Hello friends, in this blog I want to discuss regarding white hat and black hat attacks in the existing medium. The topic is related to cyber-attacks and processing techniques of hacking capability.
Introduction
Hacking techniques will steal all the sensitive information. The security methods will refer to computer programming structures where all the network security systems are associated with cybercriminal technologies. The application of cyber community system deals with various types of malicious or legal hacking application system. The cyber risk and programming structure determined about all the hacking technologies. The existing design structure of hacking consist of white, black hat hacking. The white hat hackers are good hackers or ethical hacker who will analyse about all key sources of the ethical hacking system. Malicious attacks or illegal hacking techniques refer to black hat hacker.
White hat hacker
The white hat hacker refers to an ethical hacker or good hacker such that it creates efficient exploration between computer systems on the network where identification of security improvements is recommended to reduce the black hat attack in system. The subject of ethical hacking systems is associated with penetrating testing and have the efficient capability to find out one ability and also access the risk method in the entire data system. There are many ways to use white hat hacking system over black hat hacking, this is because of improvement of vulnerabilities and ensure that black is not able to access system data because the white hat hackers will improve the design of the existing system.

Influence of white hat hackers
White hat hacker is good and also access information to create efficient output according to the influence of the hacking system.
1. Tim Berners- lee
The applications referred with computer science data sources and this is executed with worldwide techniques.
2. Greg hog loud
The computer forensic applications give the best research contribution according to malware detection and online gaming system.

Ethical hacking
The ethical hacking steal information but it is incorporated with efficient hacking systems and create positive conditions regarding data enhancement capability. The data sources and different type of hacking systems are involved with white hat hacker. Applications and ethical hacking technologies are associated with penetrating testing and also have an efficient output with the consideration of good intentions system.
Click here for Cybersecurity issues

White hat penetrating testing
In the enterprise space functionalities, white hat hacking system is most needed to create a give traditional functionality where the sources of penetrating testing are provided with an efficient service management system.
The pen testing methods and white hat hackers are employed to hack the network in a way where the private network access and applications are associated with the ethical hacking system. The approach of endpoint data structures and proactive gaps of security systems are associated to improve the zonal of system methods and also create functionality through which testing criteria are successfully operated.
By using talented hackers, we can clearly analyse proactive and attach security to have efficient defence techniques which are operated before a real attack system. The white hart penetrating testing have a weakness to identify the application of weakness through pen testing capability systems.
The application of test cases is identified to address new policies, configuration tools and all the operations are adopted to stop the threats.
The penetrating testing will check for all infiltrating, breaking out the entire system data into various applications. The application of one face of cyber kill chain is associated with network management functionality and also create is the stealing of data backup systems. The sources and non-typical coverage of pen testing are associated to create an impact on the organisation data system.
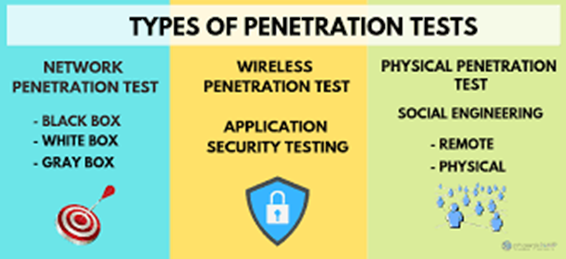
White hat hacking tactics
The white hat hackers use similar tools and technologies with real-time attacking systems. The application consists of root kids where the proven tools and complex sophisticated applications are authorised with social engineering methods. The data protocols and endpoint vulnerabilities are associated with protocol spoofing systems. White hat hackers try to create security between all the components of data systems and find the applications to create execution with successful methods of the data system.
Click here for Data security issues
Automatic white hat hacker.
- The application will limit the set of techniques and applied with a short time frame.
- The technical perspective and primary focus is on infiltration.
- Update and change of data systems are associated with the relevant finding.
Black hat hackers
The black hat hackers identify the sensitive information’s which is located in computer network capabilities and bypass all security protocol methods. The applications are carried out with various malware application technologies and it steals the personal information’s and financial data entities. The black hat hackers will steal all the confidential information and lead to cybercrime methods, the application half a range from analysing the spread of malware applications and experience hacking capabilities and the main aim is to steal the sensitive data and specify financial information because all the personal information like login credential data are needed to authorise to create efficient security methods.
- The black hat hacking is most dangerous to steal personal information.
- The black hat hacker analyses gain of unauthorised access into a network application system.
- Implementation methods and infield damages are authorised with the security system and alter all the functionalities which are acquired through network data.
Hacking is a business
The technologies and black hat hacking start with the script and purchase all tools to explore the security methods. The bug detection methodologies and exploration of skilled hacking systems are analysed to with sophisticated criminal organisations where all the collaborative tools of working principles are created with efficient agreement method and also create legitimate business management functionalities with all sources of data systems. The design capabilities and development of phishing or managing remote access systems are collaborated to improve the connections and also sell malicious software applications according to the franchise for releasing of agreements with the business world. Distributing malicious software applications is not a simple task and operate all business collaborative technology where partners, vendors and resellers are associated to buy Marlboro applications to analyse criminal organisational task.
Black hat global
The black hat hacking problems is a global problem and it is difficult to stop all the errors and existing system. The resultant applications are associated to create enterprise impact of data systems and all the challenges are associated to acquire cross multiplication data systems.
- Security mistake are created.
- Antiviruses
- Firewalls should be analysed to reduce attack in the application system.

