The abbreviation of boot sector virus is BSV, which will continuously be used in this blog. By the name of this virus, it is easy to tell where this virus resides, i.e., the disk’s boot sector. Every time any disk is mounted, the computer automatically tries to read and execute its boot sector. Now imagine this specific disk contains a virus in its boot sector along with the other programs. Then you, without knowing at all, mount this disk in the computer. The computer will start reading it and executing it. In the meantime, the virus residing in the boot sector will automatically run itself with the other executables, which will now flow through your computer and start making copies of itself in every drive you have created. Similar to a common biological virus, this computer virus or BSV resembles the functionality of multiplying. As the biological virus multiplies itself in a human body, BSV starts making a copy of itself in a computer and expands its area of damage. Before getting into more details, let’s see where specifically this virus resides in a disk. Naturally, the disk’s boot sector is the first sector as the format depends on the operating system. The disk may also include an information table knowing the partition of the disk. Now including these files, there is one more file that is not listed in the table. This file is located in the boot sector and is executed each time when the disk is mounted. This specific sector is responsible for loading your operating system. And this is the place where BSV can be located.
What is Boot Sector Virus capable of?
The primary purpose of BSV is as follows:
- This specific virus can move or flow in the computer and move from one computer to another when connected. This movement of this virus is the most important feature. And this feature distinguishes itself from other types of viruses.
- It has the capability to install itself on a computer without having any consent from the owner of the computer.
- The damaged power can be stated in a way that it can change or manipulate the real function of another executable file.
- It is also able to restrict a user from using a specific resource.
- In whatever type of executable file the BSV is hidden, it will execute when the parent executable is running.
Working of Boot Sector Virus:
Whenever a computer is built, an executable file is loaded into its Read-Only Memory (ROM), where the program remains safe, and as ROM is a non-volatile memory, therefore, the file keeps its content even when the power of the computer is unplugged.
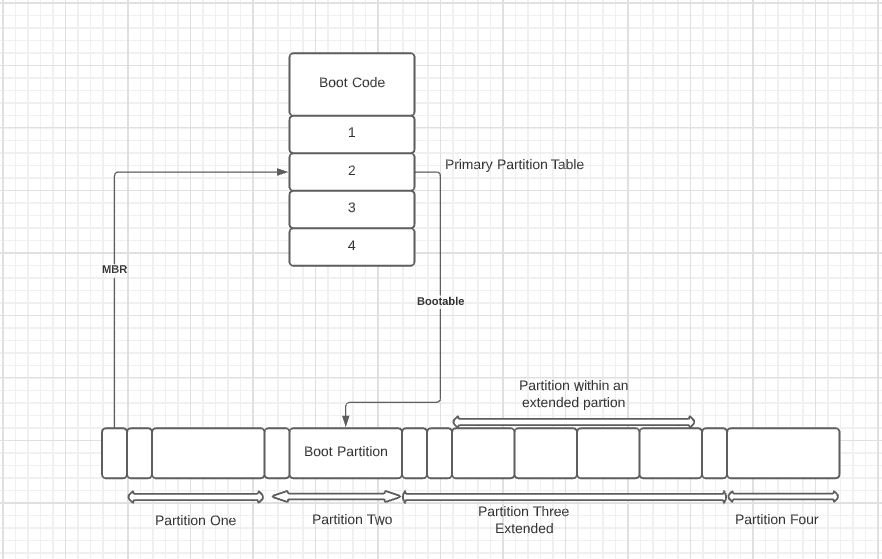
Whenever the computer is switched on, it automatically executes the bootstrap loader. This bootstrap loader is basically the first thing to run on a computer, due to which the operating system starts up. The bootstrap loader has a proper flow chart to follow, i.e., the bootstrap loader follows a technique to find out executable files in a disk. Usually, there is more than one executable file, so then the bootstrap loader executes a jump instruction which takes it to the beginning of the boot sector. The boot sector is used because it contains a program called the Master Boot Record (MBR). This program has a piece of knowledge about all the partitions in the disk and shows a list of two users to select one. Now here, this whole system is the best place for the virus. Because these executables are the first ones to execute, now, this creates an issue that why the virus can’t be seen in the directory of the disk? To answer this, suppose the virus is already written in a disk that was infected at its manufacturing. The virus can’t be seen in it because it may be written in on an extra track of the disk which was created while infecting the disk. This extra track is between the existing tracks or very close to the edge of the disk, which cannot be scanned by the anti-virus. Hence this becomes the best place to hide the virus.
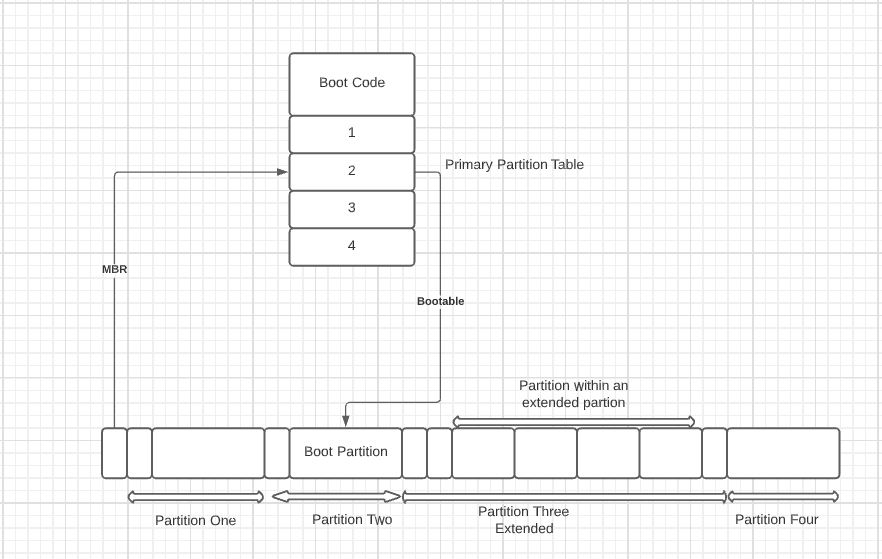
The effect of Boot Sector Virus on a Windows operating system:
So the BSV can have total control of the master boot record and can delete or manipulate the file present in it. Due to which the virus can expand its hiding region, which can be more harmful; instead, it can crash the entire system by creating changes to the main file.
The BSV spreads in the system by infecting the MBR (Master Boot Record); this causes the system not to boot itself. This virus is so destructive in nature that a user can only get rid of it by completely formatting the hard drive, which in the end results in data loss.
Now just to summarize, a boot sector virus infects a boot sector of the disk and hides there where it can delete or change the executable programs. The virus has the ability to stay in memory and function itself to move from one spot to another. So if a USB or any type of data transfer device is used, the virus can move into it by finding a spot at the edge of the disk or between the disk tracks; as a result, the virus is transferred to another computer.
The easiest and only method to detect the virus is that any of the programs in your computer can never change its content or file feature until and unless the user updates the file by downloading the new version or update of it. So whenever there is any irregularity in some sort of file, do go through its properties and check if there is any sort of changes or it is updated without the user’s consent. Nowadays, the anti-virus can notify if there is any sort of changes in the file has taken place or not.