We all have heard somewhere about this term, IP address but do we really know that what afterall is an Ip address? Let us tech it easy today and explain some tricky terms simply about the IP address. IP means Internet Protocol. We know internet already, isn’t it? Protocol means a methodology that must be followed by the devices on internet to identify each other and then communicate. Now an IP address is nothing but just a series of numbers that is used to identify a source and/or a destination. Just imagine how in this extensive web of billions of devices, an email originally sent to you, finally makes its way and reaches only you and no one else. It is because the email in its structure or for that matter any communication sent in the world wide web (www) has details of its source and the destination. Those details include some numbers called IP address.
In simpler terms, any computer connected to the Internet shall have an IP address. Without an IP address you cannot even use the Internet. Your IP address will tell other Internet computers where to send the data you are seeking. It is like your home address which allows you to send letters and packages to people. There are two variants of the IP addresses, IP 4 (IPv4) and IP 6 (IPv6).
We need an IP address since two primary roles are provided by an IP address It is used as an interface identifier for a computer network and it also helps to provide the computer ‘s location, much like a physical address for a home or company.
How to find your IP Address on Windows
Finding your local IP address for other items to set up, such as printers. It can also be used to fix any technical issues / issues within your network. You can need to contact a Technical Support Associate for example and let them know your public IP address. Probably if you lose your connectivity to Internet. Another explanation would be to allow somebody to get into your network. There are many benefits to finding your local IP Address and information is always important. As mentioned above, this power is useful in many things, linking printers, technical support etc. and more.
Using Command prompt
Start> type Command prompt and press enter
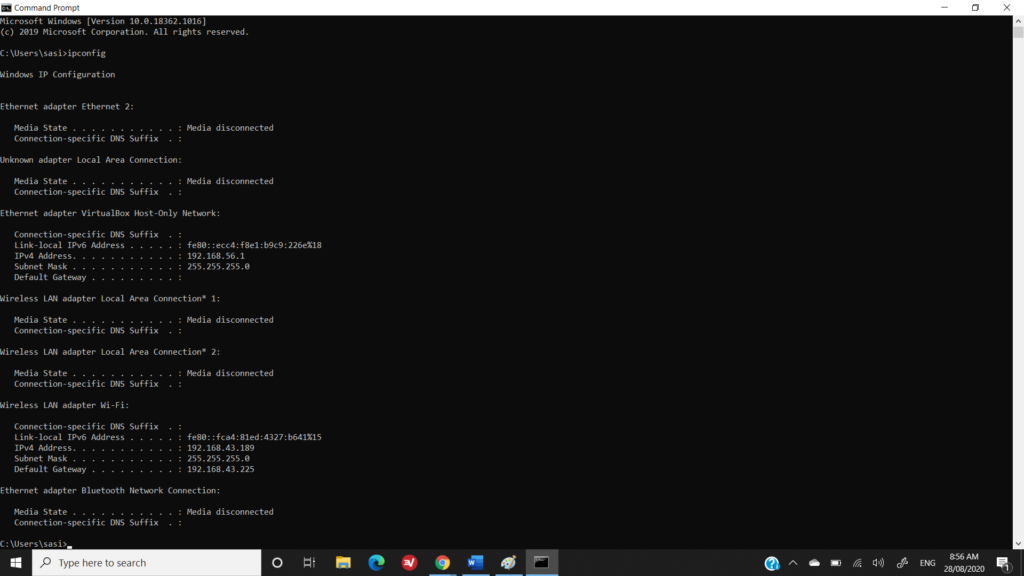
Once the command prompt is open type “ipconfig” to get your IP address information
Importance of IP address
Every gadget that takes an interest in network administration exercises must have a unique IP address. network benefits that utilization TCP/IP distinguish other network by utilizing IP addresses. The IP address gives the specific location of a host gadget on a system. If the internet protocol specifies that a destination address is on the local network, the packet will be sent directly to the host network. If the destination IP address is found not to be on the local network, instead the internet protocol searches for a connexion to a remote host. An address on the local network is a local address and a remote address on non-local network. Where the path is found, the packet is sent using router. If not, it is sent to the default gateway for the source host then the gateway connects the network using communication protocol.
What can an IP address reveal about you?
Your IP address can disclose a wide range of sensitive information about yourself. Your physical location including your residence, state / province, zip code and nation is the easiest piece of information to get. Whenever you change your physical location it will also change your IP address. You will also have one IP address at home and another IP address at a coffee shop.
The websites you visit that also connect your IP address to cookies, monitor software and other information to decide your preferences, with whom you interact, and the online services you use. You can use this information to target you with advertisements or sell your data to someone who wants your private information.
Finding your Internet Service Provider (ISP) from your IP address is also simple since ISPs are allocated a list of unique IP addresses to each. Your IP address can then theoretically be traced back to your ISP customer account to decide the following: Name, home address, phone number, credit card details, browsing history and more.
What can someone do with your IP address?
Block you from accessing websites
Your IP address can be used to prohibit you from carrying out other online activities. The most popular example of this is blocking the ability to access a specific site or posting comments in forums or web site comment section. This is also the most common way site administrators ban rulebreakers. It is also called “IP Ban.”
They can use your IP address to block you from playing online games and gamming services.
Spam you with personalized ads
Ever browsed online to buy shoes and closed it, after closing the browser you see lots of shoe ads on your social media feed? Well, the weird “coincidence” is basically how advertisers are monitoring you on the internet, and spamming you with advertisements that you might be interested in.
Tracking pixels are normally used by advertisers, but they do use your IP address. With it, they will offer location-based advertising in your mother tongue.
Some people may find this useful, but it seems like an infringement of our privacy for most of us.
They can know your location
Your IP address can reveal your location, but it will not be any specific than your city and state. Your IP address carries the name of your service provider. This information can be combined with other details together to identify your data.
How to protect your IP address
Use a VPN Service
A VPN is an on-line service you can use to mask your IP address quickly and easily. All you need to do is connect to a VPN server and its own address will automatically overwrite your real IP address. To buy a strong VPN, go to X-Tech Buy
It is better to use a VPN with a “Kill switch”. This way, if for whatever reason you ever lose your VPN connection, you won’t have to worry about someone seeing your real IP address, as the VPN will automatically cut off your web access before the connection runs again.
Use Tor Browser

People from all over the world use Tor to search and purchase goods and connect with those with limited access to the Internet, such as what happens in some countries.
The Tor Browser (such as Chrome, Firefox, or Safari) is a free software application that you download onto your device to cover your IP address while you go anonymously online. That free process is heavy-duty layered means your data layered with security and privacy protection.
Use a proxy server
Proxies are an easy way of making it seem like you have another IP address. They can really slow down your link though, they do not encrypt your operation, so they are not a good torrenting option. For home users without much IT experience, its recommended to call up your local computer expert like “Computer Repair Onsite.“
Update your router and firewall rules
Your router transmits data between networks, and your firewall does not allow unauthorised access. Make sure you change the administrative password on your router, as attackers also use default passwords to break into your network. Your ISP has the same default password and can be easily checked online. Set your firewall rules, so that no ping requests from the internet are allowed.
If you are worried that your private information is at stake and you wish to apply advanced security settings, feel free to connect with “BenchMark IT Services”
