Introduction
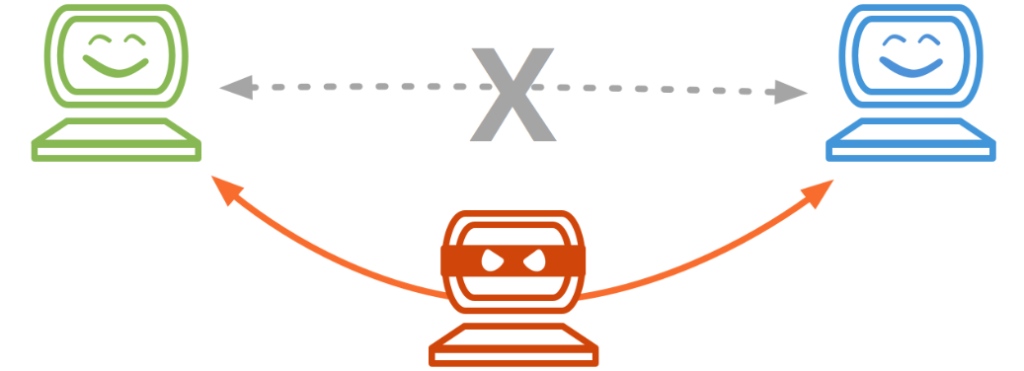
A man in the middle attack is a type of cyber-attack where the attacker inserts themselves into a communication between two parties in order to eavesdrop or tamper with the data being exchanged. This type of attack can be difficult to detect, as the attacker can masquerade as one of the legitimate parties involved in the communication. Man in the middle attacks can be used to steal sensitive data, such as login credentials or financial information, or to inject malicious code into a transaction in order to conduct other types of attacks.
How does this attack take place and its effects?
A MITM attack can be launched using a variety of methods. An attacker may take over a public Wi-Fi network or establish a free, unsecured Wi-Fi connection. When a user connects to the faked network by accident, attackers can intercept browsing behavior and send victims to malicious websites – even if the sites are legitimate – where they can steal log-in credentials, bank information, and other sensitive information. Identity theft, account takeover, reconnaissance, VIP impersonation, and unlawful money transfers are all possible with this information. In a man in the middle attack, the attacker intercepts communication between two parties. The attacker can then modify or redirect the communication without the two parties knowing. This type of attack is usually conducted by placing themselves between the two victims, such as on a public Wi-Fi network.
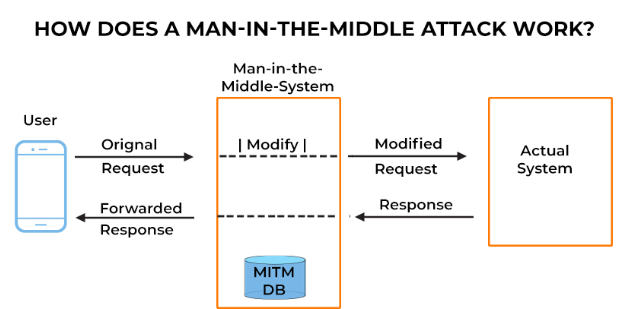
Corporate assets are at danger from the main-in-the-middle risk. MITM attacks have far-reaching consequences for the corporate network. When an executive connects to business resources from a work or personal device, or from their home network, as they frequently do, the attacker can eavesdrop on those connections, intercept secret information, and potentially get access to company networks. MITM attacks are difficult to detect and prevent, making them a CISO’s worst nightmare. The SOC has no control over what an executive does with their personal device or which Wi-Fi networks they connect to. VPNs can help but would need to implement strict security requirements to prevent sophisticated MITM hacks. Meanwhile, tips and tricks typically focus on educating users on what to look
Examples of Man in the middle attack
A man in the middle attack is a type of cyberattack where the attacker inserts himself into a communication between two parties. The attacker can then intercept, eavesdrop on, or even modify the communication. Some common examples of man in the middle attacks include:
-E-mail spoofing: Attacker modifies the headers of an email so that it appears to come from a different sender. The victim then unwittingly responds to the attacker, thinking they are communicating with the original sender.
-IP address spoofing: Attacker sends packets with a forged IP address, making it appear as if they are coming from a trusted source. The victim then responds to the attacker, thinking they are communicating with a trusted source.
-DNS poisoning: Attacker modifies DNS records so that when the victim tries to visit a website, they are redirected to a malicious site controlled by the attacker
Alternative Techniques for Intercepting Connections cybercriminals may employ a variety of additional techniques to stand between the client and the server. These techniques typically fall into one of three categories:
Server compromise: An attacker could use another method to take control of the server to which you are connected. Then, they can install their own software on that server to eavesdrop on your connections. They might start with SQL Injection and work their way up to full system compromise before installing MITM malware on the hacked web server. They might also take advantage of a code injection flaw to install a shell on the server.
Client compromise: An attacker may install a trojan or other malicious software on your computer (for example, man-in-the-browser). The application has the ability to listen in on all of your connections and is vulnerable to MITM attacks. To accomplish this, the attacker may trick you into clicking a dangerous link or employ another method to trick you into downloading malware. For instance, they might use malicious JavaScript and conduct a Cross-site Scripting assault on your preferred web application.
Compromise of communications: A hacker could gain control of a device that sends data between the client and the server. For instance, a public Wi-Fi hotspot or a network router with weak software. Additionally, rogue Wi-Fi access points may be set up nearby by cybercriminals for the purpose of attracting your connection. You can be the target of Wi-Fi eavesdropping if your Wi-Fi network connection uses a weak encryption protocol, such as WEP.
Some of the real-life examples of Man in the middle attacks are
The Babington Plot was one of the earliest cases. Thomas Phelippes, a cryptography expert, intercepted, decrypted, and altered communications between Mary Stuart and her fellow conspirators. Aspidistra devices were used by British intelligence to launch MITM assaults against Nazi forces during World War II. A MITM attack might also be thought of as cracking the Enigma code. The following are some of the most well-known instances of MITM attacks in the world of computing: Information on the Quantum/FoxAcid MITM system used by the NSA to intercept TOR connections was leaked in 2013.On its Windows PCs in 2014, Lenovo loaded the MITM (SSL Hijacking) adware program known as Super fish. A British couple (the Lupton’s) lost £340,000 in 2015 as a result of an MITM email eavesdropping/hijacking assault.
How can you prevent these attacks?
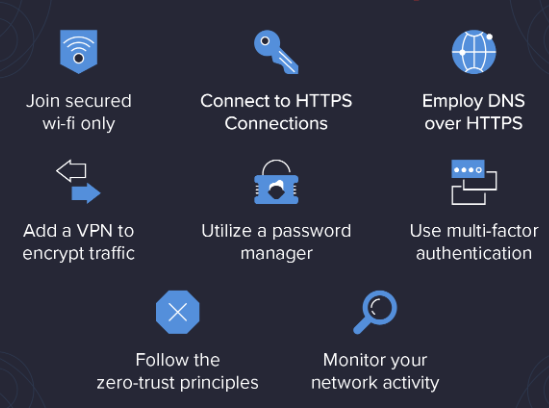
Man in the middle attacks can be prevented in a number of ways. One is to use encryption, such as Transport Layer Security (TLS), to make it more difficult for attackers to intercept and read communications. Another is to use strong authentication methods, such as public-key cryptography, to ensure that only authorized users can access data. Finally, you can keep your software up to date with the latest security patches to make it more difficult for attackers to exploit vulnerabilities.
Conclusion
A man in the middle attack is a type of cyberattack where the attacker intercepts communications between two parties in order to secretly collect data or inject malware. This type of attack can be difficult to detect, but there are some steps you can take to protect yourself, such as using a VPN and being aware of suspicious activity. If you think you may have been the victim of a man in the middle attack, it is important to change your passwords and run malware scans on your devices to ensure your safety.
