Data is the most asset which is the reason why data security has become an international agenda. Data breaches and security failures can put the world economy at risk realising the need for national and economic security.
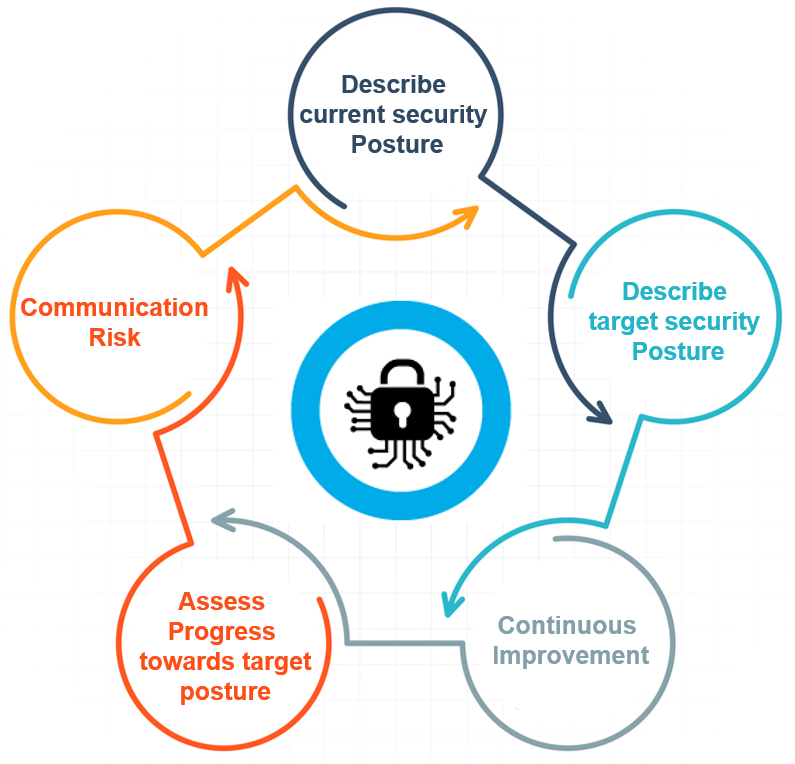
The framework will help an organisation better understand manage and reduce its cybersecurity risks. It will assist in determining which activities are most important to assure critical operations and service delivery. In turn that will help prioritise investments and maximise the impact of each dollar spent on cyber security. It results in a shift from compliance to action and specifies outcomes. By providing a common language to address cybersecurity risk management it is especially helpful in communicating inside and outside the organisation that includes improving communications awareness among planning and operating units as well as senior executives organising. It gives you a measure of where you are and where you need to go. It can be implemented in stages or degrees which make it more appealing to business. It has built-in maturity models and gap analysis, so you do not need additional majority models on top of CSF. Organisations also can readily use the framework to communicate current or desired cybersecurity postures between a buyer or supplier.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
The framework is voluntary guidance based on existing standards guidelines and practises for organisations to better manage and reduce cybersecurity risks. In addition to helping organisations manage and reduce risks, it was designed to foster communications between internal and external organisations. Now let us see the types of cybersecurity frameworks that we have so the first type of framework is PCI DSS which stands for payment card industry and data security standards. It is a set of security control required to implement protected payment account security. It is designed to protect credit cards debit cards and cash card transactions. The second type of framework that we have this ISO 270001 and 270002, which is the international organisation for standardisation. Now the best practises recommendations for information security management and information security programme elements are from this framework.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
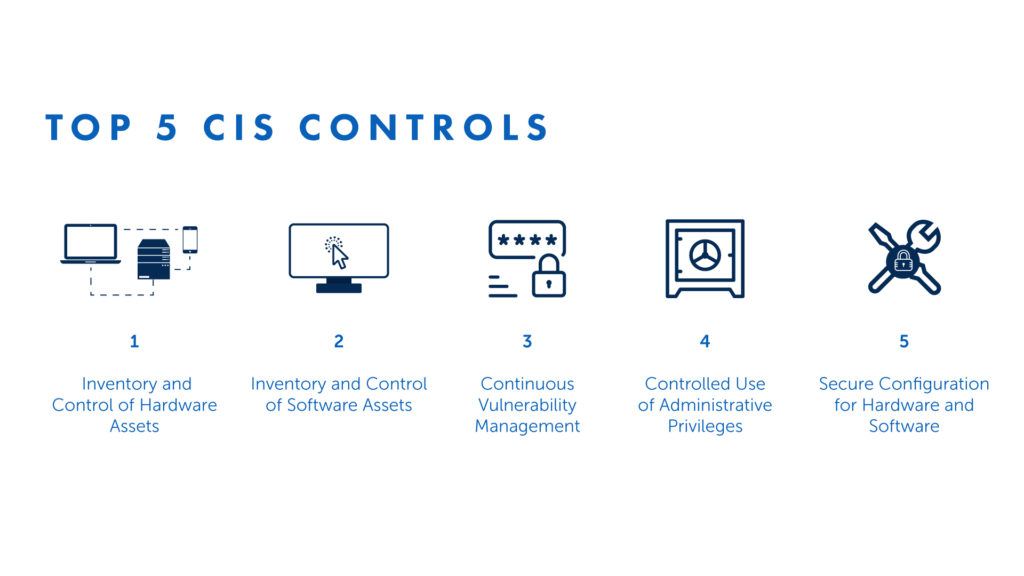
The third type of framework is CIS which stands for critical security controls. A prescribed arrangement of activities for cyber protection that gives approaches to stop. The present most inescapable and perilous attacks a key advantage of the controls is that they organise and centre fewer activities with high outcomes. Last but not least we have the missed framework honest framework is made for improvising critical infrastructure cybersecurity with a goal to improve organisations readiness for managing cybersecurity risk lodges and processes a lot of all the frameworks. We just discussed list is the most popular. It was developed in the February of 2013 after the US presidential executive order. It was designed to address national economic challenges in supposed private sectors.
Now let us just so the cybersecurity frameworks prioritised flexibility and cost-effective approach helps to promote critical infrastructure and other sectors important with economic and national security. The framework was developed to be adaptable, flexible and scalable by an organisation also it should be improved the organisation’s readiness for managing cybersecurity risks. The framework was designed to be flexible, and performance-based, and it should be cost-effective. It should leverage standards and methodologies and processes and should promote technological advancement and innovation and it should be actionable across the enterprise focus on outcomes.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
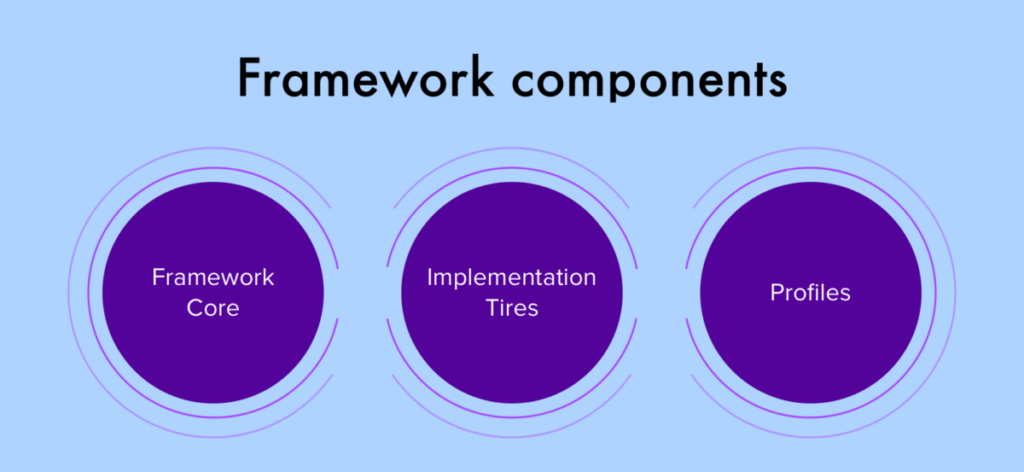
Now let us discuss the components of the cybersecurity framework. The cybersecurity framework consists of three main components namely the core, implementation tyres, and profiles. The framework or provides a set of desired cybersecurity activities and outcomes using a common language that is easy to understand. The core guides organisations in managing and reducing their cybersecurity risks in a way that is complimenting organisations existing cybersecurity and risk management processes. Next, we have the framework implementation tiers which assist an organisation by providing context on how an organisation views cybersecurity risk management. The tears guide organisations to consider the appropriate level of the further cybersecurity programmes and are often used as a communication tool to discuss the risk appetite mission priority and budget. Finally, are the framework profiles which are in organisations unique alignment of their organisational requirements and objectives risk appetite and resources against the desired outcomes of the framework code. Profiles are primarily used to identify and prioritise opportunities for improving cybersecurity at an organisation.
Let us discuss the framework tyres now that we described the degree to which an organisation cyber security risk management practises exhibit the characteristics defined in the framework. That describes an increasing degree of rigour and how well integrated cybersecurity risk decisions are into broader risk decisions and the degree to which an organisation shares and received cybersecurity information from external. Tyres do not necessarily represent maturity levels. Organisations should determine the desired style ensuring that the select level meets organisational goals, reduces cybersecurity risks to the level acceptable by the organisation and is feasible to implement physically and otherwise.
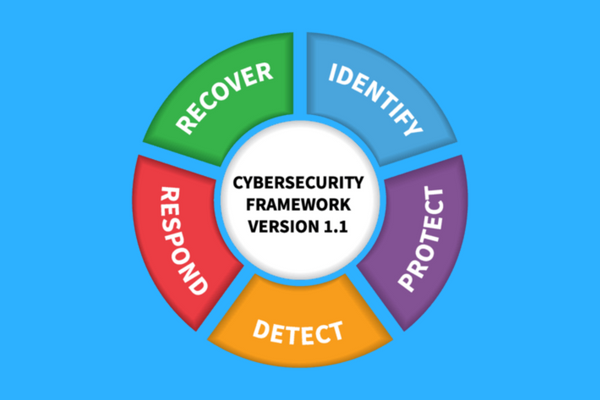
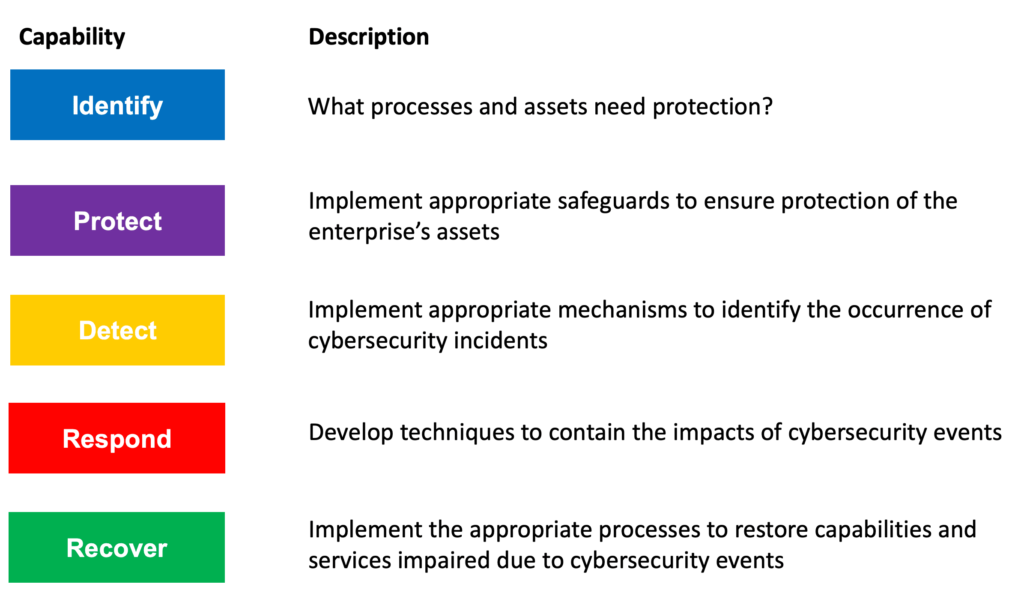
Next, we have the core. It is a set of desired cybersecurity activities and outcomes organised into categories and align into informative references. The framework core is designed to be intuitive and to act as a translation layer to enable communication between multidisciplinary teams by using simplistic and non-technical language. The core consists of three parts functions, categories and subcategories. That includes 5 high-level functions which are to identify protect, detect, respond, and recover. These five functions are not only applicable to security risk management but also to risk management. After an assessment that you need to find what protection is available. Then you need to find out what techniques can identify the different techniques can contain the impact of an incident and finally the core defines what techniques can restore the capabilities of the organisation and one direction you see last functions. They act as the backbone of the frame board that all the other elements are organised around.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/