Abstract
Kali Linux is a Debian-derived Linux Operating System which is mostly used for Penetration testing tools and Digital Forensics. If a user wants to learn about how to use tools like John the Ripper or metasploit and also want to edit files or make presentations then Kali Linux is the best platform to use. But usually, Windows or Macintosh users find it very difficult to transition from their current operating systems to Debian-derived operating systems. With the use of commands mentioned in this blog, users would be very comfortable to get hang of Kali Linux and continue to use it for penetration testing or digital forensics.
Introduction
Kali Linux has so many tools preinstalled in it and it being free of cost makes it one of the best operating systems. Users in the beginning finds it very hard to use Debian-derived Operating Systems like Linux mint and Kali Linux. The reason behind users finding difficulty being reliant on commands instead of using services from folders or desktop. Even there are options to use Kali from folders, desktop but sometimes privileges can stop users to make changes. Moreover, most of penetration tools require usage of commands in the terminal, thus it is better to get hang of commands which are mentioned in the next sections. If a user wants to still keep using Windows or Macintosh, hypervisors can be used like Vmware or Oracle Virtualbox. A hypervisor or Virtual Machine Manager allows Virtual Machines to be used on the same machine and it has no impact on current operating system. Also, it is advisable to use Virtual machine if penetration testing is learnt since it makes the network private. The useful commands which users can use in order to understand how Kali Linux works are given below.
- Super Privilege
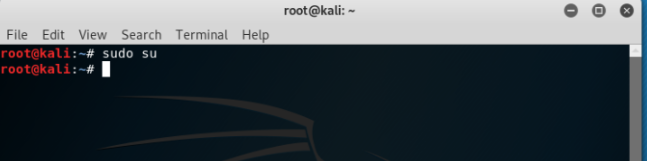
The most important command which a beginner should know is to how to get privileges of a super user or root. Without getting this permission, a user cannot perform most of the tasks on terminal. The command to get root privilege is ‘sudo su’. This will ask the user for the password for the Kali machine and after entering the password, user would gain root privileges as shown below:
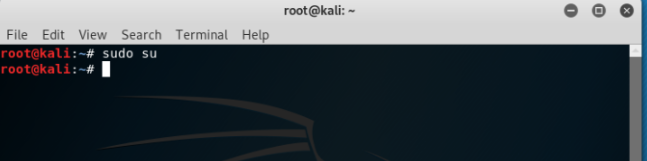
Note: Some Virtual machines already have root privileges but new installed operating systems does not.
2. Whoami
The next command is a very simple command and it gives information about the user. If the user wants to know about which user is currently being in use the command ‘whoami’ can be typed in terminal as shown below:
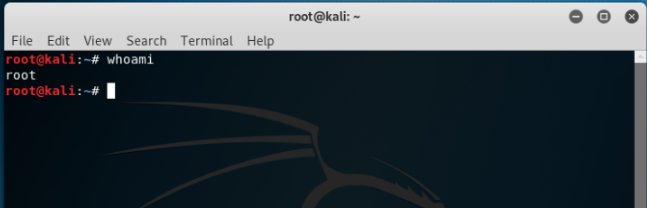
As clear from the above screenshot that the current user is ‘root’.
3. IP Address
The next command is related to IP address. In order to know what the IP address of the machine is then command ‘ifconfig’ is used. This command will give the IP address and also the subnet mask. It will also give the IPV6 address of the machine as shown below:
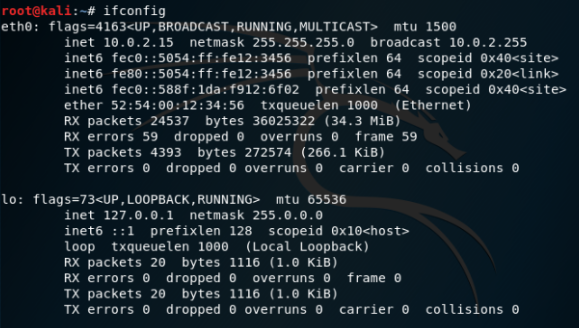
This IP address will be same to the IP address of the original operating system on which Kali Linux is being run on (only applicable if virtual machine is being used). If a user wants to run multiple virtual machine and wants to build a connection between then then in the settings of the virtualbox or VMware, network should be selected as host-only instead of NAT. This will give the virtual machines different IP range and they can connect withe each other.
4. Cd, Ls and Pwd
Next, very important commands but very simple to use are ‘cd’, ‘ls’ and ‘pwd’. When a user enters ‘sudo su’, then user would enter as root@kali. Then if the user wants to go to a folder, desktop, a file then command ‘cd’ is used. If a user wants to enter into downloads then command would be ‘cd Downloads/’. Now if the user wants to list the files which are in a folder then the command ‘ls’ can be used which would list all the files in that folder. First user should go to the folder using ‘cd’ command and then type the ‘ls’ command. If user wants to know the path of any folder or filer then ‘pwd’ command can be used as shown below:
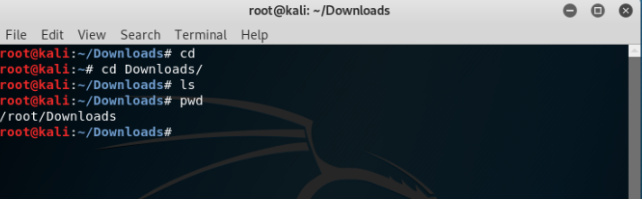
Also, if the user wants to return back to root@kali then user can just type ‘cd’ and it will take the user back.
Note: In Kali Linux, it is important to use capital word depending on how a file or folder is named e.g. in Desktop, D must be capital.
5. Make Directory
The next important command is how to make a directory or a folder. In order to make a directory say named benchmarkIT, the command is ‘mkdir benchmarkIT’ should be typed as shown below:
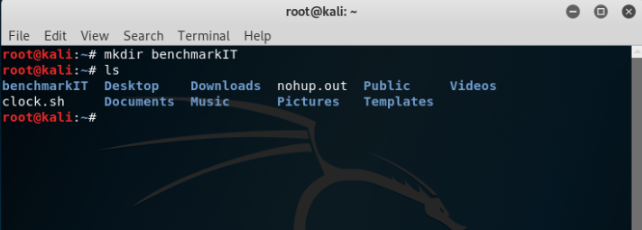
And using command ‘ls’ it can be seen that the directory has been created.
6. Echo and Cat
Next command is adding text to any file or even creating a file. If a user wants to enter a text into any file the command ‘echo’ can be used and outputting it into a either a new file or another existing file. Further command ‘cat’ can be used to view the file, create single or multiple files.
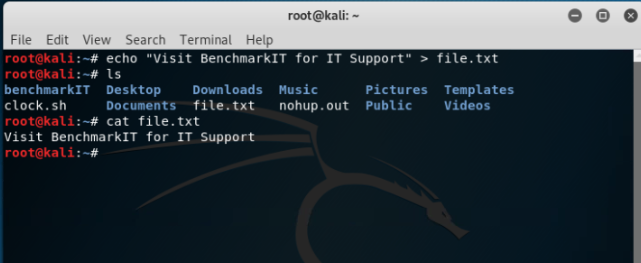
As shown above, a text is entered into fie named ‘file.txt’. Then after using ‘ls’ command it can be seen that a new file has been created and using ‘cat’ command the contents of the files can viewed.
7. Edit file in Terminal
In Kali Linux, a file can be directly edited in the terminal. In order to edit the file, command ‘vi’ with the name of the file is used as shown below:
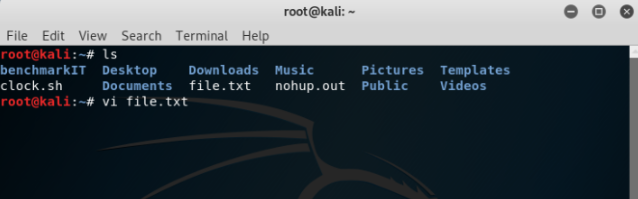
After the command is entered then on terminal the file will open and if the user wants to edit the contents, the user must enter the letter ‘i’ in order to enter editing mode. Then the file can be edited as shown below:
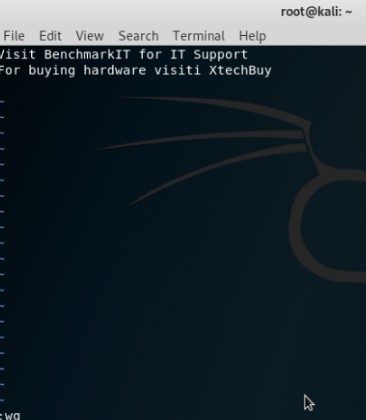
The new text is added but in order to save it and get out of the window can be tricky. In order to save it and edit it, the user should enter ‘escape’ key followed by entering ‘:wq’ which will write into the file and quit it to the main terminal window. Then the file can be checked from the folder where it exists as shown below:
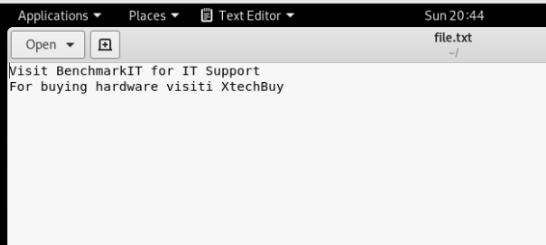
It is evident that the contents has been updated and text ‘For buying hardware visiti XtechBuy‘ has been entered into the file.
8. Copy, Remove and Delete
Terminal can be used to remove, copy and delete files easily. In order to copy a file and paste it into another directory, command ‘cp’ followed by path of where file is located and then where it would be pasted as shown below:
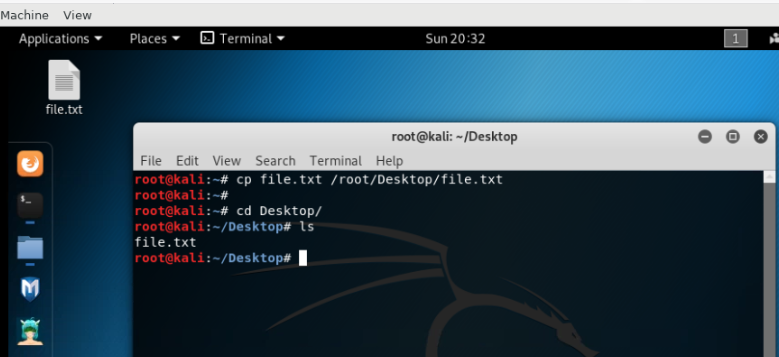
As it can be seen using ‘ls’ command that ‘file.txt’ has been copied to Desktop. Further, the file can be moved to a folder by typing command ‘mv’ with source and destination path as shown below:
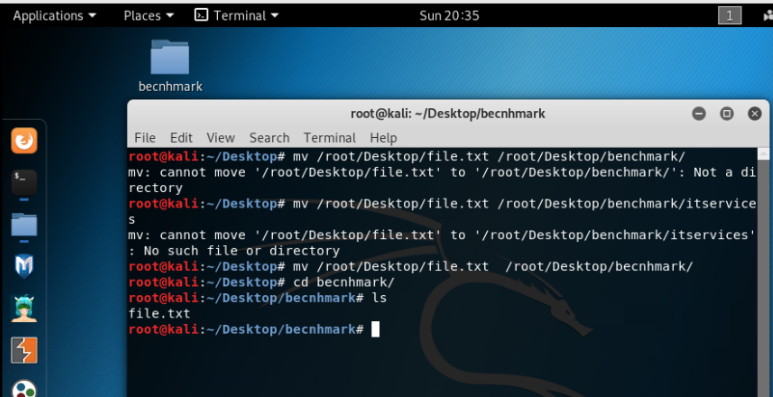
It can be seen from the image above that file has been moved from desktop and is now pasted into ‘benchmark’ folder as shown with ‘ls’ command. Moving further, a file can be easily removed by using the command ‘rm’ followed by the name of the file as shown below:
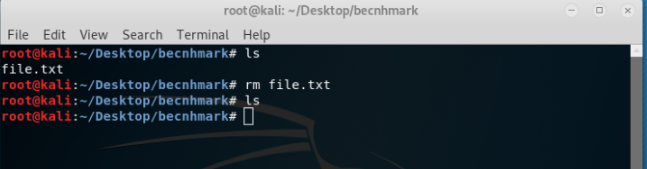
Again, using ‘ls’ command it is evident that the file has been removed from the folder.
9. Changing MAC address
Every machine has a different MAC address and it helps in network addresses while communicating. User can temporarily change the MAC address of the machine which can help in anonymous browsing and it can be done using the command ‘macchanger -r eth0’ as shown below:
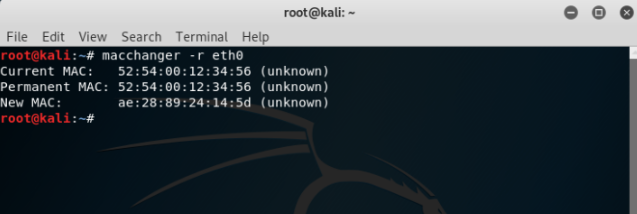
As evident from the image above the MAC address of the machine has been changed but the permanent MAC address remains the same.
Conclusion
Kali Linux can be a little difficult to use in the beginning but when users are able to use commands properly it becomes really easy. It can be a little difficult to remind all the commands but after typing few words followed by ‘tab’ key can give the command or directory which can make it easier to use terminal of Kali. To make foundation, these commands are easy to learn and perform and then later on complex software like Mestaploit can be used efficiently.

2 Comments
Pingback: Different ways to use Kali Linux – Let's Tech It Easy
Pingback: DoS Attack Implementation and Prevention in Ubuntu – Let's Tech It Easy