A penetration test, otherwise called a pen test, is a reproduced cyber-attack against your PC framework to check for exploitable vulnerabilities. With regards to web application security, penetration testing is generally used to increase a web application firewall.
Pen testing can include the endeavoured penetrating of quite a few application frameworks, (e.g., application convention interfaces (APIs), frontend/backend workers) to uncover vulnerabilities, for example, unsanitized inputs that are powerless to code infusion attacks.
Experiences given by the penetration test can be utilized to calibrate your WAF security strategies and fix detected vulnerabilities.
PENETRATION TESTING STAGES.
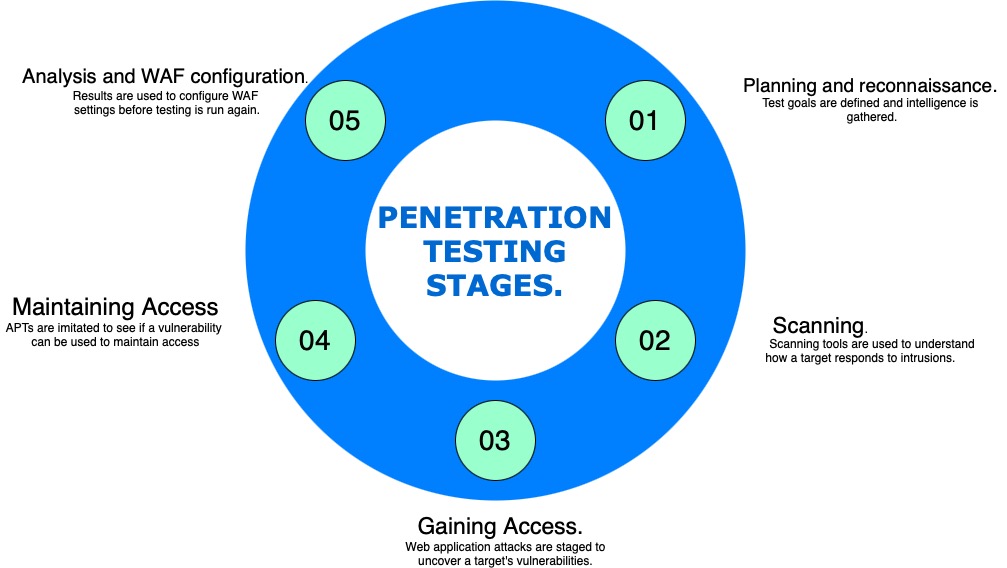
1. Planning and reconnaissance:
The first stages involves:
. Characterizing the extension and objectives of a test, including the frameworks to be addressed to and the testing strategies to be utilized.
. Gathering intelligence (e.g., organization and domain names, mail server) to all the more likely see how a target functions and its potential vulnerabilities.
2. Scanning:
The subsequent stage is to see how the target application will react to different interruption attempts. This is normally done utilizing:
. Static Analysis: Examining an application’s code to appraise the manner in which it acts while running. These tools can scan the sum of the code in a single pass.
. Dynamic Analysis: Investigating an application’s code in a running state. This is a more reasonable method of scanning, as it gives an ongoing perspective into an application’s performance.
3. Gaining Access:
This stage utilizes web application assaults, for example, cross-website scripting, SQL infusion and indirect accesses, to reveal a target vulnerabilities. Testers at that point attempt and endeavor these vulnerabilities, normally by raising advantages, taking information, capturing traffic, and so on, to comprehend the harm they can cause.
4. Maintaining Access:
The objective of this stage is to check whether the vulnerability can be utilized to accomplish a persistent presence in the exploited framework—long enough for an agitator to acquire inside and out access. The thought is to copy progressed determined dangers, which frequently stay in a system for quite a long time to take an association’s most touchy information.
5. Analysis:
The aftereffects of the infiltration test are then gathered into a report itemizing:
. Specific vulnerabilities that can be misused.
. Delicate information that can be accessed.
. The amount of time the pen tester had the option to stay in the framework undetected.
This data is examined by security staff to help arrange a venture’s WAF settings and other application security answers for fix vulnerabilities and ensure against future assaults.
PENETRATION TESTING METHODS.
External Testing:
External testing tests focus on the resources of an organization that are visible on the web, e.g., the web application itself, the organization site, and email and domain name workers (DNS). The objective is to obtain entrance and extract significant information.
Internal Testing:
In an internal test, a tester with admittance to an application behind its firewall recreates an attack by a malicious insider. This isn’t really recreating a rogue worker. A typical beginning situation can be a representative whose accreditations were taken because of a phishing attack.
Blind Testing:
In a blind test, a tester is just given the name of the venture that is being focused on. This gives security work force an ongoing investigate how a real application attack would occur.
Double-blind Testing:
In a double-blind testing, security staff have no earlier information of the simulated assault. As in reality, they will not have any an ideal opportunity to support their defences before an attempted breach.
Targeted Testing:
In this situation, both the tester and security staff cooperate and keep each other assessed of their developments. This is a significant preparing exercise that furnishes a security group with constant criticism from a hacker’s point of view.
PENETRATION TESTING AND WEB APPLICATION FIREWALLS.
Penetration testing and WAFs are exclusive, yet mutually beneficial security measures.
For some sorts of pen testing (except for blind testing and double-blind testing tests), the tester is probably going to utilize WAF information, like logs, to find and adventure an application’s weak areas.
In turn, WAF administrators can profit by pen testing information. After a test is finished, WAF setups can be refreshed to secure against the weak areas found in the test.
At long last, pen testing fulfills a portion of the consistence necessities for security examining techniques, including PCI DSS and SOC 2. Certain principles, for example, PCI-DSS 6.6, can be fulfilled distinctly using a confirmed WAF. Doing as such, in any case, doesn’t make pen testing any less helpful because of its previously mentioned advantages and capacity to enhance WAF setups.
HOW OFTEN YOU SHOULD PERFORM PENETRATION TESTING.?
Organisation should perform pen testing routinely – preferably, when a year – to guarantee more predictable organization security and IT management. As well as directing administrative commanded examination and appraisals, penetration tests may likewise be run at whatever point an association:
run at whatever point an association:
. adds new network framework or applications;
. makes critical overhauls or adjustments to its applications or framework;
. sets up offices in new areas;
. applies security patches; or
. modified end-user policies.
However, on the grounds that penetration testing isn’t one-size-fits-all, when an organization ought to take part in pen testing additionally relies upon a few different variables, including:
. The size of the organization. Organizations with a bigger presence online have more assault vectors and, accordingly, are more-appealing focuses for hackers.
. Penetration tests can be expensive, so an organization with a more modest financial plan probably won’t have the option to direct them every year. An association with a more modest spending plan may just have the option to direct a penetration test once every two years while an organization with a bigger financial plan can do penetration testing once every year.
. Guidelines and consistence. Associations in specific ventures are legally necessary to play out certain security tasks, including pen testing.
. An organization whose foundation is in the cloud probably won’t be permitted to test the cloud provider’s infrastructure. Notwithstanding, the provider might be directing pen tests itself.
Penetration testing endeavours ought to be custom-made to the individual organisation just as the business it works in and ought to incorporate development and assessment undertakings with the goal that the vulnerabilities found in the most recent pen test are note revealed in after tests.