. Addressing and Naming: Device identification and location on a network depend on IP addressing and domain naming systems (DNS). End-to-end communication and resource resolution are made possible by IP addresses and domain names, which promote smooth data interchange.
[3]
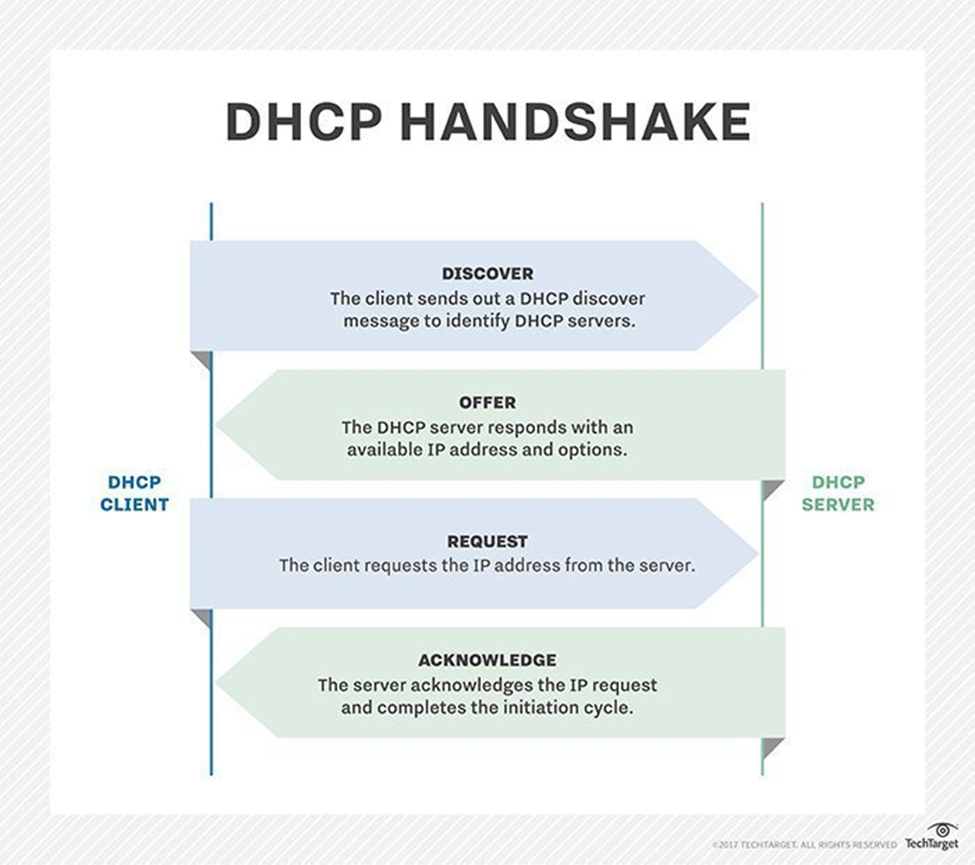
4. Network Services: By offering dynamic IP allocation, address translation, and encrypted communication channels, services like DHCP, NAT, and VPN improve network functionality and security. By putting these services into place, security risks are reduced and network performance is optimized.
[2]
DHCP: Dynamic Host Design Convention (DHCP) alters network the executives via computerizing IP address assignment. It progressively doles out IP locations to gadgets, killing manual setup bothers. DHCP leases IPs for a set span, enhancing asset distribution and working with versatility. It smoothes out gadget availability, guaranteeing consistent organization access for clients. DHCP reduces administration errors and simplifies administration tasks by centralizing IP management. It effortlessly adapts to shifting network environments thanks to its dynamic configuration of network parameters like the subnet mask and gateway. DHCP improves network effectiveness, empowering smooth correspondence among gadgets and supporting the always developing requests of current availability.
Important Design Ideas:
A set of fundamental principles that aim to optimize security, scalability, performance, and reliability guide effective network design:
1. Scalability: Without compromising performance, networks should be built to handle increases in the number of users, devices, and traffic volume. Modular elements and hierarchical structures are used in scalable architectures to enable resource allocation and expansion with ease.
2. Redundancy: In the event of failures or outages, redundancy maintains network operation by deploying backup components, links, and pathways. This ensures high availability and fault tolerance. Redundant configurations guarantee continuous service delivery and reduce downtime.
3. Resilience: Networks that are resilient are made to endure shocks and bounce back from errors fast. In order to ensure continuous operation and little service disruption, resilience is achieved through mechanisms like load balancing, route diversification, and rapid convergence protocols.
4. Security: To guard against unauthorized access, data breaches, and cyber threats, network designers implement measures like access controls, encryption, intrusion detection/prevention, and secure configuration practices. Security is of the utmost importance. Including strong security measures protects confidential data and maintains network integrity.
5. Simplicity: Scaling, managing, and troubleshooting simple network designs is easier. Network operations are streamlined by avoiding needless complexity and sticking to standardized architectures and configurations, which lowers the possibility of errors and increases overall efficiency.
Topologies of networks:
The physical or logical arrangement of linked devices and links within a network is referred to as its topology. Different network topologies provide different benefits with regard to fault tolerance, scalability, and affordability:
1. Star Topology: A centralized architecture is formed when all devices are connected to a single hub or switch. Although star topologies are easy to set up, provide fault isolation, and allow for centralized management, they are vulnerable to single points of failure at the central hub.
2. Mesh Topology: Mesh topologies create redundant pathways for data transmission by connecting multiple devices. Mesh networks are highly scalable, fault-tolerant, and redundant, but they are costly to set up and maintain.
3. Bus Topology: All devices in a bus topology are linked to a single backbone or communication line. Bus networks are easy to use and reasonably priced, but they have a limited capacity for expansion and are prone to network congestion and collisions.
4. Ring Topology: Data flows in a single direction around a ring that connects devices in a closed loop. Ring networks are easy to set up and use bandwidth effectively, but they can become congested and be susceptible to single points of failure.
Top Network Architecture and Design Best Practices:
Designing robust, effective, and secure networks requires the application of best practices. Among the crucial best practices are:
1. Modular Design: By segmenting the network into more manageable, smaller components, or modules, a modular design approach provides flexibility, scalability, and ease of maintenance.
2. Documentation: To support troubleshooting, change management, and knowledge transfer among network administrators, thorough documentation of the architecture, configurations, and policies of the network is essential.
3. Frequent Audits and Assessments: Regular audits and assessments allow for proactive optimization and security enhancement by assisting in the identification of vulnerabilities, performance bottlenecks, and areas for improvement.
4. Adherence to Standards: By guaranteeing interoperability, compatibility, and regulatory compliance, adhering to industry standards and best practices improves overall network performance and reliability.
5. Testing and Validation: To minimize risks and disruptions, it is crucial to thoroughly test and validate network designs, configurations, and security controls in order to identify and address potential issues prior to deployment.
In summary:
The fundamental components of today’s communication infrastructure, network architecture and design determine the security, dependability, and performance of networks. Through a thorough comprehension of foundational concepts, adherence to essential design principles, appropriate topology selection, and application of optimal methodologies, establishments can construct robust, expandable, and secure networks that satisfy the current digital terrain.
References
| [1] | [Online]. Available: https://www.bing.com/images/search?view=detailV2&ccid=MIol32hG&id=3F20DDDFC8EDD80700ED282CF6F2E78167D23809&thid=OIP.MIol32hG-2yJAi4PBFSQEgHaGZ&mediaurl=https%3a%2f%2fjelvix.com%2fwp-content%2fuploads%2f2021%2f07%2fwan-network.png&exph=1278&expw=1480&q=net. [Accessed 03 06 2024]. |
| [2] | [Online]. Available: https://www.bing.com/images/search?view=detailV2&ccid=l0eqToa2&id=915B1B97A763444A17832E8001D52F3617D12F3D&thid=OIP.l0eqToa2H-QAiHJHXk2KiAHaE8&mediaurl=https%3a%2f%2fwww.alpharithms.com%2fwp-content%2fuploads%2f170%2fnetwork-protocol-layers-diagram.jpg&ex. [Accessed 03 06 2024]. |
| [3] | [Online]. Available: https://www.bing.com/images/search?view=detailV2&ccid=XDSRJYLr&id=BC46D1D4A175954428380554F3F9C8D7BF162217&thid=OIP.XDSRJYLrOUhDdWULWlmb4wHaHa&mediaurl=https%3a%2f%2fkripeshadwani.com%2fwp-content%2fuploads%2f2020%2f10%2fHow-dns-works-2048×2048.png&exph=2. [Accessed 03 06 2024]. |
| [4] | [Online]. Available: https://www.techtarget.com/searchnetworking/feature/12-common-network-protocols-and-their-functions-explained. [Accessed 03 06 2024]. |
