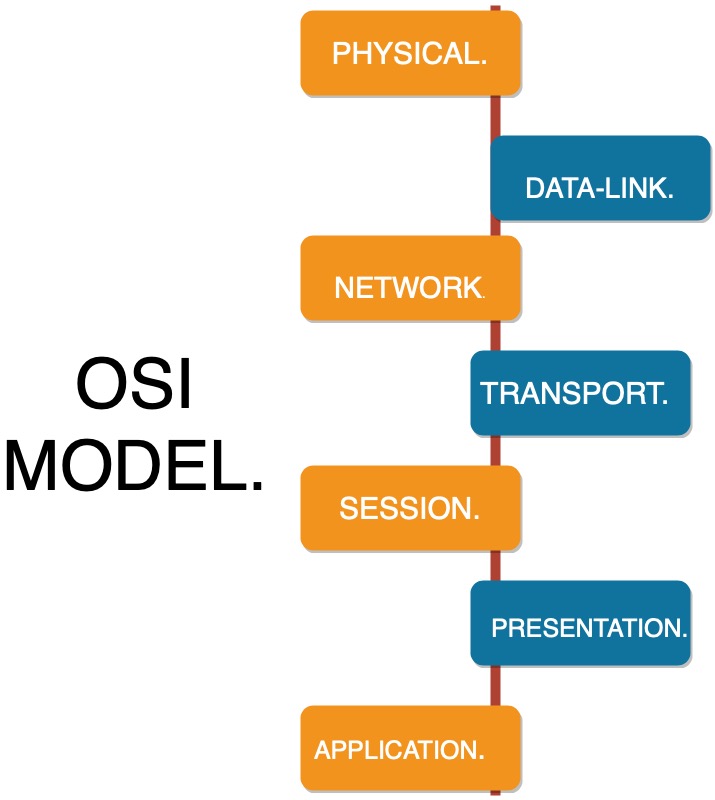
The OSI model stands for Open Systems Interconnection. It breaks the different parts of a computer network into seven layers.
It is significant that you comprehend what this model is and what network protocols run on each layer. These layers are utilized to troubleshoot network issues and to comprehend networking by and large. Each higher layer depends on services given by a lower layer.
WHY DOES THE OSI MODEL MATTER?
Although the advanced Internet doesn’t stringently follow the OSI model (it all the more intently follows the less difficult Internet protocol suite), the OSI model is still valuable for investigating network issues. Regardless of whether it’s one individual who can’t get their PC on the Internet, or a site being down for a large number of clients, the OSI model can assist with separating the issue and segregate the wellspring of the difficulty. On the off chance that the issue can be limited to one explicit layer of the model, a lot of unnecessary work can be kept away from.
The First Three layers:
They manage the mechanics of how data is sent starting with one PC to another over the network. They are known as the lower layers.
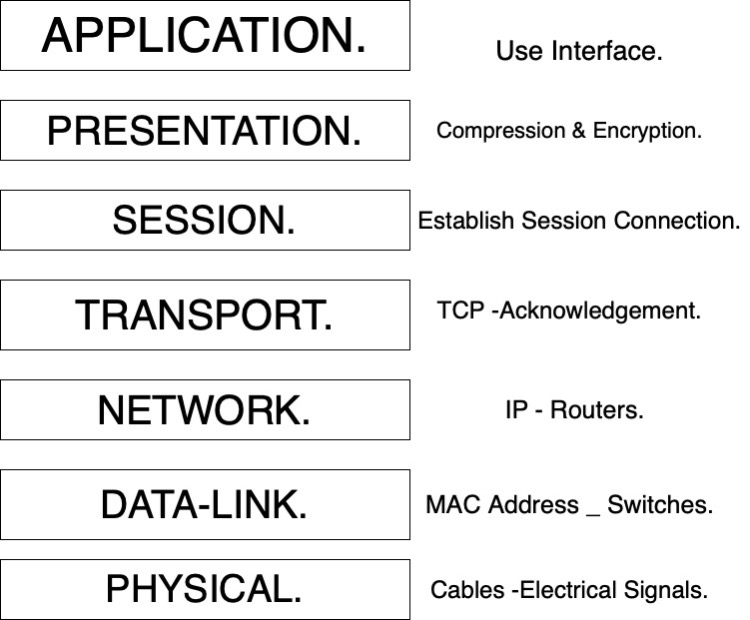
- Layer 1: Physical Layer
This layer tends to the actual properties of the network to establish a connection. The Physical Layer manages bits, which are binary values of 0 and 1. It characterizes:
. the cable utilized
. the voltages on the cable
. the timing of the electrical signs
. the distance that the cable can be run
A few instances of physical layer segments would be a repeater and a hub. A hub is a multiport repeater since it is utilized to recover signals when you need to surpass the cable length. Since these gadgets don’t inspect the contents of the signs that they recover, they work at the Physical Layer and not the Data Link Layer.
2. Layer 2: Data Link Layer
The Data Link Layer allots importance to the bits conveyed by the physical layer. The data components in the data-link layer are called frames. It tends to every packet so that it’s conveyed to the expected recipient. This layer likewise gives fundamental error detection and adjustment to guarantee the information sent is equivalent to it was received.
This data-link layer is partitioned into two sublayers, they are known as the logical link control (LLC) and media access control (MAC). Every gadget on the network has a MAC address. This is the equipment address that was doled out to the gadget at the manufacturer. It resembles a social security number.
The most well-known gadget that runs at the Data Link Layer is a switch. A switch looks at the MAC address of each approaching packet to figure out which port to send the bundle to.
3. Layer 3: Network Layer
The network layer characterizes how information packets get starting with one point then onto the next on a network and what goes into every bundle. The network layer utilizes conventions like Internet Protocol (IP) and Internet Protocol Exchange (IPX). These packets have steering data about the source and destination.
Routers work at this layer since they look at every bundle that goes through them. In the network layer intelligent addresses are meant MAC addresses. Since an information packet will go from the network layer down to the data-link layer, there must be an interpretation from IP (logical addressing to) to the MAC address of an network device.
The Next Four Layers.
4. Transport layer: The transport layer is the place where a PC interacts with another PC. In this layer the networking protocol of TCP is found. The primary reason for this layer is to guarantee that packets move over the network without errors. The transport layer does this by recognizing that a packet was gotten and re-sends the bundle in the event that it is corrupt, or it didn’t show up.
A packet is sent in pieces and when it is gotten, the transport layer reassembles the bundle and ensures all information was gotten effectively and not distorted.
5.Layer 5: Session Layer
The session layer sets up virtual sessions between network devices. A session should be set up before information can be sent over the network. This remembers arrangement between the customer and host for stream control, transaction processing, transfer of client data and validation to the network.
6. Layer 6: Presentation Layer
The presentation layer manages data compression and decompression alongside encryption and decoding. It is liable for changing over the information sent over the network starting with one sort of representation then onto the next.
7. Layer 7: Application Layer
This layer controls how the working framework and its applications communicate with the network. This application doesn’t mean Word or Excel. It manages the level at which application programs communicate with the network. Regular utilized application layer protocols incorporate HTTP and TCP/IP protocols.
Attempt to comprehend these various layers of the OSI model and you will comprehend PC networking.
HOW DATA FLOWS THROUGH THE OSI MODEL.
All together for human-readable data to be moved over an network starting with one gadget then onto the next, the information should go down the seven layers of the OSI model on the sending gadget and afterward travel up the seven layers on the less than desirable end.
For instance: Mr. Harry needs to send Ms. Julie an email. Mr. Harry makes his message in an email application on his PC and afterward hits ‘send’. His email application will disregard his email message to the application layer, which will pick a protocol (SMTP) and give the information to the presentation layer. The presentation layer will at that point compress the information and afterward it will hit the session layer, which will instate the communication session.
The information will at that point hit the sender’s transportation layer where it will be segmented, at that point those portions will be separated into packets at the network layer, which will be separated much further into outlines at the data-link layer. The data-link layer will at that point convey those frames to the physical layer, which will change over the information into a bitstream of 1s and 0s and send it through a physical medium, like a link.When Ms. Julie’s PC gets the bit stream through a physical medium (like her WIFI), the information will move through similar arrangement of layers on her gadget, however in the contrary request. First the physical layer will change over the bitstream from 1s and 0s into outlines that get passed to the data-link layer. The data-link layer will at that point reassemble the frames into parcels for the network layer. The network layer will at that point make fragments out of the packets for the transport layer, which will reassemble the portions into one piece of information.