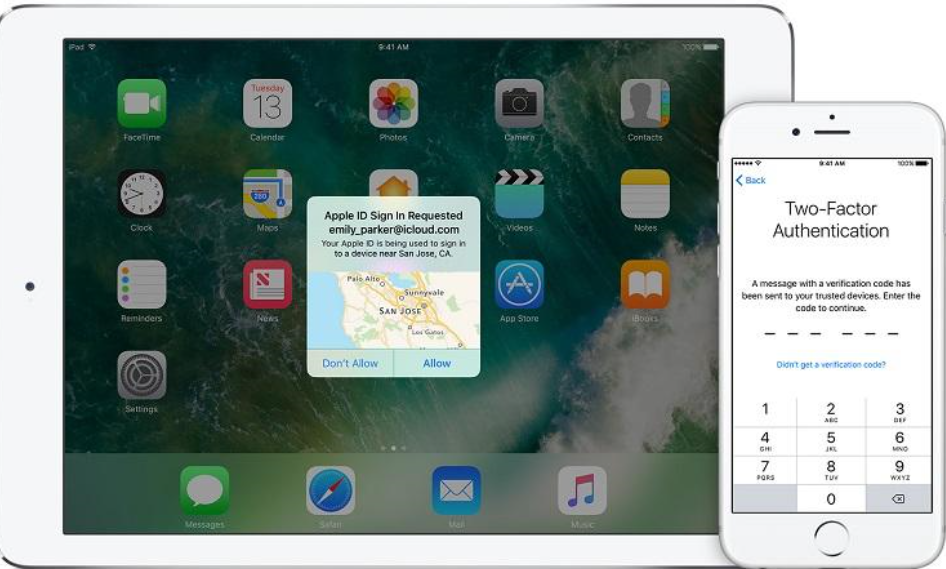
Two-Factor authentication (2FA) sometimes referred as two step verification or dual factor authentication, is a security process in which the user provides two different authentication factors to verify themselves to better protect both the user’s credentials and the resources the user can access. It provides a high level of assurance than authentication methods that depend on single factor authentication, in which the user provides only one factor – typically a password or passcode. To buy related softwares, you can go to the website like X-Tech Buy.
As the online world continues to grow, more business is conducted online than ever before, and more of our personal information is stored on websites all over the globe. Our personal information is in email accounts, internet shopping sites, online banking sites and many more places, which makes our online accounts lucrative targets for some of the world’s more unsavory characters. It used to be enough to protect your account with a password, something you could remember reliably and that was known only to you. But with the improvement in technology and the creativity of cyber criminals, it’s becoming easier for your passwords to fall into somebody else’s hands without your knowledge. One way to help make your life online more secure is to use Multi-Factor Authentication (MFA) where possible. It’s an option available for most banks some email providers such as Gmail, online payment service like PayPal and Australia post services such as Digital ID. Multiple Factors Authentication makes it harder for others to gain access to your accounts by adding a second layer of security to your accounts. Instead of just requiring your password, with Multiple Factors Authentication you’ll need to provide another piece of information known only to you. This could be a six digit PIN that is texted to your mobile phone when you login to a website, a randomly generated PIN from a key fob or phone APP, or even your fingerprint. It’s the equivalent to needing two keys to open a door. For Example, someone might have your password, but without access to your mobile phone or fingerprint, they’ll have greater difficulty accessing your account. If the safety and security of your life online is important to you, we can recommend you turn on Multiple Factors Authentication where available. While no security system is 100% fail-safe, the extra layer of security Multiple Factors Authentication provides delivers added peace of mind. If you somehow have also been a target of the hackers, you must approach a reliable cyber security expert like BITS.
Access control and an encryption have traditionally been the two stalwarts of organizational approaches to cyber security. Access has traditionally been managed and authenticated through the use of usernames and passwords, but there is significant evidence this is no longer adequate. Two factor authentication offers a way to strengthen the security around who has access to organizational systems and data.
No system is completely secure. Although two-factor authentication is a good improvement over relying on passwords alone, it may not be perfect in all situation. Two-factor authentication can strengthen security around the way users access IT services.
Nowadays, The Duo Authentication App makes the authentication process faster and easier. Duo is an app that makes it easy for an organization to implement two-factor authentication. Users simply download the Duo app to their mobile device. when logging in, they enter their username and password as usual, then use the phone app to verify their identity. You can link multiple devices to each account. To secure your home computer well, you are suggested to contact your local computer expert like “Computer Repair Onsite”.