The three steps of the network planning technique are network realization, network synthesis, and topological design.
When constructing a network, it’s also crucial to consider security, network applications, availability, traffic requirements, and accessibility.
• Determining the network’s logical and physical design
The physical and logical design of the network are used to create network architecture.
Physical design is the organization of network applications/devices such as hubs, PCs, routers, and switches.
Logical design is a description of conceptual network design (data flows, IP structures). The way of communication that connects two computers connected to a network is known as the logical layout of a network. The outflow of data between two systems is referred to as logical layout. In reality, network connectivity is determined by the network’s logical design. The logical design is used to install the physical layout design. The logical network can be upgraded as well, and it can be used to connect two or more machines. The virtual design of a network is logical, but the physical design of a network describes the network’s hardware functionalities.
Physical designs are communications between two computers connected by cables, whereas logical designs regulate the flow of data or communication between two networks. A network’s physical design, for example, can be modified to connect two or three office buildings. The growth would necessitate a network upgrade based on logical architectural structure. This would make it simple to process data from multiple systems in a building at the same time. The primary goal of a physical network is to offer information on the various physical components that make up a network. A physical network diagram can also be used to help troubleshoot by visualizing how each component in the network functions. When something in the network isn’t working properly, a clear picture of the pieces working together will reveal what needs to be fixed. A physical diagram is a diagram that shows how network devices and other physical components are connected. It shows the structure of the network as well as the presence of physical connections between devices. A physical diagram is primarily used by IT professionals to visually describe the physical connections. They’re used to diagnose network issues, spot security threats and weak places, and plan network changes.
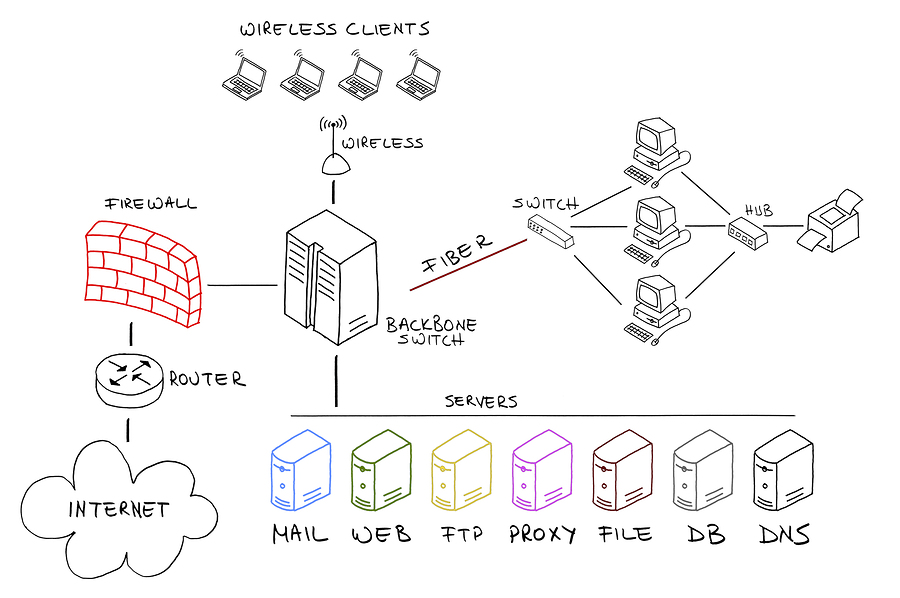
• Putting the network in place for design verification
In the execution of a network design, there are several stages. Design references, thorough planning documents, implementation instructions, roll-back guidelines, and time projections are just a few of the phases. The goal of the design process is to turn agreed-upon client requirements into a specification that defines and enables the implementation of the service to be offered in a systematic and controlled manner. The design process must be clearly documented, according to ISO 9001. Mechanisms must be included in the procedures to control and verify the design work to ensure that the given requirements are met. Documenting the organization’s structure, responsibility, and authority will be part of this. Prepare a design plan for the design activities and keep it up to date as the design progresses. Responsibilities and resources for each design activity must be identified, as well as the timing of tasks, checkpoints to monitor progress, and the scheduling of reviews and verification. We must think of design as a continuous commitment over the life of a contract, with continuing change management effort and periodic review. Ensure that the job is assigned to professionals with adequate resources and knowledge. Keep track of organisational and technological interfaces with other teams involved in the design process.

• During the performance phase, the network must be operational.
Network operation provides detailed explanations of network visibility methods, network system monitoring, and application performance. To improve network performance, operational tasks such as firewall administration, backup storage, software installation, patch management, and performance reporting are used. The more precise the implementation plan documentation is, the more probable it is that the project will succeed. Although the designer is normally required to complete sophisticated implementation stages, other staff members can complete well-documented thorough implementation processes without the designer’s involvement. Most large business design engineers rarely execute the hands-on stages of deploying the new design in practice. Rather, network operations or implementation engineers are frequently the ones who deploy a new architecture based on a strategy. Furthermore, even after a successful pilot or prototype network test, you must consider the probability of failure while executing a design. At each phase, you’ll need a well-defined but basic process test, as well as a strategy for reverting to the initial setup if something goes wrong.

• Troubleshooting network issues and redesigning in the event of a failure
The phases of network status improvements, connections, and network processes are the primary pillars of network optimization. Network logs will show bandwidth utilization, latency, and availability in great detail.
Popular methods of optimization include service quality and traffic engineering.
To deliver the best service to your customers, you must first figure out what the problem is.
Collect enough information from those who are experiencing network issues, as well as the network itself, to be able to duplicate or diagnose the issue. Avoid conflating symptoms with the root cause, as what appears to be a problem could actually be a symptom of a larger issue.
Customize your logs.
Ensure that your event and security logs are configured to give you with the information you require to troubleshoot. Each log should include a detailed description of the items or events being recorded, the date and time, and information about the report’s source (MAC or IP address).
Examine access and security.
Check that no access or security issues have developed by confirming that all access permissions are set correctly and that no one has interfered with a sensitive area of the network that they shouldn’t have access to. Check that your firewalls, antivirus, and malware software are all up to date, and that no security issues are interfering with your users’ ability to function.
Follow an escalation plan.
Going to the IT help desk and being directed to someone else, who then directs you to someone else, who refers you to someone else, and so on, is incredibly aggravating.Establish a clear escalation structure that indicates who is liable for various issues and who may be contacted for help at the end of the chain. If your end consumers have a problem, they should know who to contact so they don’t waste time talking to five different people who can’t help them.
Use monitoring software to keep track of your progress.
Manual troubleshooting is possible, but if you go through each step, it can take a long time. When you have a flurry of people beating on your office door or sending you frantic emails, it can be frustrating to try to figure out what’s wrong, let alone fix it. In commercial and corporate situations, it’s best to use monitoring tools to verify that you’re getting all of the important network data and aren’t missing anything important, not to mention avoiding exposing the company to unnecessary risk.


