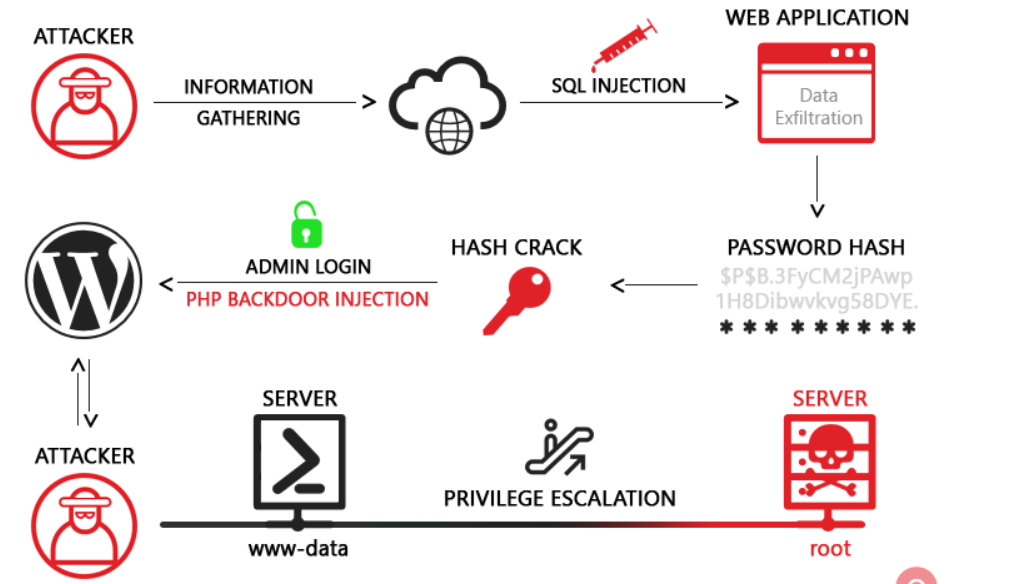
SQL Injection Attack

SQL injection, sometimes referred to as SQLI, is a popular attack method that use malicious SQL code to manipulate backend databases and access data that was not meant to be displayed. Any number of things, such as private customer information, user lists, or sensitive corporate data, may be included in this data. A business could experience wide-ranging effects from SQL injection. A successful attack might lead to the illegal access of user lists, the deletion of entire tables, and, in some circumstances, the attacker obtaining administrative rights to a database—all bad things for a company. The loss of client trust in the event that private information like phone numbers, addresses, and credit card numbers are stolen should be taken into account when estimating the possible cost of a SQLi. Although any SQL database can be attacked using this vector, websites are the most common targets.
The Workings of SQL Injection
A database, which is a computerised repository of information, receives a SQL query as a request to execute some kind of action or function, such as a data query or the execution of SQL code. One such instance is the submission of login information using a web form to grant a user access to a website. This kind of web form is typically made to only allow certain particular forms of information, including a name and/or password. When that data is added, it is compared to a database, and if they match, entry is allowed to the user. If not, access is refused.
Due to the fact that most web forms lack a mechanism to prevent the entry of additional information, potential issues may develop. This flaw allows hackers to send their own requests to the database using the form’s input fields. This could potentially allow them to carry out a range of nefarious activities, from stealing sensitive data to manipulating the information in the database for their own ends.
What results from an effective SQL injection attack?
Passwords, credit card numbers, and other sensitive data can be improperly accessed as a result of a successful SQL injection attack. SQL injection attacks have been the cause of numerous high-profile data breaches in recent years, which have resulted in reputational harm and legal penalties. In some circumstances, an attacker can gain access to a persistent backdoor, which can result in a long-term breach that can go undetected for a long time.
Examples of SQL injection
SQL injection vulnerabilities, attacks, and tactics come in a wide variety and are used in various contexts. Typical instances of SQL injection include:
- Retrieving concealed data, in which case you can change a SQL query to produce more information.
- Altering a query to tamper with the logic of the application, which is subverting application logic.
- Data can be retrieved from several database tables using UNION attacks.
- examining the database, from which you can derive details on its structure and version.
- Blind SQL injection is when you control a query, but the application does not return the results to you.
SQL Injection Attack Types
SQL injection comes in a variety of forms:
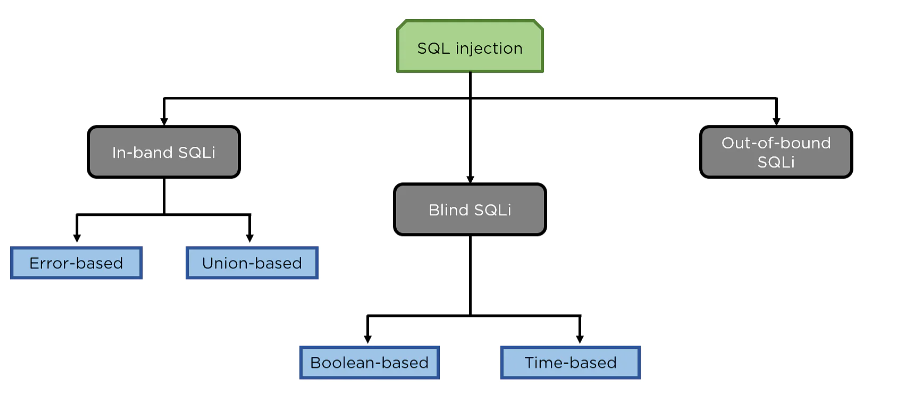
Union Based SQL injection: SQL injection using the UNION command, or union-based SQL injection, is the most common method of SQL injection. In order to retrieve data from the database, two select statements are combined in the UNION statement.
Error-Based SQL Injection: Only MS-SQL Servers can be used using this technique. The malicious user in this attack makes an application display an error. Typically, when you query a database, it responds with an error message that includes the information you requested.
Blind SQL Injection: We extract the data by sending queries to the database in a blind SQL Injection attack. In this attack, the database does not send any error messages. Blind SQL injections can be separated into time-based and Boolean-based categories. Our guide to Blind SQL Injection has more information.
SQLi attacks can also be divided into groups based on how they inject data:
User-input-based SQL injection – Web applications accept input from users through forms, which then send those entries to the database for processing. The web application must sanitise these inputs before accepting them, or else an attacker could insert harmful SQL statement.
SQL injection based on cookies : Using modified cookies to “poison” database queries is another method of preventing SQL injection. In order to perform database activities, web applications frequently load cookies and utilise their data. Cookies could be altered by a malicious user or malware installed on a user’s device to unexpectedly inject SQL.
SQL injection based on HTTP headers: SQL injection based on HTTP headers is also possible thanks to server variables like HTTP headers. Fake headers with arbitrary SQL can insert code into the database if a web application takes input from HTTP headers.
Second-order SQL injection attacks :Second-order SQL injection attacks may be the most difficult to counter since they might go dormant for a long time. Data that is contaminated by a second-order SQL injection attack may be benign in one context but malicious in another. Developers could still be subject to this kind of assault even if they clean all application inputs.
Prevention
Using safe programming methods that render SQL Injections impossible, such as parameterized queries (prepared statements) and stored procedures, is the best solution to stop SQL Injections. These safe functions are currently available for every major programming language, and developers should only use these safe functions when interacting with databases. To further reduce attacks or the effects of successful assaults, developers, system administrators, and database administrators can do the following:
- Maintain the most recent security updates available from vendors for all web application software components, including libraries, plug-ins, frameworks, web server, and database server software.
- When creating accounts to connect to the SQL database, adhere to the least privilege principle(link is external). Do not grant INSERT, UPDATE, or DELETE capabilities to a web site’s database connection credentials, for instance, if the web site simply needs to use SELECT queries to obtain web content from a database. The right database roles for accounts can often be used to manage these privileges. Never enable an administrator connection to the database for your web application (the “as” account on Microsoft SQL Server, for instance).
- Use separate databases for each application or website that you operate.
- Verify user-supplied data for expected data types, not just fields where users can write in information, but also fields with drop-down options or radio buttons.
- Set up the web server and code to properly handle and report errors so that client web browsers are never presented with database error messages. Verbose error reports contain technical information that attackers can use to modify their queries for effective exploitation.
