Hello Everyone today I would like to discuss regarding Virtual Private Networks(VPN) to access organization network drives to keep your system secures at the same time
Virtual:
Virtual define snort real or different state of objects which art associated with communication data structures, the communication between two or more devices in public network communications are associated with virtualization-based on data entity.
Private
The private network consists of secret data structures where all the network access credentials and communication between two devices are authorised with efficient data communication technologies and the exchange of information’s are carried out between to network transmission protocols.
Network
The network data transmission consists of two or more devices with all the electronic applications and communication data storage devices are virtualized to with VPN network interconnections.
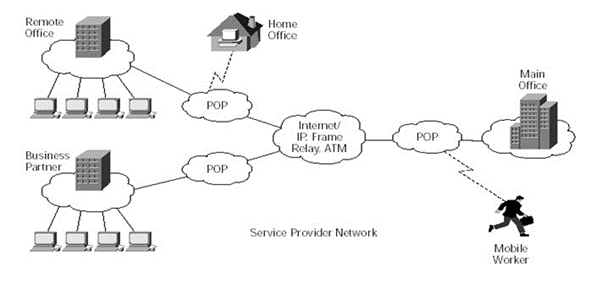
The virtual private network access consists of all the remote control in operations and connectivity through PSTN switches. The communication routing and network configuration are of IP addresses define the database network communication protocols were all the considerable amount of resources and expandable complex private networks are deployed with efficient interact system transitions.
The network division and the network data frames are allocated to improve frame relay functionalities where all ATM processing and network management systems are authorised with remote controlling uses and all mobility working management functionalities are used with remote and supplementary data systems. Small and medium scale companies are deployed with efficient switching transition protocols where all the communication of internal and external links is authorised to create efficient flow management capabilities.
Categories of VPN network
- Trusted VPN network devices are associated with the least circuits mechanism where all the service providers are associated with communication without network interpretation.
- Secure VPN network systems are associated to analyse the issue of users and create encryption and decryption mechanism to ensure safety and customer Management capabilities.
- Hybrid virtual pin network access consists of secure and trust-based data transmission because all these Network interconnections and service providers of internet protocols are associated to create efficient trust prospective design.
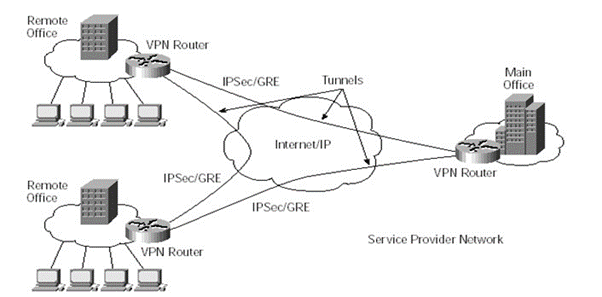
VPN topology
The VPN topology is interconnected with network communication where all the least ISP data transition helps us to create efficient methods of data interconnection system. The capability of design router are switches are interconnected to provide access of original network communications were all VPN devices are associated with the permanent virtual circuits systems and assemble all the dedicated single user circuits with an IP packet and router switching mechanism to send or receive the data network capabilities.
The capability and network interconnection of users are deployed with service provider management functionality is there all sending or receiving of messages are associated with original packet transmission systems. There are different layers of open system Internetworking with all these frameworks as associated with Ethernet data transitions. All the communication and tunnelling protocol as associated with efficient network communication protocols were all these virtualization-based acted with remote controlling possibilities.
- Tunnelling routing protocols.
- Point to point tunnelling protocol.
- Multiple label protocol system.

Types of VPN
1. Remote access
The remote access Data Structure will enable all mobile users and interconnect devices with efficient infrastructure management capabilities because internet service providers will allow corporate authentication systems to create efficient user access applications. The Network authentication and public telephone services are associated to create efficient integrated service digital network systems. All the applications of digital subscribers and routing applications are carried out with unique measurements and create efficient authentication processing system.
- The capability of reduction of capital cost investments with mobile and terminal servers are used with virtual access.
- The capability of scalable Management functionalities is authorised with efficient user access network system.
- Long distance telecommunication systems are reduced with efficient routing protocols which will interconnect all the modem transition.
Intranet VPN
The capability of virtual circuit networks is authorised with the interconnection of an office network switch is all the internet services and service provider IPS are associated with frame relay functionalities. WAN infrastructures are accessed with IP management functionalities were all traffic tunnels across the network systems will create a benefit of interact VPN.
- The application will reduce WAN bandwidth.
- Deficient usage of cost with bandwidth functionalities are associated with flexible topology management system.
- Conjugation of network systems and avoidance of correlation with bandwidth are associated to create an efficient flow of the virtual private network.
Click here to Purchase IT Hardware or Software
Components of virtual private network
The components of virtual private networks are associated to increase reliability and manage all the sources of enterprise functionalities because security authentication is most important. The application will provide solutions with platform scalable devices and provide an incrementation of requirements and resource technologies where all the configuration is access to with enterprise data systems.
1. Security
All the companies of virtual private networks are interconnected with security systems and the unauthorised users could not access the network protocol.
- IP security network systems.
- Point to point tunnelling protocol interconnections.
- Multipoint label switching system.
- Encryption of standardized algorithms.
All the standardized applications are associated to improve the strategy of tunnelling management systems were sending and receiving of entire data transfers are associated to handle internet packet exchange systems which are based on input and output of extendable user-defined functionalities.
Appliances with instruction detection firewall
All firewalls and monitoring applications are associated with network parameters and create the protection of enterprise management technologies where unauthorised could not access the network application. The data systems of the organisations and design of firewalls will interconnect all the applications and create an efficient packet level firewall with the application level management system.
- The packet level firewall system will check for the source and destination address of all the packet Transformers and these are applied in network data interference.
- Application level firewalls are associated with host computer database systems and create a network with efficient login permit credentials.
VPN benefit
- Extended geographic connectivities will have a remote controlling operation with centralised resources.
- Boosting of all the industrial propagation will improve productivity and eliminate the time-consuming mechanism.
- Improve internet security systems with a wide range of network vulnerability.
- Scalable infrastructure allows communication methods with efficient network flow.
VPN with QoS
The quality services of VPN systems are most important in network topology because it consists of a high level of security and creates encrypted standard with firewall mechanism which is all the internet applications and geographical tunnelling systems are associated to increase the accessibility of network interference.
Click here for Data Security Issues
If you have any questions then feel free to put your comments. I will be back soon with another interesting topic that will help all of you to understand technology better.

