Phishing is a method where the cyber criminals steal the confidential data such as online banking logins, credit card credentials and also passwords by sending fraudulent messages called lures.
So, usually most of the times phishing attacks happen when we receive an unknown email with some sort of attachment or a link with it. If we unknowingly try to download the attachment or click the link, then it might allow the attacker to steal the confidential information and also obtain control over the system.
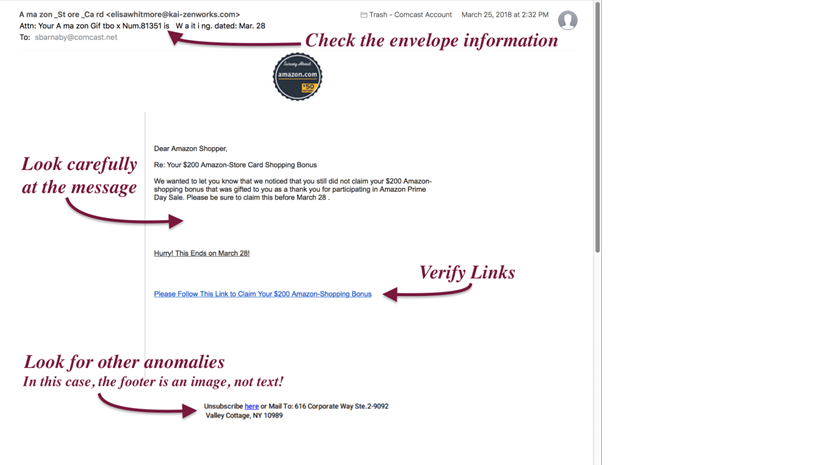
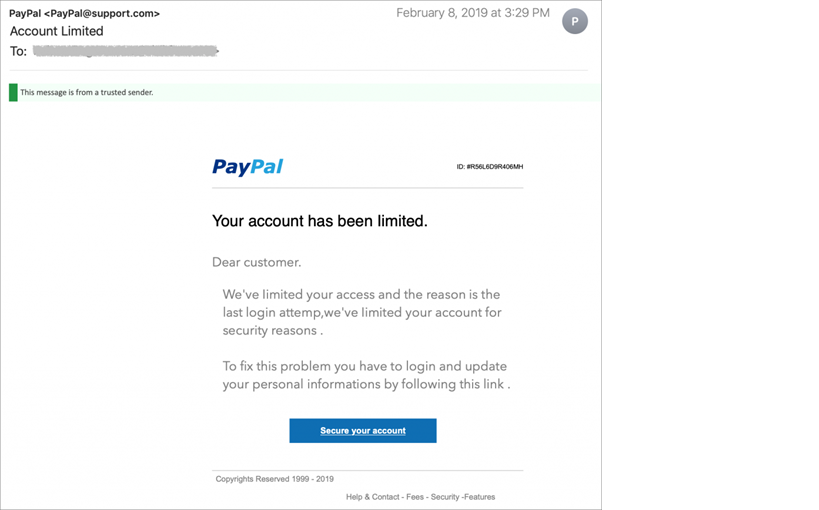
The above images are examples of a phishing email. If we select the “Secure your account” option or click on the link, we might fall victim to phishing attacks.
Spear Phishing
This is the most dangerous phishing messages. These messages are so well written that is too hard to recognise whether if it’s a genuine message or fake.
For example, you may receive a fake email from your companies IT support asking you to change your login credentials and they might send a link through an email. They ask us to click on the link to change our credentials. If we do that, we might be exposing our credentials and it’s a huge risk.
The most commonly copied brands or the organisations are:
- The Australian Taxation Office (ATO): This is the most commonly copied organisation and there is a high probability of receiving a phishing email by using the name of the ATO in Australia. They either make calls or send an email and try to make us reveal our TFN number which is confidential. Once revealed it can be used for various crimes, so we need to be cautious while dealing with this kind of attack.
- Banks: The other most commonly copied brand is banks. As most people use banks to save their money, the cyber criminals target the customers requesting them to update their information or offer them some rewards and make them reveal their account numbers.
- Telecommunication services such as fines overdue and also issue fake bills.
The ways to prevent phishing in an enterprise/organisation environment are:
- Training and education for the staff: Need to train the staff about the spam emails. Need to show them some spam emails received previously and make the cautious. This helps organisation a lot in preventing the phishing attacks.
- Let them know the most common ways to identify if it is a suspicious email such as:
- Urgent call to action.
- Unknown, first time or unusual sender.
- The domain of the email doesn’t match the organisation.
- Suspicious links or attachments.
- Secure accounts and access: Encouraging the employees to use strong passwords and keep changing them regularly. Should also recommend them to use multi-factor authentication so that the device and the data is secured.
If an employee receives a suspicious email, then:
- Report it and the cybersecurity department will take care of the issue.
- Try to do a hard delete of the email.
- Try blocking the sender, so that you won’t receive any emails further from the same sender.
- Try not to click on any suspicious links.
There is also some standard policies which have been set by the companies that, they are not allowed to call a employee or anyone via phone or email to:
- Ask for the passwords, Pin numbers and the security questions.
- Ask to confirm the confidential or personal information such as Credit card numbers or bank account details.
- Asking for some kind of payment to be done.
If an employee receives an email or call asking for the above mentioned things then he need to be aware that this is a phishing email and need to report the incident in order to prevent it.
What needs to be done by the organisation to avoid such phishing emails?
- Installing Security software: This is often considered as the first line of defence because, if we have a security software, then it might block the phishing email from being delivered.
- Keeping the software updated
- Enforcing password policies: This includes setting up some rules while creating a password such as minimum length of the password, the special characters which can be used, etc. to make it complex.
- Allowing the use of multi-factor authentication.
How to check the email header for phishing emails?
Basically, every email has three components in it: envelope, header, and the message. The envelope is not always visible, and the message is where we put in the actual message. Header is visible to sender and the recipient.
The header consists of details such as sender, receiver, date, and subject. It also shows us the security checks it has passed before receiver has got the email.
In order to know if it is a phishing email or not, we can check if:
- The sender address and domain matches or not: if it doesn’t match them, it is a phishing email.
- Email travel path and the email client.