It provides easy access to levels of technology that simply were not available a decade ago. You can now launch the coolant of an entire data centre with a single command. The assumption was that with that amplification the security challenges that we see on premises would grow as well. The top of their list of concerns the top security challenge for builders in the cloud is very straightforward. Their biggest challenge is making mistakes that come in the form of service misconfigurations. All each of the four hyperscale service providers Alibaba cloud, AWS, Google cloud and Microsoft Azure have had two security breaches over the past five years combined. Four have had to deal with a ton of security vulnerabilities over this timeframe.
For cloud-based solutions for the businesses like Google, AWS, and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/
Many cloud services are simply managed service offerings of popular commercial or open-source projects. These projects have had various security issues that the providers have had to deal with. The advantage for users, the builders is how operations work in the cloud. All operational work and make no mistake that security is operational work done in the cloud follows the shared responsibility model. There are six primary areas where daily operational work is required and depending on the type of service that you are using in the cloud your responsibilities shift. The applications running on that OS your data and as you move to entirely managed services you are responsible just for the data that you process in store with that service. But for all types of cloud services, you are responsible for the service configuration. Despite having a clear line of responsibilities, the providers offer several features that help you meet your responsibilities and adjust the service to suit needs. Looking back at those two security issues from the providers over the past five years. The first one will look at is from March 2020, in this case Google cloud paid out $100,000 reward through their bug bounty programme to a security researcher who found a privilege escalate in Google cloud shell.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
This is a service that provides a browser-based interface to the command line of a virtual machine running in your account. The shell is a simple container running an application that provides the required access. The researcher noticed that they were able to use a socket connection in that container to compromise the host machine and escalate their access. The root cause a misconfiguration in the access to that socket. The second example is from October 2020, for this one we turned to Microsoft Azure. Here in issue was reported in the Microsoft app services offering, this vulnerability allowed an attacker to escape the expected boundaries of the service and access a limited scope deployment server with elevated privileges. The reason a misconfiguration in the open-source tool that provided the web hosting service in this app now in both cases the vulnerabilities were disclosed quickly and responsibly, and the issue was fixed without any reported customer impacts. But both cases were in higher level cloud services. These are services that the providers teams built using other services on that platform. So as a result, and in line with the shared responsibility model they were at risk of a service misconfiguration. Even the hyperscale providers face this challenge. There is more evidence to support the fact that misconfigurations are the biggest issue in cloud security.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
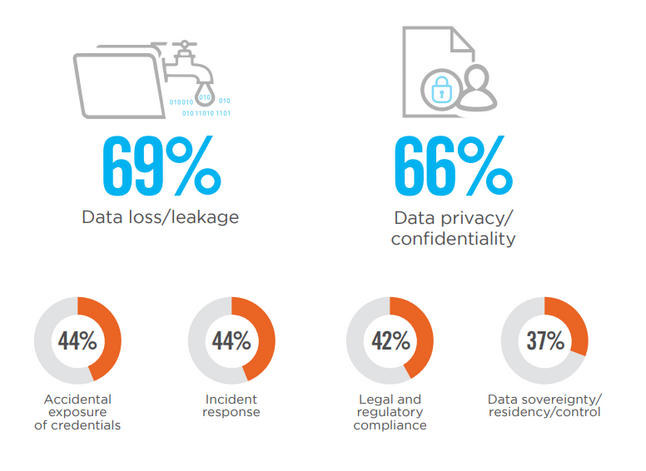
Researchers in the community that study cloud issues have all published findings that align with this premise now whether that is from other security vendors or industry organisations the findings all agree. 65 to 70% of all security issues in the cloud start with a misconfiguration. But surveys and targeted research projects only go so far.
One wrong setting one incorrect permission one simple mistake caused all these breaches that leaves just the Capital One breach. This is a more complicated event that was caused by two misconfigurations and a bug and after in-depth analysis this bug was inconsequential to the overall impact which was 100 million customer records being exposed The Capital One is a very mature cloud user their reference customer for a WS they’ve been a huge advocate for cloud within the community and they were even the incubator for the very popular open-source security governance and management tool called cloud custodian. This is a team that knows what they’re doing and yet they still made a mistake and that’s what misconfigurations.
Sometimes those mistakes or oversights other times an incorrect choice made due to a lack of awareness it all comes back to the power made inaccessible by the cloud reducing these barriers haddock a measured increase in the pace of innovation teams are moving faster and as these teams mature, they’re able to maintain a high rate of innovation with a low failure rate. In fact, 43% of teams who have adopted a DevOps philosophy are able to deploy at least once a week while maintaining a failure rate under 15%. Critically when they do encounter failure, they’re able to resolve it within the day more impressively 46% of those teams resolve those issues within the hour. But as we all know cyber criminals don’t need a day any opening can be enough to gain a foothold creating an incident.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
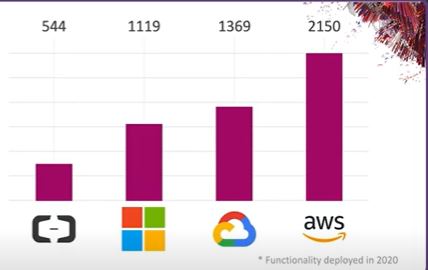
Well, the other 57% of teams the majority of which are at large enterprises often feel that their lack of pace provides a bit of protection. Moving cautiously in the cloud align to take a more measured approach. Change is still happening around them the cloud service providers themselves are moving at a rapid clip. In 2020 alone the big four hyperscale providers released over 5000 new features for their services. For a single cloud user that means almost two new features a day at a minimum and for the growing set of multi cloud users the pace of change only increases. So even if your team is moving slowly the ground underneath them is shifting rapidly. Now the goal of cybersecurity is quite simple the goal is to ensure that whatever is built works as intended and only as intended and in a traditional on premises environment this standard approach is a strong perimeter with deep visibility across the enterprise.