Cyber Crime is a global problem, and it has been dominating the news cycle. This poses a threat to individual and organisational security alike. It is a threat to banks institutions and governments. Today’s organised cybercrimes far out shadow lone hackers of the past and are large, organised crime rings that function like start-ups and often employ highly trained developers constantly innovating or 9 attacks. With so much data to exploit out there. Cybersecurity has become a crucial domain and all companies in the world are looking to hire skilled cybersecurity experts.
For cyber security related issues of businesses please visit: https://www.benchmarkitservices.com/cyber-security/
It can be rightfully said that today’s generation lives on the Internet and we general users are almost ignorant as to how those random bits of ones and zeros reached securely to a computer. It makes sure that your packets reached you un snuffed. We were living in the digital era whether it is booking a hotel room, ordering some dinner or even booking a cab be costly using the Internet and inherently constantly generating data. This data is generally stored on the cloud which is basically a huge data server or data centre that you can access online. Also, we use an array of devices to access this data. Now for a hacker it is a golden age but so many access points public IP addresses and constant traffic and tonnes of data to exploit. Black Hat hackers are having one hell of a time exploiting vulnerabilities and creating malicious software for the same. Above that cyberattacks are evolving by the day hackers are becoming smarter and more creative with their malware ares and how they bypass virus scan them n firewalls still baffle many people.
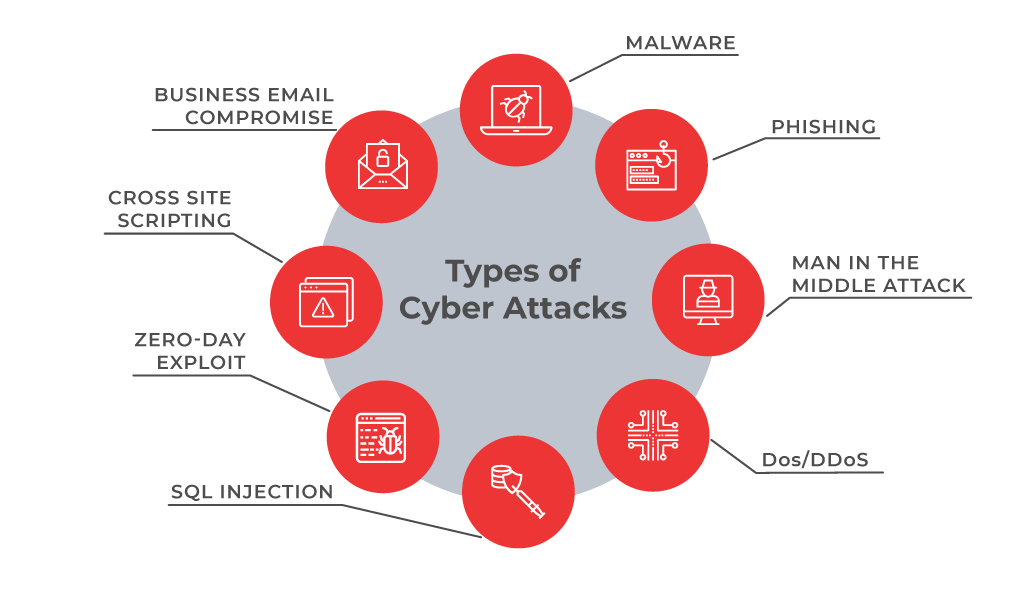
Let us go through some of the most common types of cyberattacks. I have listed out eight cyberattacks that are plagued us since the beginning of the Internet. Let us go through them briefly.
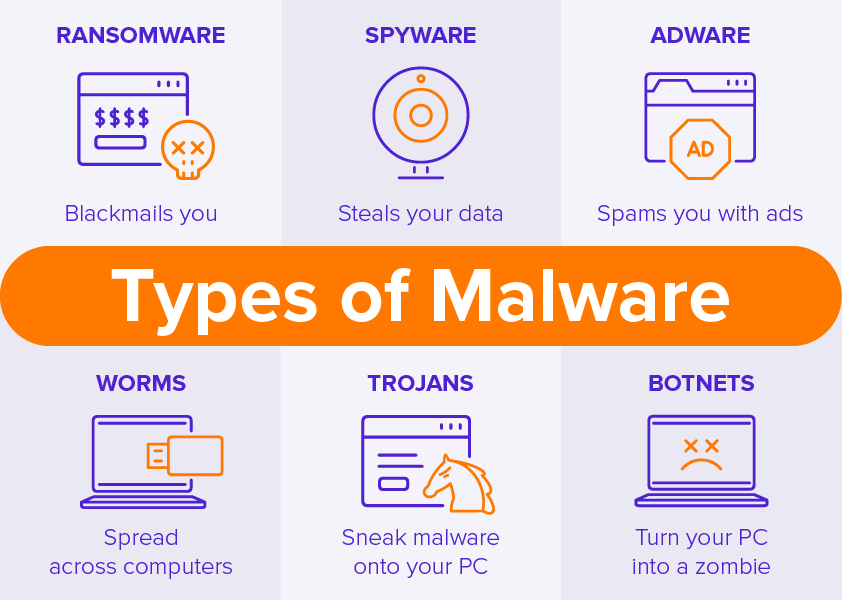
Malwares
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
First, on the list, we have general malware. Malware is an all-encompassing term for a variety of cyber threats including Trojan’s, viruses and bumps. Malware is simply defined as a quote with malicious intent that typically steals data or destroys something on the computer.
Phishing
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
Next on the list, we are phishing. Often posing as a request for data from a trusted third party. Phishing attacks are sent via email and ask users to click on the link and enter their personal data. Phishing emails have gotten much more sophisticated in recent years making it difficult for some people to discern a legitimate request for information from a false one. Phishing emails often fall into the same category as spam but are more harmful than just a simple ad.
Password Attacks
Next on the list, we have password attacks. A password attack is exactly what it sounds like, a third party trying to gain access to your system by cracking a user’s password.
DDoS
Next up is DDoS which stands for distributed denial of service. A DDoS attack focuses on shopping. The service over network attacker said high volumes of data or traffic through the network that is making a lot of connection requests. Until the network becomes overloaded and can no longer function.
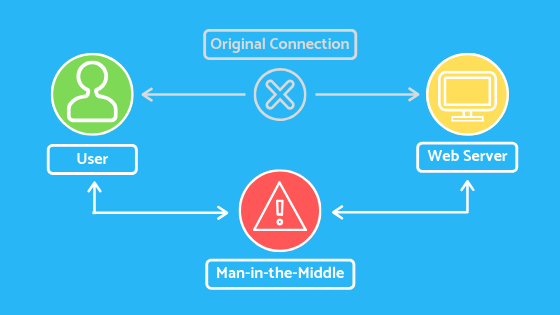
Man in the Middle Attacks
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
Next up we have a man in the middle attack by impersonating the endpoint in an online information exchange that is the connection from your smartphone to a website. The MITM attacks can obtain information from the end-users, an entity he or she is communicating with. For example, if you’re banking online the man in the middle would communicate with you by impersonating your bank and communicate with the bank by impersonating you. The man in the middle would then receive all the information transferred between both parties which could include sensitive data such as bank accounts and personal information.
Drive-by Downloads
Next up we have driven-by downloads through malware on the legitimate website a programme is downloaded to a user system just by visiting the site it does not require any type of action by the user to download it.
Mal Advertising
Next up we have mal advertising which is a way to compromise your computer with malicious code that is downloaded to your system when you click on an affected ad.
Rogue Software
For cloud-based solutions for the businesses like Google, AWS, and Azure please visit: https://www.benchmarkitservices.com/google-cloud-service-providers/
Lastly, we have rogue software which is basically malware that is masquerading as legitimate and necessary security software that will keep your system saved. So, as you guys can see how the Internet sure is in the same place as you might think it is. Not only applies to us as individuals but also to large organisations.
There have been multiple cyber breaches of the past that has compromised the privacy and confidentiality of our data. If we head over to the site called information is beautiful. We can see all the major cyber breaches that are being committed. Even big companies like eBay, Adobe have gone through major cyber breaches even though they have a lot of security measures taken to protect the data that they contain. So, it is not only those small individuals are targeted by hackers and other people, but even bigger organisations are constantly being targeted by these guys so after looking at all sorts of cyberattacks possible the breaches of the past and the sheer amount of data available. We must be thinking that there must be some sort of mechanism and protocol to protect us from all these sorts of cyber-attacks and indeed there is away, and this is called cyber security.
In computing, context security comprises of cyber security and physical security both are used by enterprises to protect against unauthorised access to data centres and other computerised systems. Information security is designed to maintain the confidentiality, integrity and availability of data in a subset of cyber security. The use of cyber security can help prevent cyberattacks data breaches, identity theft, risk management. When an organisation has a strong sense of network security, and an effective incident response plan is better able to prevent and mitigate these attacks. For example, end-user protection defence information and guards against loss or theft while also scanning computers for malicious code.
For general support issues of home users please visit: https://www.computerepaironsite.com.au/