Operational security (OPSEC) is a risk management and security process that keeps sensitive data out of the wrong hands.
A technique that identifies seemingly harmless behaviors that could mistakenly divulge essential or sensitive data to a cybercriminal is another OPSEC definition. OPSEC is a strategy and a method that encourages IT and security professionals to look at their operations and systems through the eyes of a possible attacker. Analytical activities and processes include behavior tracking, social media monitoring, and security best practices.
The use of risk management to find potential risks and vulnerabilities in organizations’ operations, how they function, and the software and hardware their personnel use is an integral part of OPSEC. Looking at systems and processes from the perspective of a third party allows OPSEC teams to uncover concerns they may have missed, which is critical for installing the necessary countermeasures that will keep their most sensitive data safe.
What role does OPSEC play ?
Federal departments, such as the Department of Defense, have now adopted the OPSEC approach to preserve national security and trade secrets. It’s also utilized by businesses that wish to protect their customers’ information, and it helps address corporate espionage, information security, and risk management.
What is the significance of OPSEC?
OPSEC is significant because it pushes firms to examine security risks and identify potential vulnerabilities that a traditional data security strategy would miss. IT and security teams can use OPSEC security to fine-tune their technical and non-technical processes while lowering their cyber risk and protecting themselves from malware-based attacks.
To avoid the unintended release of classified or sensitive data, a robust OPSEC program is critical. It allows businesses to keep the details of their future operations, capabilities, and goals hidden from the public eye. However, it is crucial to understand what this information is about, where it is stored, what level of protection it has, what the consequences would be if it were compromised, and how the organization would respond.
Attackers may be able to wreak significant damage if such information is disclosed. Employees who reuse their login credentials across several internet platforms, for example, may be able to launch more extensive cyberattacks and perpetrate identity fraud or theft.
Operational Security in 5 Steps
OPSEC is a five-step method that allows businesses to safeguard their data processes.
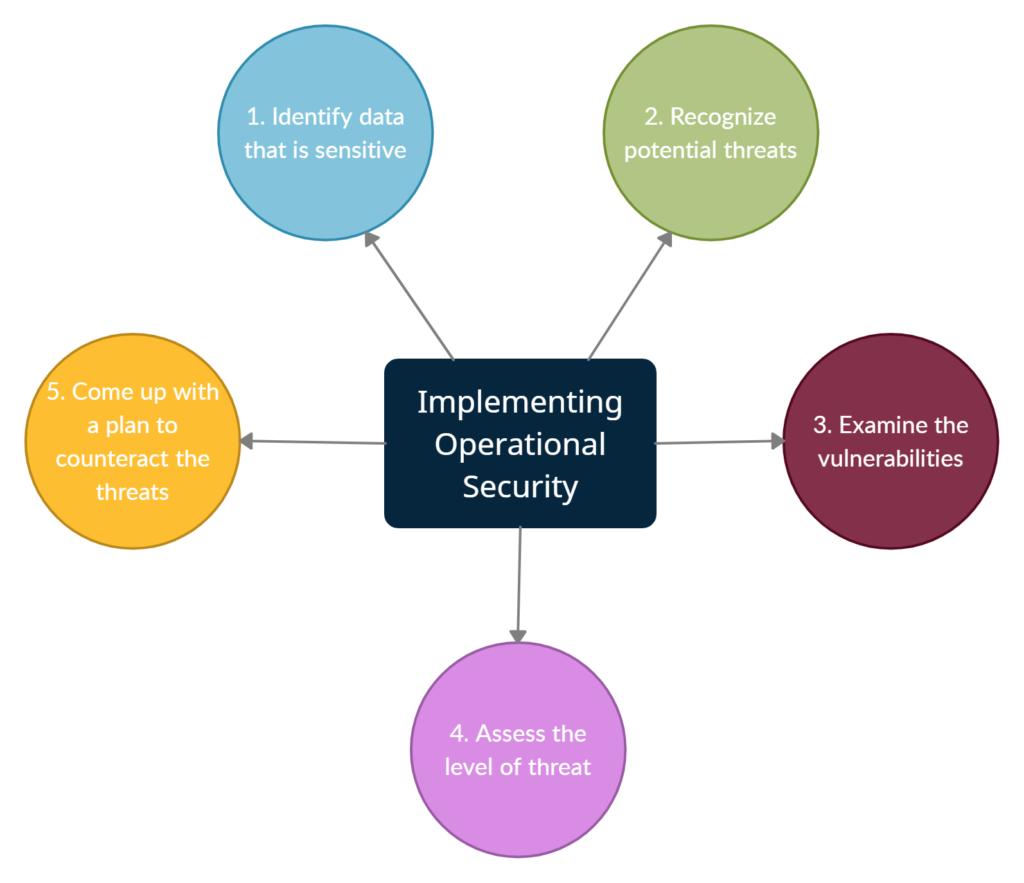
1. Identify data that is sensitive
Understanding what data businesses have and what sensitive data they maintain on their systems is the first step in ensuring OPSEC security. Customer information, credit card information, employee information, financial documents, intellectual property, and product research are all examples of information identification. Businesses must concentrate their resources on safeguarding this vital information.
2. Recognize Potential Threats
Once sensitive data has been identified, companies must assess the threats this data may face. Insider threats or malicious insiders, such as disgruntled workers or negligent employees, include third parties who may want to steal the data, competitors who may gain an advantage by stealing information, and insider threats or malicious insiders disgruntled workers or negligent employees.
3. Examine Vulnerabilities
The next step is for organizations to assess the potential gaps in their security defenses that could allow the threats to materialize. This entails evaluating the processes and technology solutions in place to protect their data and detecting any vulnerabilities or flaws that attackers could exploit.
4. What is the level of threat?
After that, each identified vulnerability must be assigned a threat level. The vulnerabilities should be prioritized based on the likelihood of being targeted by attackers, the severity of the harm if exploited, and the time and effort required to mitigate and restore the damage. The greater the potential for damage and the greater the likelihood of an attack, the greater the resources and priority that organizations should devote to minimizing the risk.
5. Make a plan to counteract the threats.
This data gives businesses everything they need to create a plan to counteract their discovered hazards. Putting countermeasures in place to minimize threats and manage cyber risks is the final step in OPSEC. Typical examples are updating technology, adopting procedures to protect sensitive data, and offering employee training on security best practices and corporate data regulations.
An OPSEC process plan must be easy to comprehend, implement, and follow, and it must be updated as the security threat landscape changes.
Operational Security best practices
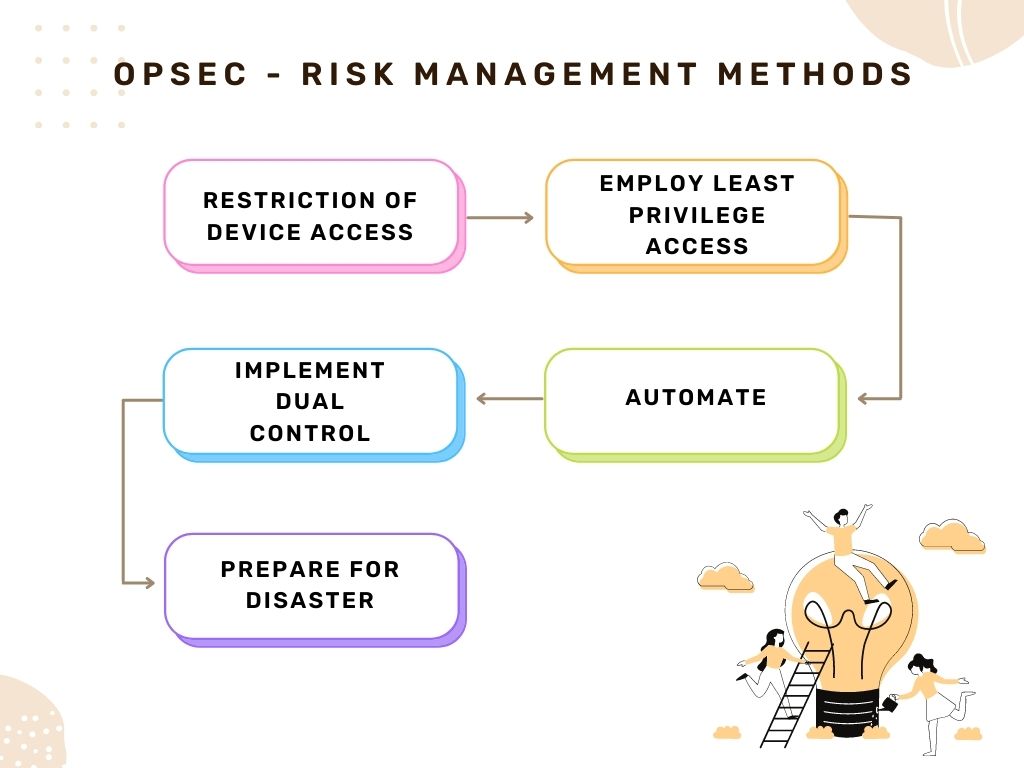
OPSEC uses risk management methods to identify potential threats and vulnerabilities before they are exploited and cause difficulties for businesses. Following these best practices, businesses can develop and implement a thorough and robust OPSEC program:
Organizations must develop specific change management practices that their employees can follow if network changes are made. Organizations must be able to audit and monitor these modifications if they are to be managed and logged.
Restriction of device access: Organizations must limit network access to only those necessary devices. Military agencies and other government organizations use the “need to know” principle to protect their networks, and same philosophy must also be extended to corporate networks. Network device authentication should be utilized as a general rule of thumb regarding access and information exchange.
Employ least privilege access: Employees should be given the bare minimum of data, network, and resource access required to accomplish their tasks well. This entails implementing the principle of least privilege, which assures that any program, process, or user has only the privileges necessary to do its task. This is critical for enterprises to improve their security levels, minimize insider threats, reduce the attack surface, reduce malware risk, and improve audit and compliance readiness.
Implement dual control: Users in charge of network management should not be in charge of security. Teams or individuals in charge of maintaining business networks must be kept distinct from those setting security policies.
Automate: Humans are frequently the weakest link in a company’s security systems. Mistakes, data mistakenly ending up in the wrong hands, key details being neglected or lost, and critical processes being circumvented can result from human error.
Prepare for disaster: Preparing for disaster and a sound incident response plan are essential components of any security defense. Even the most robust OPSEC protection must be backed up by strategies that detect possible threats and spell out how a company will respond to cyberattacks and mitigate the resulting damage.
OPSEC Personal Security Checklist
– For authentication:
1. Use a password manager to encrypt, store, and fill credentials, and use a lengthy, and unique password for each account.
2. Where possible, use two-factor authentication and utilize an authenticator app or hardware token.
3. Sign up for breach notifications and change the passwords on any accounts that have been compromised.
– Browsing Requirements:
1. Use a browser that prioritizes privacy, Set your default search engine to a non-tracking engine, and avoid entering any information on a page that isn’t HTTPS.
2. Using a plugin, you can block unwanted third-party trackers and advertisements.
3. Allowing your browser to save passwords or auto-fill personal information is a bad idea (instead, use a password manager)
– For the telephone:
1. Set a device PIN, preferably a long one. Configure fingerprint authentication if possible, but don’t use face unlock.
2. To protect your data from physical access, encrypt your device.
3. Make sure your gadget is up to the current date. Patches for recently revealed security vulnerabilities are frequently included in system updates. When requested, you should install updates.
4. Examine the app’s permissions. Access permissions should not be granted to apps that do not require them.
5. Disable any networking capabilities that aren’t in use, and ‘forget’ any Wi-Fi networks that aren’t in use.
– Email Addresses:
1. Enable 2FA and use a lengthy, strong, and unique password.
2. Consider using secure and encrypted email services. Use an email aliasing service to protect your actual email address. This allows you to keep your real address hidden while still receiving all messages in your primary inbox.
3. Disable automatic remote content loading is commonly used for thorough tracking but can also be harmful.
– In the case of networks:
1. Use a trustworthy VPN to encrypt your IP and restrict the amount of browsing data your ISP may keep track of, but be aware of their limitations.
2. Change the default password on your router. Anyone connected to your Wi-Fi can listen to network activity, so use WPA2 and choose a strong password to prevent strangers from connecting.
For any personal or business related cybersecurity issues, please visit: https://www.benchmarkitservices.com/cyber-security/

