Introduction:
In our digital age, where privacy is paramount, Virtual Private Networks (VPNs) have become indispensable tools. This blog offers a comprehensive introduction to VPNs on Windows and macOS, shedding light on their functionalities, benefits, and how they enhance online privacy without compromising readability.

Decoding VPNs: A Quick Overview
What is a VPN?
A VPN, or Virtual Private Network, is a technology that establishes a secure, encrypted connection over the internet. This creates a virtual tunnel for data transmission between the user’s device and a server, ensuring privacy and protection against potential threats.
How do VPNs Work?
VPNs operate by rerouting internet traffic through a secure server, masking the user’s IP address and encrypting data. This process not only shields users from cyber threats but also enables them to access the internet anonymously from a different geographic location.
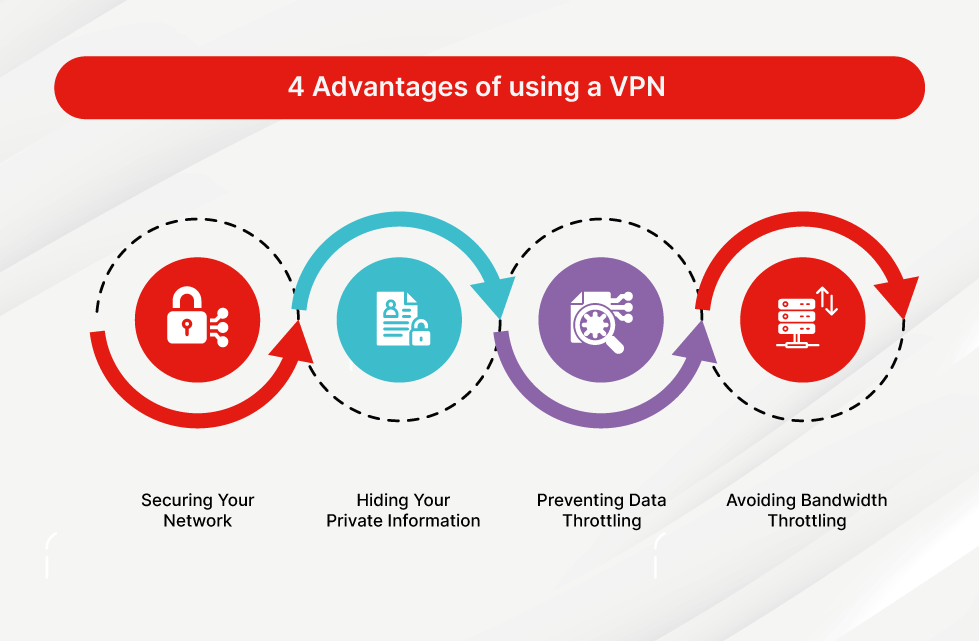
Benefits of Using VPNs
1. Enhanced Security:
Learn how VPNs bolster online security by encrypting data, protecting against hackers, phishing attempts, and identity theft.
2. Privacy Preservation:
Explore how VPNs safeguard user privacy by anonymizing online activities, preventing monitoring by ISPs, government agencies, or malicious entities.
3. Geo-restriction Bypass:
Discover how VPNs help users overcome geo-restrictions, accessing region-locked content, streaming services, or websites from anywhere in the world.
4. Secure Remote Access:
Understand the importance of VPNs in providing secure remote access to corporate networks, allowing employees to work remotely without compromising data security.
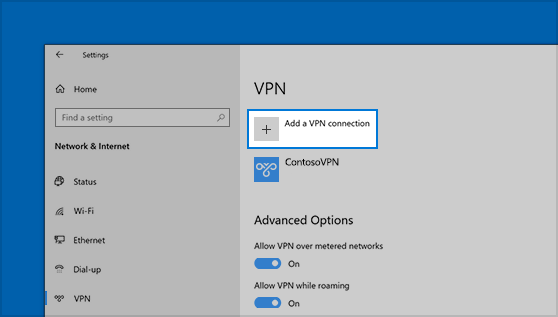
Setting Up a VPN on Windows
1. Built-in VPN Support:
Explore the native VPN features integrated into Windows, providing users with a simple method to set up and configure VPN connections.
2. Third-party VPN Applications:
Discover popular third-party VPN applications compatible with Windows, offering additional features and customization options for users seeking more control over their VPN experience.
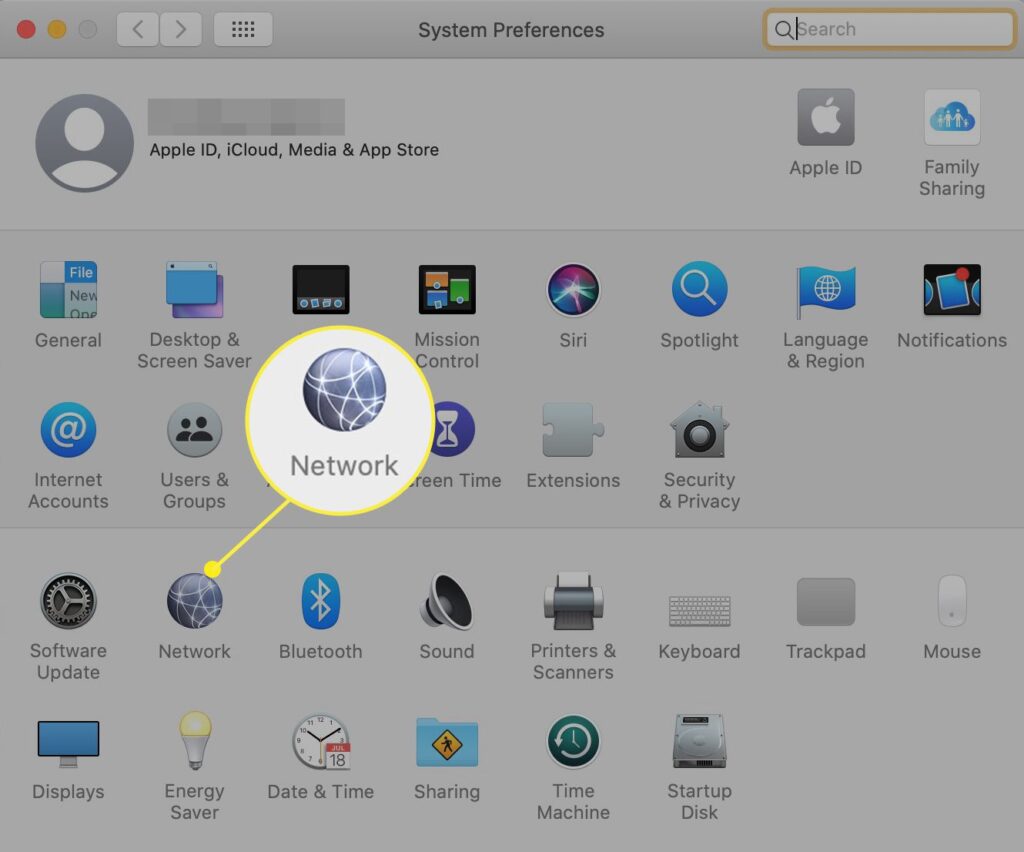
Setting Up a VPN on macOS
1. Integrated VPN Settings:
Understand how macOS provides integrated VPN settings, allowing users to configure VPN connections seamlessly within the system preferences.
2. Top VPN Apps for macOS:
Explore recommended VPN applications for macOS users, highlighting their unique features and benefits for a personalized VPN experience.

Best Practices for Using VPNs on Windows and macOS
1. Choosing the Right VPN Service:
Guidance on selecting a reliable VPN service, considering factors such as encryption protocols, server locations, and privacy policies.
2. Ensuring Proper Configuration:
Tips on configuring VPN settings for optimal security and performance, covering aspects like protocol selection, kill switches, and DNS leak protection.
3. Regularly Updating VPN Software:
Emphasizing the importance of keeping VPN software up to date to address potential security vulnerabilities and ensure optimal functionality.
Conclusion
In conclusion, this blog provides a comprehensive yet accessible introduction to VPNs on Windows and macOS. From grasping fundamental concepts to practical tips for setting up and using VPNs, readers are equipped with the knowledge to navigate the online world securely and privately.
By adopting VPNs as essential tools in their digital toolkit, users can reclaim control over their online privacy and security, ensuring a safer and more liberated online experience.
