Abstract
Phone calls play an integral part in the communication from ages and this channel has been compromised by attackers over the years to perform their vicious attacks. Cybersecurity attacks have always been persistent and attackers have always found a way to exploit vulnerabilities in networks, computers and mobile devices. Phishing attack is a Cybersecurity attack where attackers pretend to be from any legal organization and then steal banking details, Credit card details from customers. Vishing Attack is a type of Phishing attack where attackers lure customers or users to give out their details but on phone. Many customers over the years have been victimized by attackers and it still continues to persist because of newer ways that attackers tend to find to masquerade themselves as others.
Introduction
Vishing or Voice over IP Phishing attack can be defined as an attack where financial information, usually banking details or credit card details, is gained by attackers by luring them with false offers, misinformation or pretending to someone else (masquerading). Most of the people, including myself, have received a call from an unknown caller where some offers have been provided in order to reveal the information of banking, debit-cards or credit cards. There are numerous ways which are used by attackers to make the customers reveal their important financial information like cancellation of debit card/ credit card, enticing offers etc. which are discussed in the next section. There are numerous ways Vishing attacks are performed which will be discussed in latter parts. Even after so much awareness created by companies, organizations but still the gap has not been bridged. A movie called Compliance dealt into similar subject but still attackers have outsmarted customers with their enticing offers
Vishing Scams
There are myriad of ways which attackers use to perform vishing attacks and after COVID-19, these attacks have even increased further. Some of the ways which attackers use to perform this attack are as follows:
- Cancellation of Credit/ Debit cards- Masqueraders call the customers to provide false information that their Credit/Debit card will be cancelled until or unless they provide information of the current card.
- False Offers- Attackers call customers to entice them with some offers and if the customer gets lured into the offer then credit/debit card information is asked to be given.
- Income Tax Scams- Attackers pretend to be from Tax department and fear the customer that they have not paid their taxes and if not paid over certain period in a particular account, there would be consequences.
- Post Pandemic Offers- After pandemic started, many people received number of offers that they are eligible for certain amount of payment from government and in order to gain it, financial information needs to be revealed.
In all four ways mentioned above, attackers manipulated different emotions which the customer withheld and used it to gain financial information.
How Vishing is Performed
In order to understand how threat of Vishing is performed, following image visualizes that.
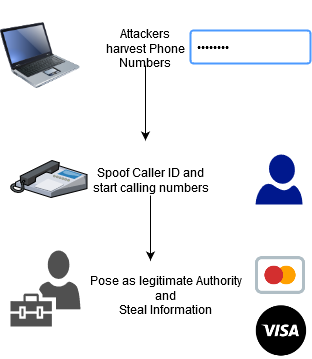
In the figure shown above, it is depicted that attackers first gather phone numbers and harvest them using various sources. In next step, attackers call users and then in last step they impose themselves as legitimate authority and steal information.
Identification of the Vishing Attack
There is plethora of ways which attackers might use to perform the Vishing attack. There are some ways which can be used to identify whether the call received is an impersonator or a legitimate organization which are mentioned below:
- Caller claiming to be Medicare, Internal Revenue Service or Social Security Administration- If a user/customer requests to be contacted from these companies then they would contact them, otherwise these companies do not call specially to ask for any financial details.
- Sense of urgency- As mentioned before that attackers manipulates emotions of customers and if they are invoking fear of arresting/suspension and asking to act urgently then the claimer is an impersonator. The reason behind being is that these matters have legal processing and are not resolved on phones in an urgent manner.
- Asking for personal information- The callers if asking for any information related to account numbers, credit card numbers, social security numbers are mostly impersonators because banks or organizations do not require this information.
Protection from Vishing Attacks
As learned from identification techniques, there are some ways which are often used by the attackers to impersonate and receive information from the callers. There are some techniques which can be used to protect from phishing attack.

- Black listing of calls/ Applications- Installation of applications like trucaller in order to black list calls.
- Reaching to Benchmark IT Services to know about solutions and preventive measures.
- Hanging up the phone if banking details are asked.
- Creating awareness among people so that they can identify difference between impersonators and legit callers.
- Never revealing any financial information or personal information to any caller.
- Verifying the identity of the caller by asking more about the company/organization.
- Using Benchmark IT Cloud services, so that phone numbers are not accessed or harvested by callers.
Recovery from Vishing attack
If by any chance, the customer is able to reveal any financial information to a vicious caller then strict measures needs to be taken which are as follows:
- If Credit/Debit card information is released during the call then the user must freeze its cards so that the attacker cannot steal any money.
- Reaching out to Benchmark IT Services, so that the damage can be minimized.
- Reaching out to the bank so that bank can freeze accounts or any transactions.
Conclusion
Vishing attack is very common and has been a major weapon used by attackers to steal information. Everyday people receive scam phone calls which and become victims to this attack. Attackers manipulates emotions of customers by fearing them, exciting them with offers so that they would reveal their financial information. The best way to avoid Vishing is to just ignore or hang up the call but still people have been victimized because of lack of awareness among people. There are methods which customers can make use of in order to prevent Vishing attack from happening.

