Abstract
Man, in the middle attack is a serious problem acquire in network interconnection. Man, in the middle is interlinked with cyber-attacks it is a malicious application enter in between the conversation of corresponding to users. It steals the sensitive information of the individual and analyzes the application according to the access inside the system processing structure. This attack will acquire the secret information where the manipulation of entire processing structures can be accessed, the main issue acquired with cryptographic algorithms where all the authentication of sensitive information and threatened applications are associated under in the middle attacks. The cryptographic network algorithms are accessed with efficient security systems and all the steals methods of hacking systems are steals acquired through man in the middle and this is the most dangerous application in network communication.
Introduction
The cryptographic network systems are associated with various useful communication system but the man in the middle is a malicious attack enter into the communication process in systems and transfer all the sensitive information which are associated between two parties. Acquiring for stealing of information can be accessed through true individual information technologies where the financial applications and targeted designs are acquired with third parties.
- Man, in the middle targets the end-users concerning financial applications.
- A secret PIN will be accessed with third party users.
- SaaS, business, and web applications are also acquired with men in the medals and create a dangerous problem.
- The computation for the hacking of information will steal all the sensitive data protocols.
- The application will include fraud management and an improved support exchange system.
The man in the middle applications is associated with the edge infiltration phase, the amount of advanced persistent threats is associated according to the schematic application of man in the middle, and all the malicious actors are involved in sending or receiving of data without the intimation of authorized users.
Attacks with Man in the middle
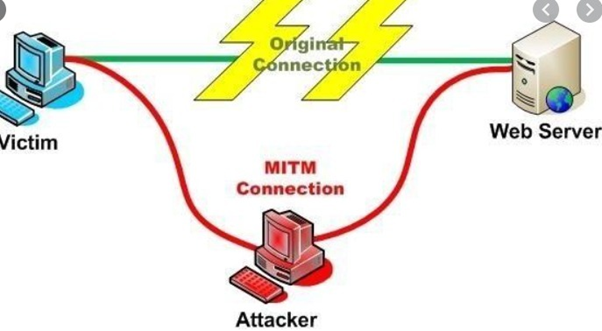
The man in the middle attacks are required with dynamic eavesdropping and create an independent victim to transfer messages. The network communication or message transfers are associated with two people where the independent victim transfer is acquired through message or independent victim telephonic. The man in the middle will steal the private information in the whole discussion with the user and the attacker will analyze the capacity of significant messages and passed out a inject into the database system. The attackers will have a capacity to analyze the message transition between two actors and inject new errors, analyzing all these factors we can gather the information and create a scope of an encrypted wireless access points man in the middle attacks will process to steal information
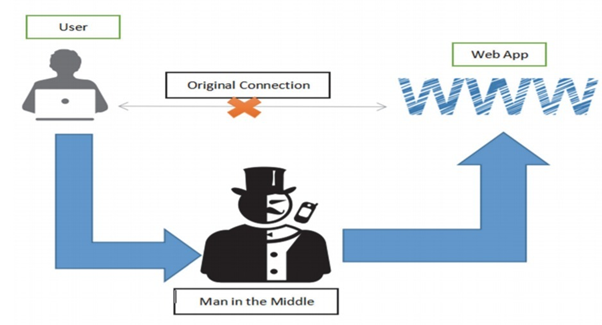
Solution
- It is necessary to provide efficient indication technologies that could improve the standardized data system.
- MITM, attacks will improve the risk associated with network applications, by using efficient encrypted technologies we can reduce the risk factor.
- The cryptographic method is encrypted to improve authentication processing.
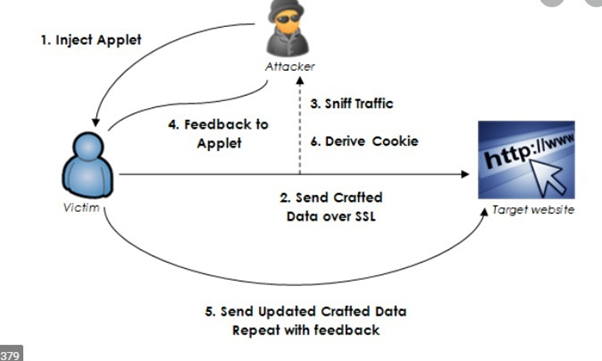
Man, in the middle attack to HTTPS protocol.
A web-based application protocol that is used with https applications where granted privacy and security transactions are associated with home banking and e-commerce, web application. The transaction ranging from recruitment technologies is used to analyze the sensitive information, the https protocol will prevent the unauthorized access because all the net banking information and confidential web devices should allow only the authorized users into the processing system.
Netscape communications are deployed with secure socket layer systems and all the senses to sensitive information are associated with the communication data system. The internet task force attacks are adopted to improve the standardization and security of transport layer security where https is used in the URL where the authorized users could access the web application. TLS encryption technologies are adopted with encryption standards where the authentication layer acts as a mediator between HTTP and TCP, where the security of transfer protocols are deployed and it will reduce the risks associated with network management and improve the standardized authentication system
Attack concepts
Man, in the middle attacks are deployed in https server management where certification of public encryption keys and the web browsers are associated with communication technologies. The path of vulnerable attacks and authenticating service will give modified certifications were a successful adaptation of attacks will neglect the errors and produce a warning notification which will improve the frequency counter.
- The client host is one of the applications used in user protocol where it wants to create a secured transition.
- Server host network transitions are deployed to have a security transition.
- An attack host is one of the applications where the exchange of information is hosted with efficient deployment.
Attackers built an attack.
- Gateway techniques are associated between client host and local area network routing.
- Client hosting will request for interconnection to server hosting with the default gateway routers.
- Intercept server hosting will forward the local area network as the default browsing system.
- Client hosting will accept all certification and create efficient encrypted standards.
Sniffing
- It is the easiest attack to launch in all the packets of transition between the attackers.
- Plaintext protocol will sniff the user id and password with the implementation of HTTP, FTP.
- Standardized data systems are associated to create an application with an efficient deployment system.
Progression of man in the middle attack
Efficient man in the middle attack execution is associated with two different stages.
- Interception.
- Decryption
- All these techniques are involved with efficient intended target management systems where all the malware is involved with a man in the middle browser attacks.
- The technical perspective of execution is involved in various Malware applications were sending or receiving of unsecured data systems are authorized with the Wi-Fi switch configuration system.
- Network cryptographic algorithms and attackers which are deployed in data systems are injected with malware into the PC such that all the sensitive information will be accessed with third-party victims.
- The transition of malware will gather all sources of information through which data transitions are acquired.
Interception
The initial step of intercept applications is associated with the attackers to describe the intended destination system.
1. IP spoofing
The application will involve all the attackers to create a is efficient application technologies with will alter the IP address in the system. The network communication and attempting client URL technologies are associated according to the applications which are sent and received with attacker end.
2. ARP spoofing
ARP spoofing technology will forward all the attackers with Mac address in systems and deployed with IP address where all the local area networks will use fake ARP to access the personal information. The information which is sent by the client is deployed with host IP deliverables and creates a transmission of the attacker’s management system.
3. DNS spoofing
The DNS spoofing, will store all the positions and be involved in filtration technologies for all the DNS server management will alert all the record sites where adjustments of record are used according to the encrypted technologies.
Description
1. HTTPS spoofing
The https provides a victim browser to initialize the demand for safe site management technologies.
2. SSL browsing
SSL browsing technologies help to create efficient token management systems which are involved in man in the middle attack systems.
- Authentication token with MIMAM
- Man, in the middle attack with rapid web service.
SSL hijacking
The attackers will have their identification technologies where it sends or receives the client application with efficient handshaking technologies. The says identification systems are organized with a man in the middle attack.

