The risk of network security attacks has gained a lot of momentum in the past decade. With the fast transition to remote working technology and using online resources to store sensitive data, detecting and preventing these security attacks have become the need of the hour.
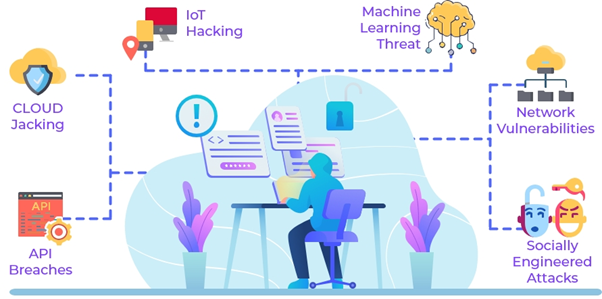
SOURCE: nsktglobal.com
Intrusion detection and prevention are kinds of broad words to describe practices used for application security. These practices not only help to mitigate network attacks but also to block new threats.
Types of Network Attacks
Network attacks are unauthorized actions that target computer networks or the infrastructure in an organization. These attacks orchestrated by malicious parties aim to alter, corrupt, or steal your organization’s data. Here are a few common types of network attacks conducted to steal your personal information.
1. Malware
Hackers attempt to gain access into your personal computer to corrupt your files or data, using malicious codes known as malware. It is one of the most dangerous cybercrimes, causing massive damage.
2. Phishing
Cyber Criminals trick users to click on fraudulent email links or messages. Malware downloads into your phone or computer as soon as you click on these legitimate-looking links. It allows them to steal sensitive information, like credit card details.
3. 5G Attacks
With the help of the 5G network’s high-speed data transfer, hackers are now able to attack multiple systems, mobile phones, or IoT devices. These swarm-based network security attacks can make changes in real-time.
4. DoS and DDoS Attacks
Cybercriminals use DoS and DDoS attacks to overload your website with malicious traffic. As a result of the attack, your website crashes and your users won’t be able to access it.
Techniques of Network Attacks
Unauthorized activity on your digital network often involves stealing valuable data and jeopardizing your network’s security. With tons of digital activity constantly happening around us, it might be challenging to pinpoint a network attack. Here are a few network attack techniques that organizations should look for.

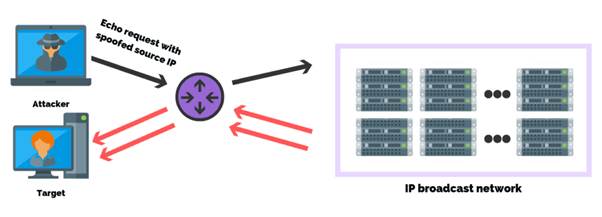
SOURCE: malwarebytes.com
1. Buffer Overwriting
Attackers overwrite certain sections of computer memory and replace them with malicious commands. These commands are later used to enter into the system and corrupt your data.
2. Trojan Horse
This malware creates a network backdoor, giving attackers easy access to your computer system and all the available data. They are introduced into the system through online archives.
3. Worms
These standalone computer viruses spread through email attachments and messages. These worms can be moderated to steal confidential information, including social security numbers or credit card details.
Prevention of Network attacks
Network security is one of the most critical aspects of an organization. Keeping your employee’s and customers’ data safe should be the priority for every company. To detect an attack, you need to know the types of network attacks. Once you know what hit your organization, you will prevent a similar attack in the future.
SOURCE: purplesec.us
Here are a few ways you can prevent network attacks in the future.
1. Antivirus Software
These programs scan every file that you download from the internet on your computer. It prevents damage to your system and protects your devices against viruses or malware.
2. Data Encryption
A security method that securely encodes your data, and only an authorized user can access your organization’s database. It protects your information from being stolen from phishing attacks.
3. SSL Certificates
SSL Certificates are a global standard security protocol that establishes a secure connection between your web server and the internet browser. It encrypts all your data that passes through the network.
4. Virtual Private Network
This software creates a secure and encrypted connection over public and private networks, like Wi-Fi hotspots. These are popular amongst big organizations and help them to keep their sensitive data safe.
Intrusion Prevention System
Intrusion Prevention System or IPS is a network security application that regularly monitors your system or network activities for any malicious action. If the software detects malicious activity, it collects all the required information and reports it to the security administrators.
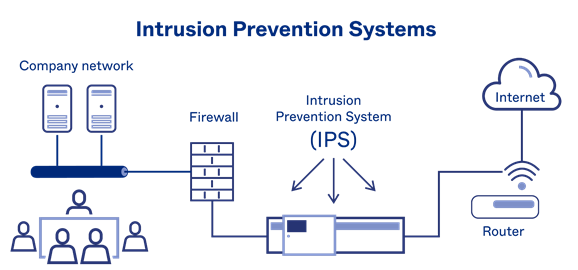
SOURCE: okta.com
Once the activity has been reported, the Intrusion Prevention System will work towards blocking it. It uses various techniques for stopping the attack, including changing the security environment or changing the attack’s content.
Intrusive Detection of Network Attacks
No matter how advanced the level of prevention techniques your organization might use, there is a good chance that your computers can still get affected by network attacks. Hence, detecting and resolving these attacks before they cause significant damage to your system is essential.
Most organizations implement multiple layers of defense strategy, which is much more complex and challenging to break. When the attack fails each layer, it will alarm the security administrator, and the virus can be detected easily.
Intrusion Detection System
An intrusion detection system, also known as IDS, is software that regularly monitors your system for any suspicious activity. The system issues instant alerts the second a malicious activity is discovered.
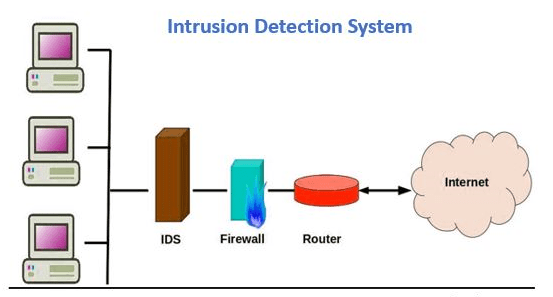
SOURCE: comodo.com
IDS detects suspicious activity by scanning the system for policy breaching. Once the issue has been detected, the system will automatically alert an administrator or a SIEM system.
Even though IDS applications are pretty effective in detecting malicious activities, they might sometimes generate false alarms. Hence, you would need to fine-tune your applications after you have installed them. You need to set them up and train them to understand what regular traffic looks like and how it is different from a malicious one.
Intrusion detection systems detect malware using two techniques. First is the Signature-based Technique, which uses specific patterns to detect the attack. It also uses previously known malicious instruction sequences used by the malware. These sequences are known as signatures.
The second technique is the Anomaly-based method which detects unknown malware attacks. It uses machine learning to create a trusted activity model. Whenever a new activity is detected, the software compares it with this trusted model. If it is not found in the model, then it is declared malicious.
Conclusion
Even though IDS and IPS are related, they are a little different in their way of working. The intrusion detection system is a passive monitoring application, where the packets are analyzed at the primary level, and the results are logged in. In contrast, an intrusion prevention system follows a more proactive approach.
There is no permanent method to prevent your personal or organizational system from a network attack. However, you can use proactive methods and techniques to detect the malware early and avoid a similar attack in the future. Efficient intrusive detection and prevention of network attacks are essential to protecting your client data and maintaining your organization’s reputation.
