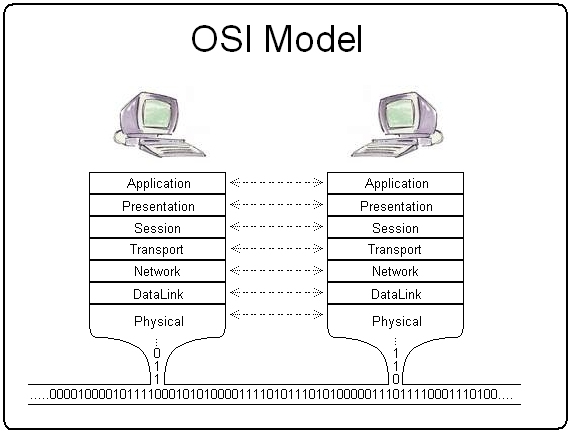
What exactly is OSI Model?
The Open Systems Interconnection Model (OSI Model) is a theoretical framework for describing the functions of a networking system. In order to facilitate interoperability between diverse devices and applications, the OSI model describes computing functions into a universal set of rules and standards. The connections between computing systems are divided into seven abstraction levels in the OSI reference model: Physical, Data Link, Network, Transport, Session, Presentation, and Application.

The OSI Model can be thought of as a universal computer networking language. It’s based on the idea of breaking down a communication system into seven abstract layers that are piled on top of each other. The OSI was published in 1984 by the International Organization for Standardization at a period when network computing was still in its infancy (ISO). The OSI Model is still used to explain network architecture today, even if it does not always map exactly to real systems.
Why OSI MODEL?
There are many reasons to use the OSI model some of them are,
- The OSI model is effective in helping you determine where the biggest data security threats are inside your business since it provides a framework for doing an inventory of your organization’s assets. Knowing where the majority of your company’s data is held, whether on-premises or in cloud services, will help define your information security policy. You can invest in the correct solutions that provide you data visibility within the relevant OSI levels once you have this knowledge.
- For decades, the OSI model has been used to help IT professionals understand networking and handle problems that might occur at any point during the networking process. As a result, it’s still useful for infosec professionals conducting asset inventories today. Using the multiple levels, you may categorise your physical assets, any data you might have on your organization’s networks (and how it’s protected), and an inventory of which applications your employees use to access your data and resources. The approach can also assist you in addressing vulnerabilities and security issues according to the levels they touch.
- Given how valuable the OSI model is for inventorying security resources and assets, it’s no surprise that using it when shifting to the cloud might be beneficial. This is because the OSI model will assist you in determining the exact types of data security concerns that cloud adoption may pose to your business. This enables you to make more informed decisions about the cloud systems you use.
- Several experts have developed “updated” OSI models that reflect operational layers in IaaS and cloud architecture (featured as images below). While the OSI system layers can be applied in a variety of ways to cloud architecture, it’s evident that the model is conceptually flexible. With this in mind, it may be worthwhile to examine your own cloud architecture and determine whether designing a modified OSI model for your surroundings might enhance your security programme.
- The OSI Model is still very useful for debugging network problems, even if the modern Internet does not fully follow it (it instead follows the simpler Internet protocol suite). The OSI Model can assist break down a problem and find the cause of the trouble, whether it’s one individual who can’t get their laptop online or a web site that’s down for thousands of users. A lot of unneeded work can be avoided if the problem can be focused down to one specific layer of the model.
OSI LAYERS:
Let’s take a look at the OSI layers from the application layer, which serves the end user directly, all the way down to the physical layer.
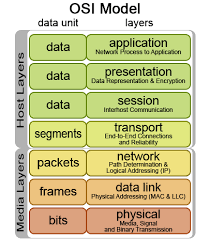
7. Application layer: This is the sole layer that interacts directly with user data. Web browsers and email clients, for example, rely on the application layer to establish communications. Client software programmes, on the other hand, are not part of the application layer; rather, the application layer is in charge of the protocols and data manipulation that the software uses to provide meaningful data to the user. HTTP and SMTP are examples of application layer protocols (Simple Mail Transfer Protocol is one of the protocols that enables email communications).
6. Presentation layer: Layer 6 is primarily responsible for preparing data for use by the application layer; in other words, layer 6 makes data presentable for application consumption. Data translation, encryption, and compression are all handled by the presentation layer. Two gadgets that communicate Because different encoding methods are used while communicating, layer 6 is in charge of converting incoming data into a syntax that the receiving device’s application layer can understand.
5. Session layer: This layer is in charge of establishing and maintaining communication between the two devices. The session is the period of time between when a communication is initiated and when it is ended. The session layer guarantees that the session remains open for as long as necessary to send all of the data being exchanged, and then swiftly ends it to avoid wasting resources. Data transport is also synchronised with checkpoints by the session layer.
4. Transport layer: The end-to-end communication between the two devices is handled by Layer 4. Before transferring data to layer 3, data from the session layer is broken up into segments and sent to layer 3. The receiving device’s transport layer is in charge of reassembling the segments into data that the session layer can ingest. Flow control and error control are also handled by the transport layer. Flow control establishes the best transmission speed to prevent a sender with a fast connection from overwhelming a receiver with a sluggish connection. On the receiving end, the transport layer conducts error control by checking that the data received is complete and requesting a retransmission.
3. Network layer: The network layer is in charge of making data transit between two networks easier. If the two communicating devices are on the same network, the network layer isn’t required. On the sender’s device, the network layer breaks up segments from the transport layer into smaller pieces called packets, which it then reassembles on the receiving device. Routing is a function of the network layer that determines the optimum physical path for data to take to reach its destination.
2. Data link layer: The data connection layer is similar to the network layer in that it allows data to be sent between two devices on the same network. The data link layer decomposes packets from the network layer into smaller units known as frames. In intra-network communication, the data link layer, like the network layer, is responsible for flow control and error control (The transport layer only does flow control and error control for inter-network communications).
1. Physical layer: The physical equipment used in data transfer, such as cables and switches, are included in this layer. This layer is also where data is turned into a bit stream, which is a string of 1s and 0s. Both devices’ physical layers must agree on a signal protocol so that the 1s and 0s can be identified on both devices.
You can easily get “Computer Repair Onsite (CROS)” support by clicking here if you want to know more about or help your organisation’s use of this process.

Advantages of OSI Model:
- It is a generic model that may be used to guide the development of any network model.
- It employs the divide-and-conquer strategy. All of the services are separated into tiers. As a result, administration and maintenance of this OSI model architecture are simple and basic.
- The abstraction principle is followed in this tiered architecture. Changes in one layer have little effect on the other levels.
- Having all services packed in a single layer is less secure and versatile.
- It’s a multi-levelled model. Changes to one layer have little effect on the other levels if the interfaces between them do not alter dramatically.
- It clearly distinguishes between services, interfaces, and protocols. As a result, it is adaptable. Depending on the nature of the network, each layer’s protocols can be easily modified.
- Both connection-oriented and connectionless services are supported.
Disadvantages of OSI Model:
- It’s merely a theoretical model that ignores the availability of suitable technologies. This makes it difficult to put into practise.
- It doesn’t specify any specific protocol.
- It may be challenging to incorporate a new protocol within this model at times. This is due to the fact that this model was designed before any of these protocols were invented.
- The session layer is used to manage sessions. User interaction is handled by the presentation layer. They are useful, although not as much as the OSI model’s other levels.
- At several stages, there is some service duplication. Error control mechanisms exist in both the transport and data connection layers, for example.
- Interdependence exists between the layers as well. These layers are unable to work in tandem. They have to be in wait to receive data from its predecessor.
- The launch of this model occurred at an inopportune time. TCP/IP protocols were already in place before OSI was introduced. As a result, businesses were hesitant to employ it at first.
- The OSI model is extremely complicated. The initial implementation was inefficient, slow, and expensive.
Conclusion:
The primary idea behind OSI is that the process of communication between two endpoints in a telecommunication network may be separated into seven discrete sets of related functions, or layers, with layer one at the bottom and layer seven at the top of the layer stack. The protocol stack receives data from software at layer 7, which is the application layer. A service data unit is assigned to the information received (SDU). Each layer adds a header to the SDU that is specific to that layer. As each tier adds its header, a payload data unit is created (PDU). The PDU is subsequently transmitted to the layer below, where it becomes the layer’s SDU. The data is transferred via the network media after the physical layer, layer 1, gets the PDU from the data link layer, layer 2. We can learn more about all the data related topica like data security, data storage and many more with the team of experts “BENCHMARK IT SERVICES”. You can access the website here