This blog is the second part of the Internet Security for Home Users series. Throughout this series, you will learn tips and tricks to keep your home internet secured with the use of network troubleshooting, modem configuration, firewall setup, and VPN usage, among others. This blog will cover everything you need to know about a firewall and how to enable it on your devices.
What is a firewall?
The term “firewall” refers to a partition designed to prevent the spread of fire. Similarly, on your computer, a firewall helps prevent unauthorized access to your devices and secure the data on your computers. While it filters malicious traffic requests on a network, it allows legitimate traffic through.
What are the types of firewall architectures?
Packet-Filtering Firewalls
As the oldest kind of firewall architecture, packet-filtering firewalls create a checkpoint at a traffic router. The firewall checks on data packets coming through the router by checking – inspecting destination and origination IP address, parcel type, port number, and other data on the surface without reviewing its substance. It will drop any packet that does not pass the inspection.
The benefit of packet-filtering firewalls is that it does not require a lot of resources and will not have a huge impact on your system performance. However, it is relatively easy for harmful data packets to bypass the inspection as it only reviews information of the surface level.
Circuit-Level Gateways
Like packet-filtering firewalls, circuit-level gateways can quickly inspect traffic without requiring much computing resources because they do not check the packet itself. It verifies the transmission control protocol (TCP) handshake to ensure that the packet is from a legitimate source.
Since this type of firewall does not check the content of the data packets, it is possible for a packet with malware but with the right TCP handshake to pass through.
Stateful Inspection Firewalls
This type of firewall utilizes packet inspection technology and TCP handshake verification. The level of protection offered is greater than the two types of firewalls previously mentioned.
However, these firewalls do put more of a strain on computing resources as well. This may slow down the transfer of legitimate packets compared to the other solutions.
Proxy Firewalls
Proxy firewalls, or sometimes called Application-Level Gateways or Cloud Firewalls, filter incoming traffic between your network and the traffic source at the application layer. The delivery of this type of firewall is a cloud-based solution or another proxy device. It will establish a connection to the traffic source and inspect the incoming data package instead of allowing a direct connection to the traffic source.
Similar to the Stateful Inspection Firewalls, they inspect both the packet and the TCP handshake protocol. On top of that, proxy firewalls can perform deep-layer packet inspections and check and verify the contents of the packet to ensure that it contains no malware. It will only let the packet connect to the destination if the checking process approves the content of the packet. The proxy firewalls create an extra layer of protection between the origination source and the devices on your network. However, in exchange for better security, proxy firewalls can slow down your system due to all the extra steps required.
Next-Generation Firewalls
Among the many recently released firewalls are “next-generation” architectures. Some of their common features include deep-packet inspection, TCP handshake checks, and surface-level packet inspection. Next-generation firewalls may include other technologies such as intrusion prevention systems (IPSs) that automatically stop any attacks against your network. However, the term is not well-defined, so it is important to check what a next-generation firewall is capable of before investing in one.
What are the methods of delivering firewall functionality?
Generally, there are three methods of delivering the firewall functionality which is through hardware, the cloud, and software.
Hardware Firewalls
This kind of firewall requires a physical appliance that intercepts data packets and traffic requests before they are connected to the server of your home network. Hardware firewalls are especially good at securing the perimeter and prevent traffic with malware before the endpoints are put at risk. The drawback of this category of firewall functionality is that its capacity to handle simultaneous connections is limited so insider attacks can bypass them.
Cloud Firewalls
A cloud firewall, or firewall-as-a-service (FaaS), or proxy firewalls mentioned in the previous section. This is because many of the proxy firewalls are cloud-based. A major benefit of cloud-based firewalls is that they are scalable, meaning that their capacity can be increased to filter larger traffic loads. Similar to hardware firewalls, cloud firewalls excel at perimeter security. This option is more suitable for organizations and not home users. For more information, please do not hesitate to contact BITS.
Software Firewalls
This category covers any type of firewall applications installed on your devices that does not require any hardware or a cloud server to function. By isolating individual network endpoints from one another, it can help create a line of defense.
However, it is important to check the compatibility of the firewall and your device because it is not a one-size-fits-all type of situation. Also, maintaining individual software firewalls on different devices can be time-consuming. Below are simple ways to turn the firewalls on and off for both Windows and Mac. If you find it complicated, please feel free to contact a specialist here.
How to check whether your firewall is on?
Regardless of the operating systems, your devices do come with their firewalls. There is one main difference in firewall protection between Windows and Mac. Mac’s built-in firewalls are off by default because, unlike Windows systems, Macs are not prone to worms infection.
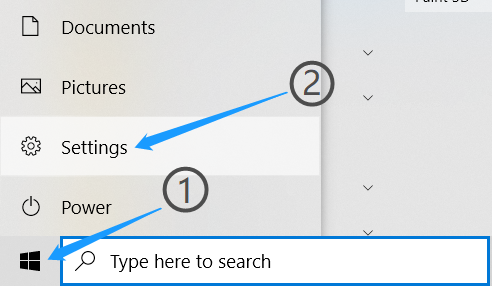
For Windows, you can check the status of your firewalls by following these steps:
- Start > Windows Start Screen > Settings
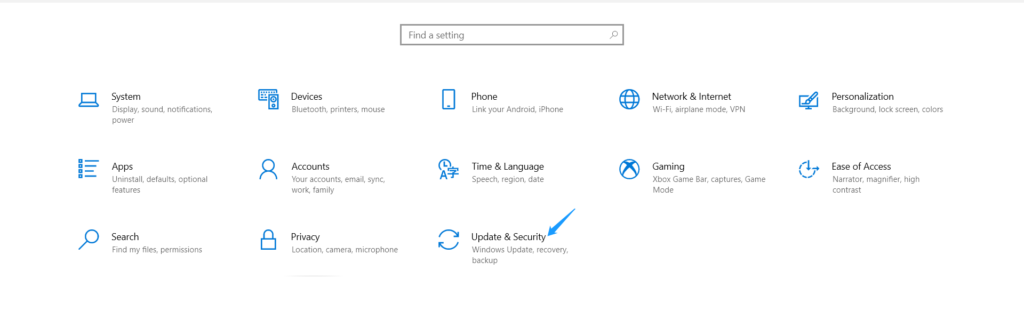
2. Click the Update & Security > Windows Security
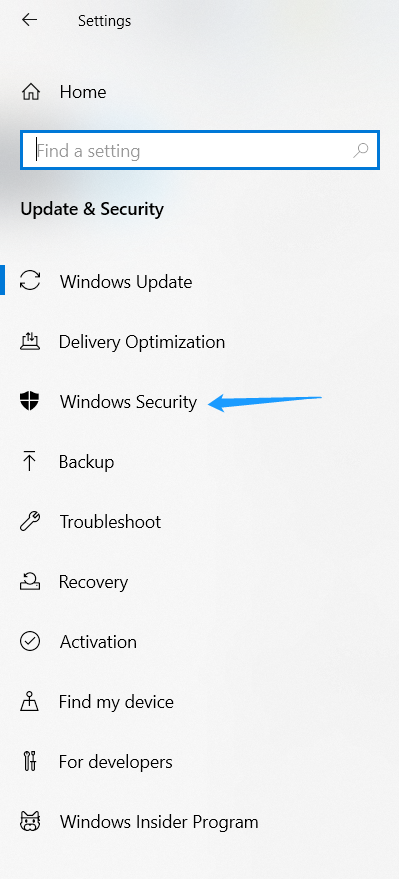
3. Click Firewall & network protection
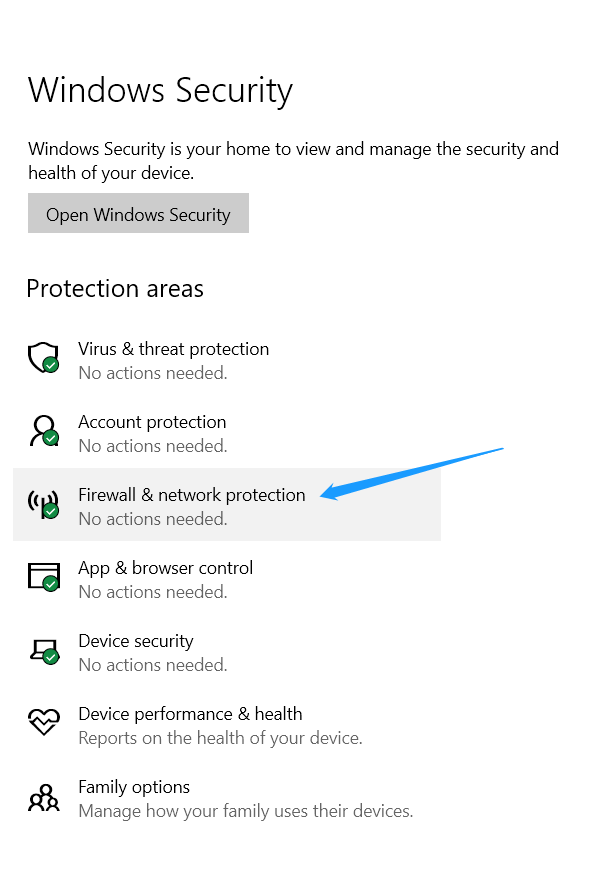
Upon completing the third step, you will see whether your firewall is on for domain, private, and public networks as well as the option to enable and disable.
For Mac, you can simply enable the firewall protection by following these simple steps:
Choose Apple menu > System Preferences
Click Security & Privacy > Firewall
Note: if there is a lock icon present at the bottom left, you have to first unlock the preference pane.
Click Turn On Firewall