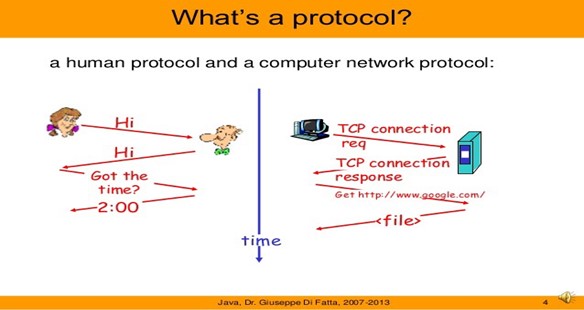
The elements of protocol are message encoding, message formatting encapsulation, message timing, message size, and message delivery options. We shall see each of these elements in a detailed manner.
Protocol
Interconnected communication is not enough to ensure nodes talk to each other, that is the reason protocols are essential for them to communicate. The uses of protocols ensure the speed, how fast shall we talk, how do we talk, who talk first, can we talk together, do you understand what I am talking. Computers should follow some set of rules and conventions, consider computer A is transferring a movie to computer B. Consider two cases first when they are not following a set of rules and conventions and the second one when they are following is set of rules and conventions, in the first case computer B will pop up a message saying the file is corrupted on the other hand. In the second case computer, would be able to understand this file as a movie that is data transfer. In second case is successful because both computers followed some guidelines. It is like both computers decided to speak same language instead of speaking different language. It transfers data from one computer to another in the form of packets which hold file, is divided into small pieces some security measures are added to each packet these packets are received and reassembled at destination to generate the original file. The security measures that are added to each piece are decided by network protocols and the receiving computer will be able to understand the received packet and hence the whole file if and only if it follows the same networking protocol.
To purchase any IT related software or hardware please visit: https://www.xtechbuy.com/
Message Encoding
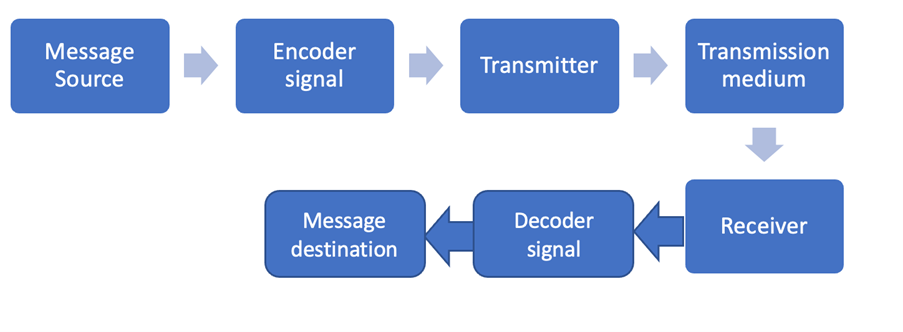
It means the source, that is the source computer generates a message. It gives that message to the encoder in order to generate signals. Once the data is converted into signals, now it is given to the transmitter for transmission. Then why we need encoder here is because, we have two kinds of transmission medium one is a wired medium another one is a wireless medium. The source must understand to which medium it is connected to. If it is a wired medium, the data must be converted into signals in order to facilitate the data transmission on a wire medium. If it is a wireless medium, the sender half to encode the data in the form of waves because this is a wireless medium we cannot send signals, we must send waves and once the data is sent through the transmission medium the receiver receives the data and a corset decoding, it means the message has reached the destination. This is what message encoding is all about the sender sends the data the sender creates the data and then quote the data and finally the transmitter sends the data through the transmission medium this transmission medium takes the data to the receiver the receiver after receiving the data it decodes the data and after proper decoding it means the message has reached the destination this is what message encoding is all about.
For general support issues of home users please visit https://www.computerepaironsite.com.au/
Message formatting and encapsulation
This means both sender and receiver must mutually agree upon certain formats which we call as formatting at the same time when the receiver receives some data it should identify who has sent this data. We are going to add some information with the data in order to identify the sender and the receiver, so we are not going to just send data asset we are going to encapsulate certain things like the source information and the destination information with the data so that the right sender and the receivers are identified.
For general IT Support services for Businesses please visit: https://www.benchmarkitservices.com.au
Message sizing
If there is a very big message to be communicated to the destination, human breaks the message into smaller parts or sentences see if sender has a very big content to be sent. So, what sender does it breaks the message into smaller parts or sentence is likewise our computer should also do that if the capacity of the link is very small but the data to be transmitted is very big, this computer should break this big message into smaller units which this transmission medium can handle. This is what message sizing, and this is one of the things a protocol should do.
For cyber security related issues please visit https://www.benchmarkitservices.com/cyber-security/
Message timing
It is the 4th element of protocols and message timing deals with the flow control and response time mode. Let us first talk about flow control, assume that the sender is very fast and the receiver is slow. Since the sender is very fast it can send data at high speed and what about the receiver, he cannot handle that speed. If there is no flow control mechanism, he can keep on sending data, but he cannot receive the data. So, the entire communication will become useless. It is the responsibility of the protocol to provide flow control mechanism at the same time the sender is sending some data and the receiver must acknowledge the data when the acknowledgement is sent back to the sender. The sender can understand that the data is received by the destination, but the acknowledgment is not received. The sender must wait for a certain period after the expiry of the time. The sender will retransmit the same so that we can ensure guaranteed delivery and it is the responsibility of the protocol to tell how much time this computer should wait for an acknowledgment.
For Data security related issues of businesses please visit: https://www.benchmarkitservices.com/backup/
Message Delivery options
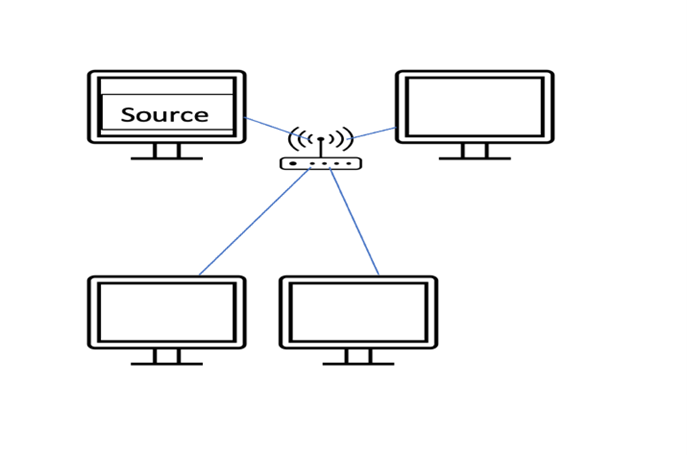
There are three delivery options one uni cast, the second is multicast, and the third is broadcast unicasting. It means one sender and one receiver; this is centre is going to same data to exactly one receiver in the network. If the sender is sending the data to exactly one destination, it is called as unicasting. When the sender sends the data to set of receivers but not to all then this is multicasting. Broadcasting means the sender sends the data to all the participants in the network then we call us broadcasting.
For cloud-based solutions for the businesses like Google, AWS and Azure please visit https://www.benchmarkitservices.com/google-cloud-service-providers/