The later center on security concerns is driven by various cyber security assaults that driven to enormous breaches of individual information. In reaction, controls outlined to fortify shopper security assurance have been created in nations around the world, from the U.S. to India to Australia. The EU’s GDPR (Common Information Assurance Direction) in specific has had an vital affect. In expansion, numerous person states within the U.S. have embraced their possess protection security laws, such as the CCPA (California Shopper Protection Act), and their number is still developing. We ought to expect more administrative exercises within the future, as Congress is working to actualize a U.S. government information security law. Exactly why is information security vital? It is vital to shoppers since a breach of individual data can harm an individual’s essential rights and flexibilities, counting the hazard of character burglary and other sorts of extortion. But information security concerns are moreover critical to organizations. If you somehow have also been a target of the hackers, you must approach a reliable cyber security expert like BITS.
Simple step to Protect Privacy

Use a Password Manager to Protect Yourself
The normal individual has 70-80 passwords to keep in mind. As a result, numerous of us conclusion up reusing the same ancient passwords or depending on passwords that are simple to keep in mind, but similarly simple to guess. A secret word supervisor gives you a secure put to store your passwords whereas observing them shortcoming and reiteration and making a difference you make unused, solid passwords. Numerous watchword directors are free, up to a point at least. Take Dashlane, for case, which lets free clients make and store up to 50 passwords, and spare installment subtle elements and distinguishing proof records. It encompasses a strong watchword generator and lets you utilize two-factor verification to boost security indeed further.
Use a VPN to Stay Safe on Public Networks
Open Wi-Fi systems are the virtual proportionate of the dodgy neighborhood, where cybercriminals, programmers, and other evil characters are sauntering on each corner. Employing a open Wi-Fi association uncovered you to a variety of cyber dangers, the foremost predominant being Man-in-the-Middle assaults, in which your information is catching some time recently it comes to the association point. An unsecured open Wi-Fi association may still redirect you to a malevolent site. Indeed in case you simply visit secure HTTPS locales, a few of the apps on your cell phone can be interfacing to HTTP destinations without you knowing it. If you’ve not introduced the most recent security patches for your working system, your gadget might come beneath attack.
One of the most excellent VPNs can keep these threats at narrows. We recommend:
ExpressVPN – the finest all-rounder with the quickest speeds
NordVPN – worldwide server arrange and top-class security
SurfShark VPN – reasonable plans with great speeds and cutting-edge encryption.
Use a Private Browsing Mode when Surfing the Web
Whereas a private browsing session doesn’t offer the same level of security as a VPN, it does cruel your browsing history won’t be spared and any treats created amid the session, deleted. Private browsing mode is “largely incapable at blocking third-party observing, meaning that your web benefit supplier can still track your online activities”. It’ll , be that as it may, halt anybody else utilizing that gadget from finding out where you’ve been or getting to touchy data, like your online keeping money password. It’s a step within the right heading but, in the event that you need to protect your security online more viably, you’ll attempt utilizing an mysterious browser like Tor, or let a VPN cover you in a cloak of secrecy.
Stop Adware by Using an Ad Blocker
Adware was sent to undertake us. It may be outlined to accumulate data so we as it were see pertinent adverts in our social media nourishes, but it’s gone way past the call of duty. Some adware is so determined, it’ll take after you through the internet, following your computerized impression and gathering up pieces of information about your area. Once it’s wrapped up, it’ll immerse you with adverts that hinder your browsing encounter, eat up your portable information, and eat absent at your device’s battery life. Standalone adblockers like AdBlock Furthermore and uBlock Root, are accessible as free browser expansions and a few antivirus program and VPN suppliers bundle advertisement blockers into their suite of cybersecurity tools Google Chrome presently has anti-ad blocking apps accessible simply can utilize in conjunction together with your ad-blocking computer program to fly under the radar – or so they say. The viability of these is, as however, dubious so choosing a trustworthy advertisement blocker is likely still perfect way”>the most perfect way of ensuring your security online
Update Your Privacy Settings on Social Media Account
You’ll have, incidentally, given all sorts of apps and websites authorization to connected with Facebook using your profile. You’ll be, able in the event that you have got a morning to save, utilize Facebook’s Off-Facebook Movement device to track them down and near them down but, I caution you, it’s not simple but it is worth it. It’s prudent to change a couple of settings to make strides your online security.
These include:
Not utilizing area information when posting
Preventing clients from labeling you in photos
Hiding your e-mail address and phone number
Turning off personalization and data
Not giving Twitter consent to get to your address book
Protect Your Phone’s Online Privacy
There are a few steps you can take to boost your phone’s online privacy. These include:
- Activating two-factor authentication
- Using a screen lock
- Turning off your location, Wi-Fi and Bluetooth whenever they’re not in use
- Only installing apps from reputable sources
- Not jailbreaking your iPhone
- Avoiding using USB chargers in airports and other public places
- Keeping your apps updated
- Managing your app permission
- Using one of the best antivirus apps for mobile devices
This can be done by experts like “Computer Repair Onsite” and “X-Techbuy.
Turn off your Location
Turning your area on your cellphone is reasonable in the event that you’re seeking out for a particular address or need to discover the closest coffee shop. Once you’ve found what you were seeking out, for be that as it may, you ought to turn your area off again. Leaving it open seem cruel giving obscure companies and peeping Toms more experiences into your life that you’d donate your best companion. Your area history seem give “evidence of sedate addiction” or uncover “records of visits to mental facilities”. Turn your area off or utilize a VPN to cover up it behind a fake IP address. That you’ll both secure your security online and opt-out of “the most noteworthy trap innovation companies ever played” – “persuading society to surveil itself”.
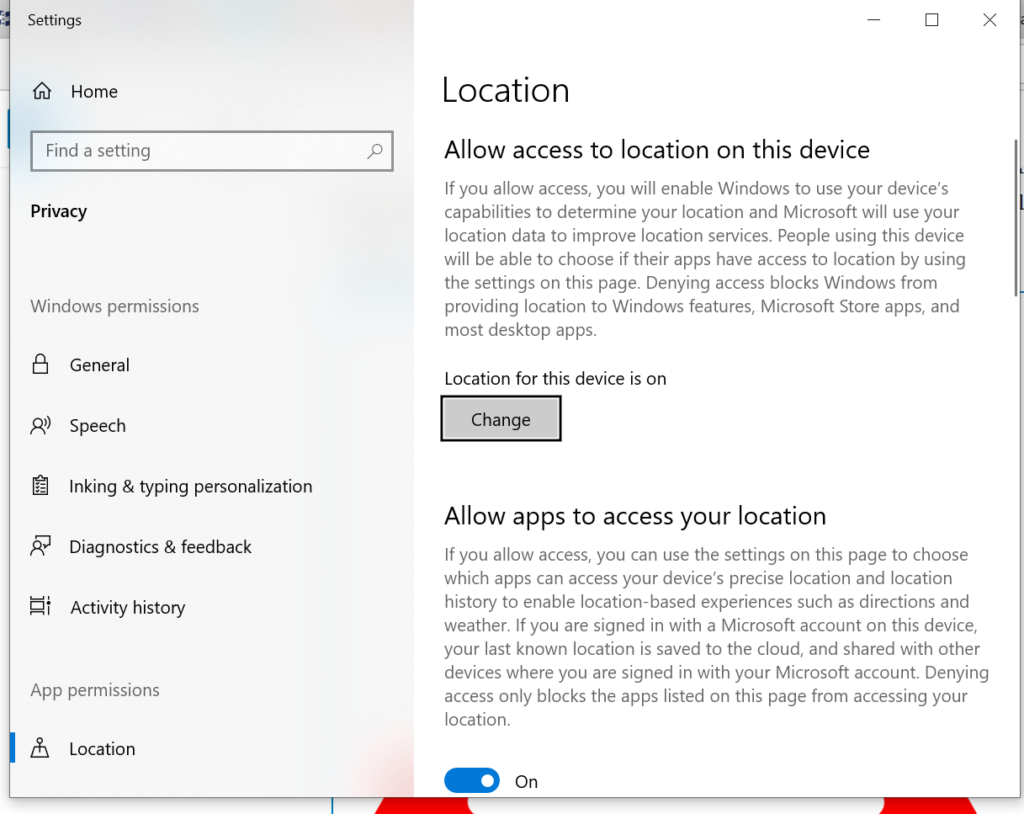
Limit your applications’ access to personal data and settings
Some apps are rather more cagey. The Washington Post ran an article last year pointing out that, on the average iPhone, apps are using trackers to collect and share around 1.5GB of data over 30 days.
Whereas you’ll be able halt them to a few degree by restricting their get to, a more compelling arrangement is to introduce a diverse sort of app through and through – one that will halt trackers rather than enacting them. Apps like Disconnect and Large will halt trackers… in their tracks! Disengage includes a free essential form accessible for macOS and iOS gadgets, whereas Enormous is consistent with both Andoird and iPhones but is as it were accessible on subscription.
Encrypt your Emails
Nearly all prevalent informing apps utilize encryption, and however few of us consider looking for out an scrambled mail benefit. Instep, we appear substance to bargain with the spam and the phishing assaults, depending on our minds and great sense to channel out the dangers. Depending on who your mail benefit supplier is, you ought to be able to scramble emails yourself. To realize this, in any case, both you and your beneficiary ought to empower S/MIME e-mail encryption settings, so it’s not practical in each instance. Alternatively, you’ll utilize a third-party encryption apparatus to do the work for you. For occasion, Mailvelope contains a browser expansion that’s consistent with Firefox, Chrome, and Safari. This will deliver you end-to-end encryption on Gmail, Viewpoint, and Yahoo Mail. It’s basic, open-source, and free.
Avoid clicking on links from unknown sources
if you don’t need to alter your e-mail benefit supplier or your e-mail address, you won’t need to switch to an scrambled mail benefit. Instep, you’re fair planning to have to be be more careful and remain on the look-out for e-mail tricks, phishing assaults, and other related threats. Phishing could be a destructive strain of social designing and phishing emails more often than not attempt to lure the beneficiary into clicking on a connect or opening an attachment. perfect way”>The most perfect way to halt them is by, very essentially, not clicking on or opening anything that’s not from a dependable source. There are a few other types of phishing to see out for which are less simple to spot. For illustration, stick phishing is after you get mail from a source posturing as an institution that’s known to be reliable (a wellbeing clinic, a bank, or indeed the government), provoking you to uncover individual data. Whaling is targetted at big-time CEOs and tall profile trade individuals, coaxing them to exchange stores or uncover top-secret commerce information.
Indeed in spite of the fact that these emails see true blue at to begin with look, you would like to guarantee that they are, in truth, who they say they are. You ought to never reveal personal data by means of e-mail unless you’re completely beyond any doubt who you’re sending it to. While a few antivirus bundles will watch against phishing assaults, the foremost solid way of ensuring your online protection in this occurrence, is by consistent watchfulness and awarenes
Manage your smart devices
IoT gadgets are taking the world by storm, making strides efficiencies in each feature of our individual and proficient lives. By 2021, there will be a anticipated 35 million shrewd homes within the US. Current gadgets have been appeared to be helpless to penetration by cyber-criminals, posturing a critical risk, to our individual security and indeed to worldwide systems. Usage of prescribed best hones can diminish the chances of an assault and offer an extra layer of assurance, in this manner expanding the security of IoT devices. The Web of Things, or IoT relates to gadgets which interface to the web or to each other, by means of the web, making a arrange of gadgets. Coordination sensors and programmable capabilities, IoT gadgets are revolutionizing our ordinary lives as well our proficient lives, making efficiencies, and making strides our quality of life.
IoT gadgets incorporate a wide run of devices executed in fabricating, horticulture, shrewd homes and more. For occurrence, shrewd sensors can control the sum of water utilized in a field, based on the level of precipitation, cutting costs, and optimizing the sum of water utilized. In keen homes, movement locators interface to indoor regulators, for ideal vitality utilization, coffee producers interface to cautions, for those who require their coffee within the morning, open front entryways by means of a farther control application, when kids call saying they overlooked their keys, and printers consequently arrange unused cartridges when ink levels are running low, to name fair a number of examples. According to Gartner, the introduced base of IoT gadgets in 2016 was near to 6.4 million, of which 62% were buyer gadgets. IoT endpoints are anticipated to develop at a 32% CAGR from 2016 through 2021, to reach an introduced base of fair over 25 billion units in 2021.

IoT Security Risks
Whereas these shrewd gadgets have certainly moved forward our lives, they come with vulnerabilities taking off them helpless to cyber-attacks. In truth, IoT gadgets are greatly simple to hack, advertising numerous focuses of section into our individual information and security frameworks, putting clients at noteworthy hazard. For occurrence, by remotely checking keen domestic sensors, hoodlums can recognize when the domestic is purge. They can misuse framework shortcomings in IoT fueled carport entryway frameworks, or keen bolt gadgets, to effectively break-in to homes. Remote assaults seem target our passwords and credit cards, as this information is effortlessly available from inside our systems. Our webcams and infant screens can be taken over to record our individual lives, taking off us helpless to shakedown and blackmail. you can seek help from nearest “Benchmark IT Services” if you feel any trouble.
Clearly, enterprises must implement security protocols to protect themselves from these vulnerabilities, however, with the majority of IoT devices currently deployed by consumers, it is imperative that all IoT consumers also implement security measures as well. Below an overview of recommended methods to secure your IoT devices.
Choose Who You Trust
Use Strong Passwords and Advanced Authentication Measures
Secure Your Networks
Be Your Own Guest
Limit Connectivity
Keep Up to Date
Monitor Bandwidth
security must be priority
To secure your home computer well, you are suggested to contact your local computer expert like “Computer Repair Onsite”.
conclusion
The degree to which Web security ought to be ensured, and the strategies utilized to do so is as of now beneath wrangle about. Whereas most concur that something must alter with respect to the individual data online, the arrangement is vague. Web security laws may secure citizens, but they undermine businesses and openness, one of the foundations of the Web. Social media and comparative online communication advances permit data sharing and collaboration that would be uncommon fair some decades prior. In any case, the cost of this association is security, a concept that’s not completely acknowledged by most Web clients. As Cory Doctorow put it in his article for the MIT Innovation Survey, “we exchange our protection for services.” Whether or not usually a reasonable bargain is up for wrangle about. The heart of the issue is that most Web clients who lock in in this trade ordinary are uninformed of what they are truly getting themselves into. Lawmakers, lobbyists and knowledge can contend over Web security until they are blue within the confront, and not come to any sort of conclusion. The as it were way in which we, as a associated society, will be able to shape the changing scene of the Web emphatically is in the event that individuals are mindful of what Web protection truly implies nowadays. To purchase the security software, you can go to the website like X-Tech Buy.