For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
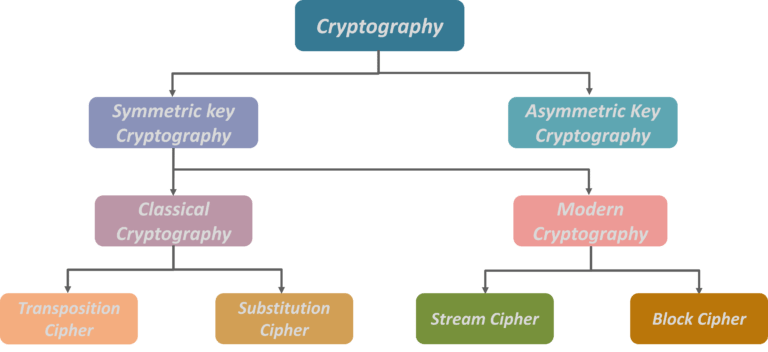
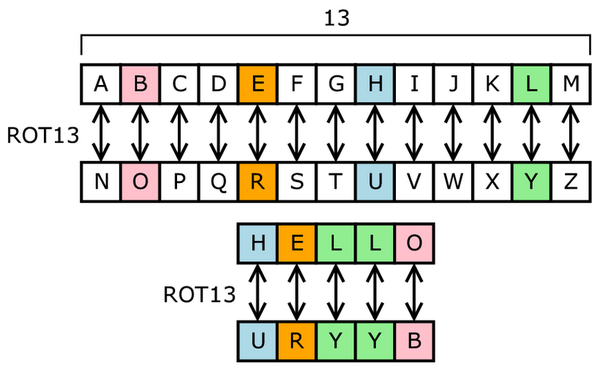
Type of keys encryption algorithms cryptography is classified under the following categories. Now cryptography is broadly classified under two categories namely symmetric key cryptography and asymmetric key cryptography, popularly also known as public-key cryptography. Now symmetric key cryptography is further classified as classical cryptography and modern cryptography. Further drilling down classical cryptography is divided into which is transposition cipher and substitution cypher. On the other hand, modern cryptography is divided into stream ciphers and block ciphers.
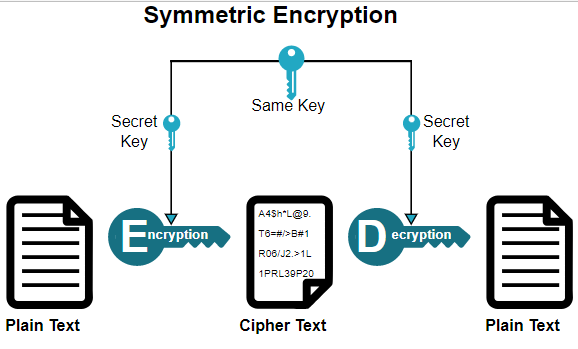
Symmetric key cryptography
Symmetric key algorithms are algorithms for cryptography that use the same cryptography keys for both encryptions of plaintext and decryption of cipher-text. The keys may be identical or there may be some simple transformation to go between the two keys. The keys in practice represent a shared secret between two or more parties that can be used to maintain a private information link. This requires that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption. In comparison to publicly encryption also known as asymmetric key encryption. Now symmetric key cryptography is sometimes also called secret-key cryptography and the most popular symmetric key system is a data encryption standard which all stands for DES.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
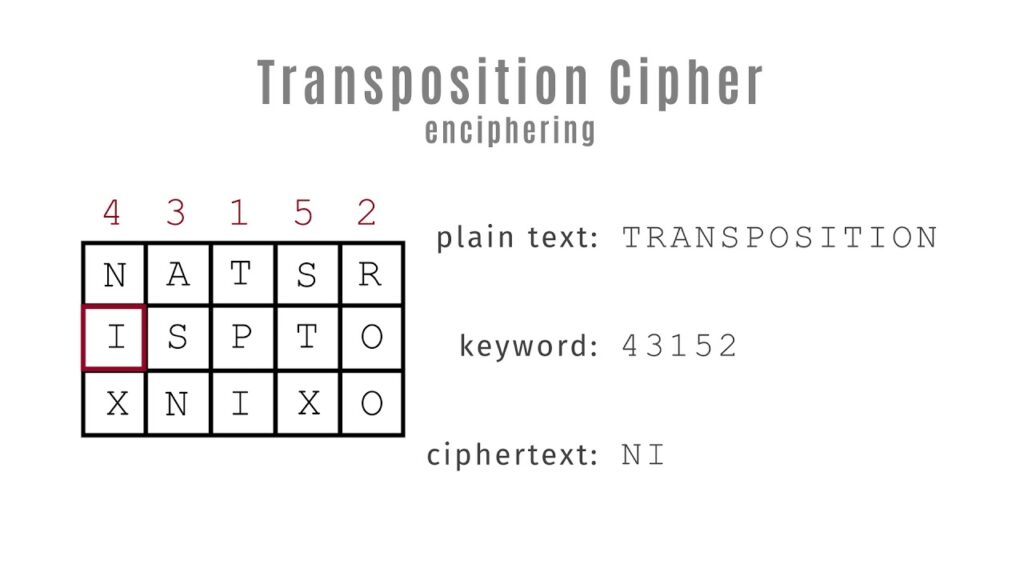
Transposition cypher
In cryptography, a transposition cypher is a method of encryption by which the positions held by units of plaintext which are commonly characters or groups of characters are shifted according to a regular system so that the cipher-text constitutes a permutation of the plaintext that is the order of units is changed the plaintext is reordered. Now mathematically speaking a bijective function is used on the characters position to encrypt and inverse function to decrypt. So, as you can see that there is an example, on the plaintext side we have a message which says meet me after the party. Now this has been carefully arranged in the encryption matrix which has been divided into 6 rows and the columns. So next we have a key which is basically 24565 and then we rearrange by looking at the plaintext matrix and then we get the cipher-text which basically is some unreadable gibberish at this moment. So that is how this whole algorithm works. On the other hand, when the cipher-text is being converted into the plaintext the plaintext matrix is going to be referred and it can be done very easily.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
Substitution cypher
Substitution of single letter separately simple substitution can be demonstrated by writing out the alphabets in some order to represent the substitution. The cypher alphabet may be shifted or reversed creating the Caesar an app stash cypher respectively or scrambled in a more complex fashion in which case it is called a mixed alphabet or deranged alphabet. Traditionally mixed alphabets may be created by first writing out keywords removing repeated letters in them, then writing all the remaining letters in the alphabet in the usual order.
Example, the F letter corresponds to Sand then the L letter corresponds to I. Then we get the cipher-text that you are using of the code and the process. Now traditionally the cipher-text is written out in blocks of fixed length omitting punctuation and spaces this is done to help avoid transmission errors to disguise the word boundaries from the plaintext. Now these blocks are called groups and sometimes a group count that is the number of groups is given as an additional cheque. Now five letter groups are traditional that we have also divided cipher-text into groups of five and this dates to when messages were used to be transmitted by Telegraph. Now if the length of the message happens not to be divisible by 5 it may be at the end with nulls, and these can be any characters that can be decrypted obvious nonsense. So, the receiver can easily spot them and discard them.
Stream cypher
A stream cypher is a method of encrypting text to produce cipher-text in which a cryptographic key and algorithm are applied to each binary digit in a data stream one bit at a time. This method is not much used in modern cryptography. The main alternative method is a block cypher in which a key algorithm is applied to a block of data rather than individual bits in a stream.
Let us see what block cypher does. A block cypher is an encryption method that applies a deterministic algorithm for the symmetric key to encrypt a block of text rather than encrypting one bit at a time as in stream cyphers. For example, a common block cypher AES encrypt 128-bit blocks with the key to a predetermined length that is either one 128,192 or 256 bits in length. Now block cyphers are pseudo-random mutation families that operate on the fixed size of the block of bits.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
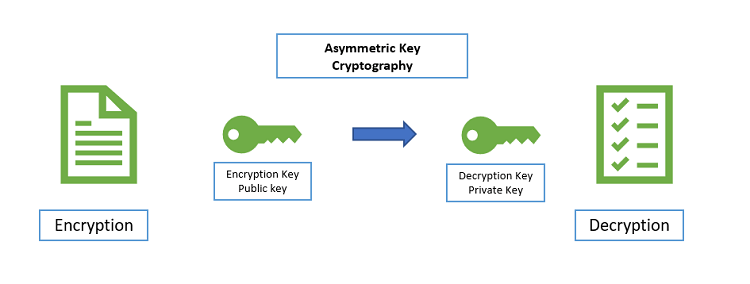
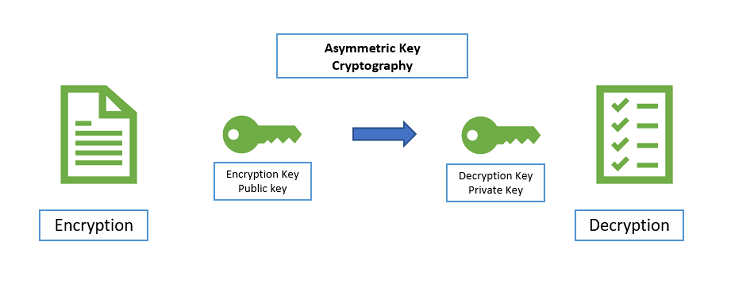
Asymmetric cryptography
Asymmetric cryptography also known as public key cryptography is any cryptography system that uses pair of keys which is a public key which may be disseminated widely and private keys which are known only to the owner. This accomplishes 2 functions authentication where the public key verifies that the holder of the paired private key said the message and encryption where only the paired private key holder can decrypt the message encrypted with the public key and the public key encryption system any person can encrypt a message using the receivers public key that encrypted message can only be decrypted with the receiver’s private key. So, to be practical the generation of public and private key pair must be computationally economical. The strength of a public key cryptography system relies on computational efforts required to find the private key from its paired public key. So effective security only requires keeping the private key private and the public key can be openly distributed without compromising security.
For general support issues of home users please visit: https://www.computerepaironsite.com.au/