What is AI?
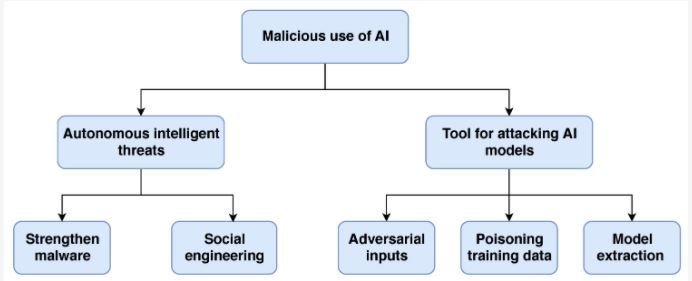
Artificial intelligence (AI) is an umbrella expression used to explain various programming routines or disciplines. Artificial intelligence makes it visible for computers or machines to understand and learn from past experiences, make adjustments with new input, and carry out tasks that humans do just like them. Almost all examples of artificial intelligence you hear or see today, from the computer that plays chess to self-driving auto cars, depend mainly on Deep learning neural networks.
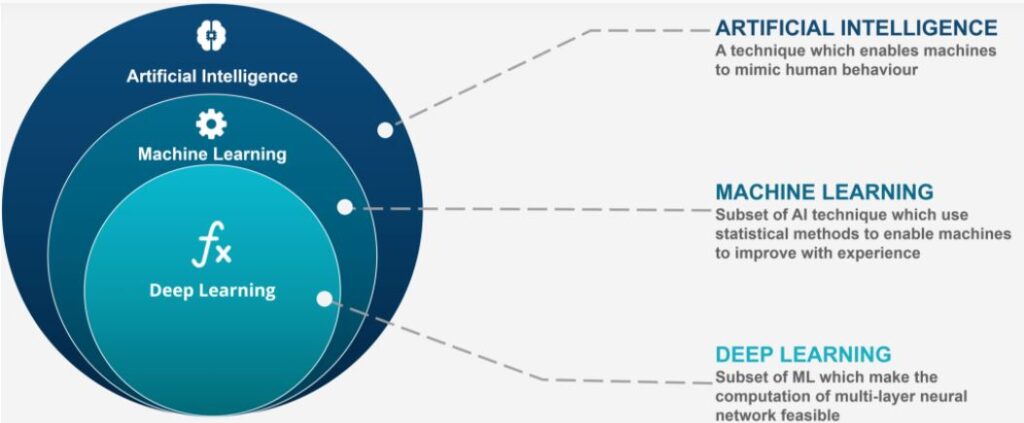
How AI-enhanced cyber threat?
Digitalization keeps increasing the prospective attack surface dramatically, presenting new opportunities or ideas for the online hacker’s community. Besides their growing collection of Advanced Malware or virus and zero-day hazard, Artificial Intelligence and machine learning are the latest equipment added to the toolkit belonging to them. It is not surprising for anyone that nowadays, AI is being utilized by cyber enemies.
Using AI and automation authorizes evil people or hackers to carry out additional Bushwhacks at a rapid rate, and it shows that security crew should also increase their speed and technology to match them. Moreover, the worst part is that all this is occurring in the present time, and we are witnessing fast development, so the time is too short of deciding whether to use your personal AI countermeasures.
How AI helps to increase cyber threats?
Following are some points that show that besides having many cybersecurity benefits, artificial intelligence is also beneficial for cybercriminals and enhanced cyber threats.
1. AI offers cybercriminals or actors more bang for the buck:
Cyber actors also face economic realities just like their target or victims; zero-day risk can be very costly to recognize and utilize. Generating new risk and Malware or viruses requires time and can be highly expensive, as can leasing or renting a virus like a service mechanism of the deep and dark network. Just like any other person, cybercriminals are aiming to obtain the maximum bang for their investment (buck) which means obtaining the highest rate of interest (ROI) with the minimum amount of fixed cost expenditure, which includes money, effort, and time, while boosting the effectiveness and value of the tools and methods which they used.
Artificial Intelligence and machine learning make cybercriminals generate Malware or virus that can find the vulnerabilities on their own and later independently find out which payload will have the high rate of success without revealing itself using persistent connections back to its C2 workstation or server.
We have previously witnessed multivector attacks merged with APTs (advanced persistent threat) or payload arrangement. AI boosts the efficacy of the following tools by independently studying about attacked system; thus, attacks could be laser-focused except for using the normal slower and disorganized approach, which can warn the victim about the attack.
2. AI reduces time to breach:
We all can easily predict attacks to get faster with the introduction of technologies like 5G connections. 5G also makes edge devices able to communicate faster, generating impromptu networks that are difficult to secure and easy to abuse. This can bring about Swarm based raids, where every component does a particular task as part of a more powerful, coordinated attack.
Whenever you integrate AI into the network of linked machines that can communicate and transfer data at 5G speeds, you build a situation in which those machines can not only self-initiate an attack but can also personalize the attack at a digital pace contingent on information that it gets during the process of attack.
Swarm Technology enables the smart Swarm of Machines to share data and learn from one another. Cybercriminals can generate attacks competent of quickly estimating weaknesses by applying self-learning technologies, and after that, they apply techniques of countering attempts to finish them.
3. AI-based cyber-attacks will be more affordable:
In the past human-made cyber weapons were very expensive as it was complex to make them. Nevertheless, with AI, cyber actors will make weapons much more rapidly, in bulk, and more flexibly.
It will lower the black market price of these weapons, and simultaneously these weapons will be abundant and freely accessible by a large number of persons.
Hope the readers would have more clarity after reading this piece. Any comments or suggestions are welcome as we strive to make technology easier for everyone.