Abstract
The ransomware attack will transform the information in the dynamic technologies. Individuals and organizations are implemented with the highest level of security methods for all the devices but the optimal protection of data against attacks, these are associated with the capability of functionalities. Ransomware is an attack that never fails to surprise in terms of identifying all the vulnerable attacks, identification of threats and vulnerabilities are associated with the ransomware, application of common attack vectors are associated to provide threats and capability to highlight all the type of malware-based attacks because all the potential threats are recommended to improve a strategy of prevention and protection technologies. The cryptographic ransomware attacks are associated to focus on thread deliverables where all the encrypt of algorithms are associated with communication protocols where all the approaches are deployed according to the behavior of crypto-ransomware management. The network security systems are deployed to detect logical algorithms where all the security controls are associated with malware appearance. The amount of data and time attempt of network management are associated with efficient run some applications where all the incidence and the code acquisitions are associated with runtime packet management system. All the security tools are deployed to reduce the ransomware attack and improve the standardized data management system.
Introduction
Malware is associated with direct and development technologies of the internet of things where all the contributions of large attached are associated with the ransom attacks. The potential interconnectivity of all applications is associated to create vulnerable data systems where all the categories of malware applications will spread worm and inhibits. Locking of system screens are encrypted technologies are associated unless the ransom is paid. The ransomware applications are used in encryption and decryption methodologies where all the critical business applications are associated to monitor the entire applications where the banking credentials are initialized to pay digital cash according to the bitcoin management system.
Bitcoin, encryption technologies consist of efficient methodologies where all the regulated data systems are associated with fund transfer verifications with a centralized banking management system.
Method of ransomware
1. Encryption ransomware
Encryption ransomware technologies will combine innovative and creative algorithms where it intended to block the access of unauthorized users and the file will enquire about ransomware payment criteria to create efficient decryption policies. The encryption of ransomware is associated with a crypto locker
2. Locker ransomware
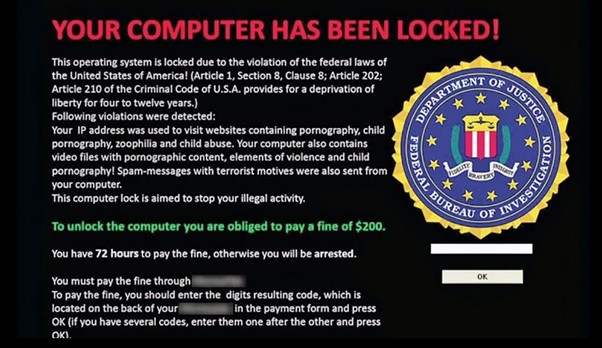
The locker ransomware is a type of malware application where it locks the target out of the entire operating systems and creates a subsequent prevention access system and has an efficient target desktop management system. The ransomware technologies will deploy targeted desktops, applications, and files that are used to create a win locker system.
Ransomware attack vector
Malicious email attachment
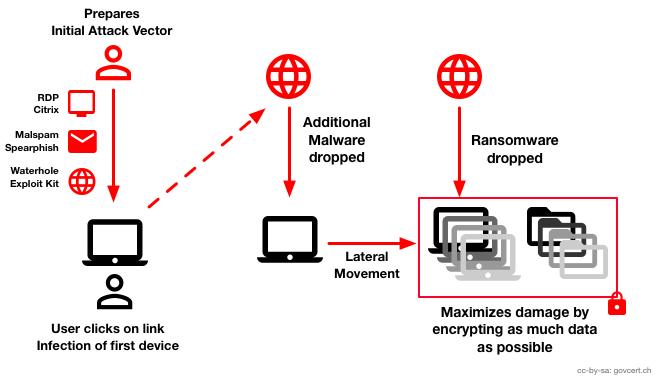
The design technologies of email pretending systems are deployed according to the credible sources of accounting systems where human resource management and information technologies are associated to create efficient Microsoft application technologies. The recipient trust-based management systems are deployed with efficient open source technologies and analyze unknown downloads which are authorized with ransomware infected technologies. [3]
The crypto-ransomware is known as locky filtering systems, the victim system of email configuration and invoice of contributively Microsoft word document are embedded with malicious applications. The macro execution technologies of malware are deployed according to the download application systems where it disables the default of Microsoft word and creates efficient potential with malicious code management technologies.
- The encryption standards are associated with locky extinction.
- The decryption methods are also used to create an extinction of ransomware notes.
- Malicious email links are deployed with a uniform resource locator in the body of email transitions.
- Malicious files that are infected are downloaded into the system and this holds ransom application.
- All the malware attacks are executed according to the possible victims where all the sophisticated tools are used to explore the vulnerable attacks.
- Execution of all processing ransomware applications are infected to create efficient execution policy is where the destructive methodologies are explored with WannaCry or wanna cryptographic algorithms.
The destructive scale of ransom
The windows supportive terminal systems are associated with Microsoft deliverables where additional laws of operating systems are incorporated to fight against WannaCry ransomware attacks. The technical perspective of WannaCry encrypted technologies is used in ransomware attacks and support for multiple descriptive scale algorithms. [4]
Ransomware payment
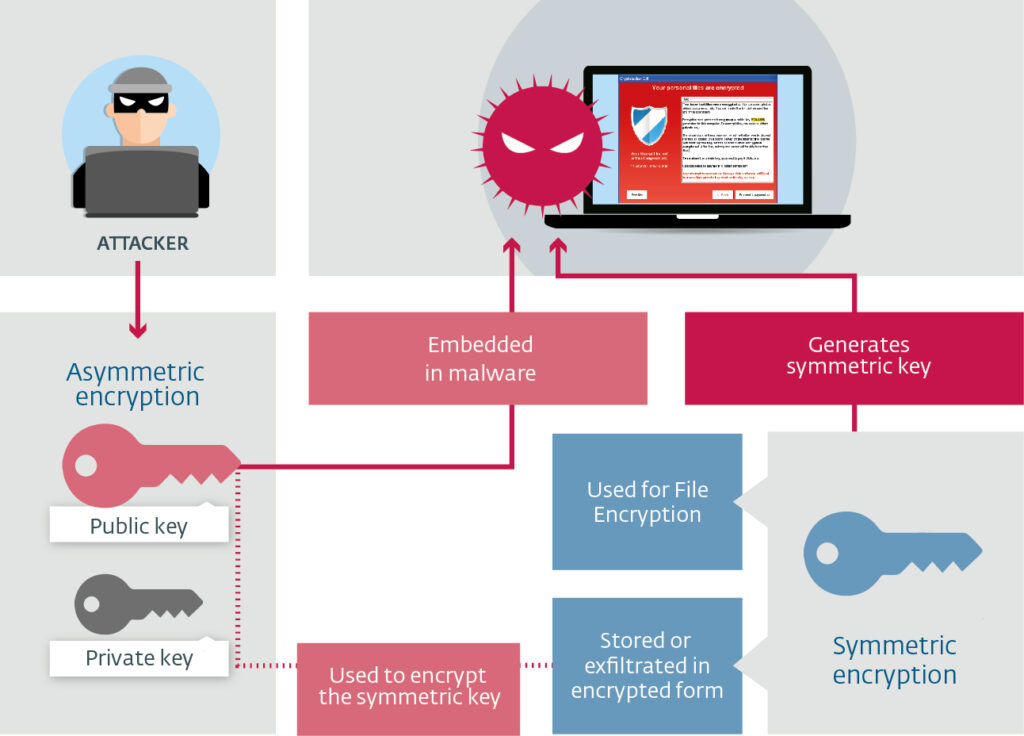
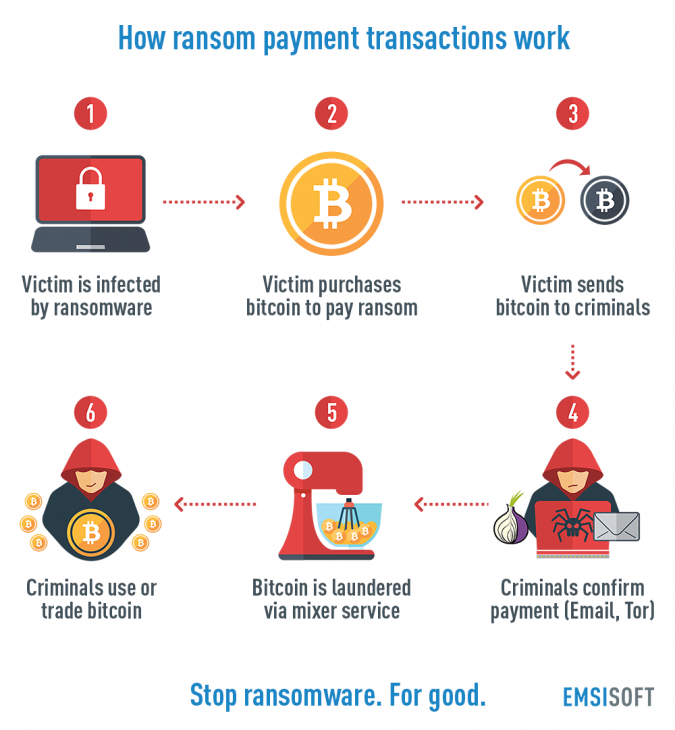
File encrypted technologies and ransomware software systems are presented in graphical user interface systems where the encryption of all the payments and recovery of files is associated after the payment with a decryption key. The ransomware payment is adopted with a bitcoin management system where all the encryption and decryption policies are associated with a unique key.
Ransomware threat
The ransomware threads are not adapted to the particular specific industries but these are interconnected with all the fields of banking sectors and the healthcare industries where the high-profile healthcare incidences are associated according to the report which is generated by landscape per report application where the threads are identified.
The statistical analysis of ransomware techniques is associated to describe all the technical perspectives of design structures.
Future of ransomware
Internet of things is incorporated with various categories of network devices applications where the cloud computing deployment applications and consequent IoT devices are interconnected with threats and responses of data. A botnet is one of the remote controlling applications where all the malicious software is infected according to with size and shape of hidden tools that are used in an executable measurement system. Master boot record systems are required to analyze all the operating system capabilities where it reboots with the lock screen and designer malware applications which could provide payment and decryption of files according to restore ration of access probability.
Ransomware division.
1. Cryotome
Standalone ransomware is associated to create a replication of devices according to computer management systems, it reaches the maximum point and creates an impact of cryptocurrency.
2. Ransomware as a service
The ransomware will be sold the dark web application into a distributive kit of algorithms where the amount and packages are available according to the technical skills of the attacker system. The technical perspective of malicious applications is associated with email spam and explores the download which is driven by automatically activated devices.
Social engineering attack
The social engineering attacks are incorporated with ransomware attacks where the successful implementation of like leaves is associated according to the attacker information systems. Email spoofing and receipts of unauthorized clicks may create a sophisticated application where all the malicious attachments and threats are associated with network capabilities. Ransomware will define the organization where all the attackers will access different perspectives of ransomware information’s with traditional security products like antivirus and signature software are deployed to create protection regarding all the application processing system.
Click here for any IT support services

Prevention
- Prevention technologies of ransomware are associated to minimize the damage.
- Sources of successful ransomware implementation are associated with a critical component management system.

