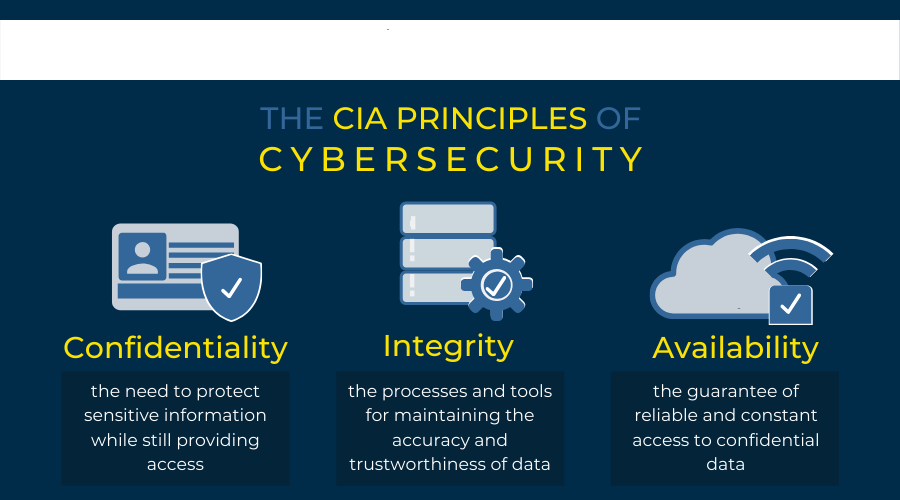
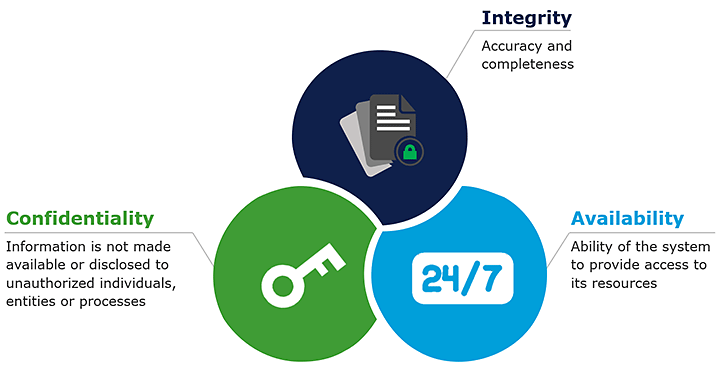
When we have a huge amount of data available, there must be some sort of mechanism and protocol to protect us from all these sorts of cyberattacks and there is a way, and this is called cyber security. In a computing context, security comprises of cyber security and physical security both are used by enterprises, to protect against unauthorised access, to data sent us another computerised system. Information security which is designed to maintain the confidentiality, integrity, and availability of data is a subset of cyber security. The use of cyber security can help prevent against cyber-attacks data breach’s identity theft and can aid in risk management. When an organisation has a strong sense of network security an effective incident response plan is better able to prevent and mitigate these attacks. For example, end user protection defence information and guards against loss of theft while also scanning computers for malicious code. Now when talking about cyber security there are three main activities that we are trying to protect ourselves against and they are unauthorised modification, unauthorised deletion, and unauthorised access. These three terms are very synonymous to the very commonly known CIA tribe which stands for confidentiality, integrity, and availability. This is commonly referred to as the three pillars of security and most security policies of bigger organisations and even smaller companies are based on these three principles. So let us go through them one by one.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
Confidentiality
First on the list, we have confidentiality. Confidentiality is roughly equal to privacy. Measures undertaken to ensure confidentiality are designed to prevent sensitive information from reaching the wrong people. While making sure that the right people can in fact get it. Access must be restricted to those authorised to view the data in question. As well for data according to the amount and type of damage that could be done, should it fall into unintended hands. Stringent measures can then be implemented across to those categories. Sometimes calling data confidentiality special training for those documents training would typically include security risks that could threaten this information. How secure is my information the other question is how secure does the data need to be? For example, if you go to any website any public facing website and you are going to see a web page. On that web page is information that is not confidential it is fully out there for every one of the publics to be. If we have a file that one of my sub directories of that website, we may want to encrypt it and maybe that file is Social Security card. Training can help familiarise authorised people with risk factors and how to guard against them. Further aspects of training can include strong password and password related best practises and information about social engineering methods to prevent them from data handling rules with good intentions and potentially disastrous results.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
Integrity
Next on the list we have integrity. It involves maintaining the consistency, accuracy, and trustworthiness of data over its entire lifecycle. Data must not be changed in transit and steps must be taken to ensure that data cannot be altered by unauthorised people. For example, in a breach of confidentiality, these measures include file permissions and user access controls. Version control may be used to prevent erroneous changes or accidental deletion by authorised users becoming a problem. In addition, some means must be in place to detect any changes in data that might occur as a result of non-human caused events. So just electromagnetic pulses or silver crash. Some data might include checksums even cryptography checksums for verification of integrity backup or redundancies must be available to restore the affected data to its correct state.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
Availability
The last one is availability. It is best insured by rigorous maintaining of all hardware performing hardware repairs immediately when needed and maintaining a correctly functional operating system environment that is free of software conflicts. It is also important to keep current with all necessary system updates providing adequate communication bandwidth and preventing the occurrences of bottlenecks are equally important. Redundancy failover and even high availability cluster can mitigate serious consequences when hardware issues too upper fast and as adaptive disaster recovery is essential for the worst-case scenarios that capacity is reliant on the existence of a comprehensive disaster recovery plan.
Safeguards against data loss or interruption in connection must include unpredictable events such as natural disasters on fire. To prevent data loss from such occurrences a backup copy must be stored in the geographically isolated location perhaps even in a fireproof water safe place. Extra security equipment’s or software such as firewalls and proxy servers can guard us against downtimes. An unreachable data due to malicious actions such as denial of service attack and network intrusions. So now that we have seen what we are trying to implement when trying to protect ourselves on the Internet, we should also know the ways that we protect ourselves when we are attacked by cyber organisations. So, the first step to mitigate any type of cyber-attack is to identify the malware or the cyber thread that is being currently going on in your organisation. Next, we must analyse and evaluate all the affected parties and the file systems that have been compromised and, in the end, we must patch the whole treatment so that our organisation can come back to its original running state without any cyber breaches.
For cloud-based solutions for the businesses like Google, AWS, and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/