In the modern world, sensors have their own vogue. The wireless sensor network has recently gained its place in the research world and piqued the interest of many researchers. Let us first understand the sensor. It happens to be a device designed to respond or detect any kind of physical or natural interference that is taken as its input. It gives the output in the form of an electric signal for any advancement as per its design. WSNs are networks of widely scattered and focused sensors that measure and preserve the physical nature of the site before transmitting the gathered data to a central point. It can be used to measure temperature, humidity, or pollution level. The data that is collected by these sensors are made to travel through multiple nodes, and the data is connected via a bridge to other networks as well.
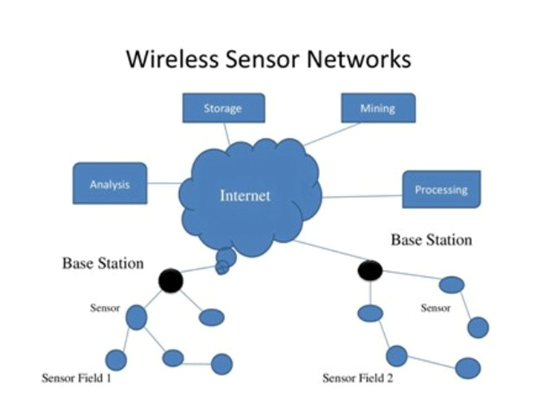
WSN has base stations and a lot of nodes that are supposed to observe the physical or natural intervention that it is programmed to and then pass the data further as mentioned in the algorithm that is used to design the device. Let us learn about the WSN topologies to understand the working deeply.
WSN Topologies:
There are various topologies in the structure of WSN like star, tree or also known as cluster tree, and mesh.
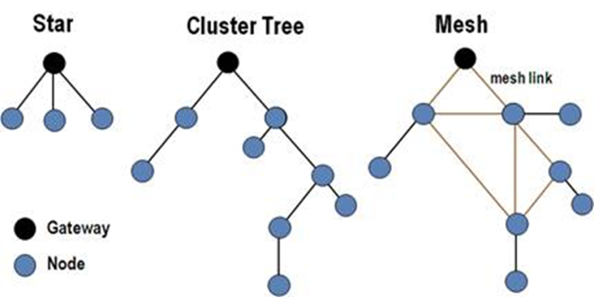
Fig. Link: https://theedugaragecom.files.wordpress.com/2020/04/image-11.png?w=768
These topologies give us a clear view of the working from node to node and all about the movement of the data. Let us briefly discuss these topologies.
Star Topology: It is the form of topology where each node is connected to the bridge or gateway. This means that a single bridge can take or send data to different and numerous nodes in some other network. There is a restriction on nodes from sending data among each other. And this restriction brings the dependency of the whole device on a single node that is considered as a liability.
Tree Topology: The nodes are interconnected to one another in this manner, and the bridge connects the top nodes. Because of this feature, the constraint in star topology is no longer present, and fault detection and network growth are also made easy. The only downside of this architecture is that it employs bus cable, which, if destroyed, causes the entire network to fail.
Mesh Topology: It permits data to move between nodes within a specific transmission range. However, if data is to be transmitted to a node from a distinct communication range, an intermediary node should be used to transport the data to its target node. If an issue arises with this sort of topology, it is extremely easy to discover and isolate it. The only significant drawback is the considerable economic investment necessary to set it up.
Types of WSNs:
There are various types of WSNs that are used according to the need of the situation. Let us now discuss them and how do they work.
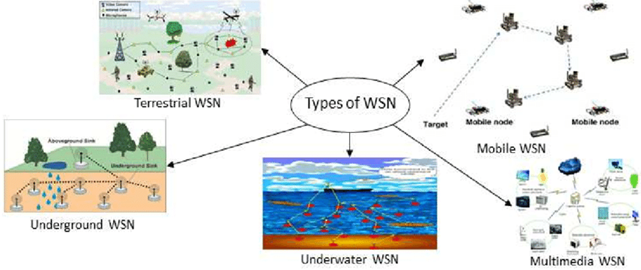
Terrestrial WSNs: Thousands of wireless sensor nodes are placed in a structure or unstructured form to communicate the base stations productively. The sensor nodes in an unstructured form are arbitrarily dispersed inside the target region that is deployed from a fixed plane. The structured model takes into account optimum position, grid placing, and 2D and 3D layout models. This model has the limitation of being battery dependent for power but it is equipped with solar cells as its alternate power source.
Underground WSNs: It requires more economy to set up and maintain this form of WSN when compared to the terrestrial model. This model has multiple sensor nodes that are buried in the ground and are used to monitor subterranean conditions. Additional sink nodes are installed above ground to transfer information from the sensor nodes to the base station. The nodes underground have a limited power supply and recharging the battery is also tough. Furthermore, the subterranean condition makes wireless communication difficult due to significant levels of distortion and signal loss.
Underwater WSNs: We are well aware of the ratio of water that covers our planet. These networks are made up of numerous sensor nodes and vehicles that are deployed underwater. Data from these sensor nodes is collected by remotely operated underwater vehicles. Underwater communication is hampered by significant propagation delays, as well as bandwidth and sensor problems. The battery of WSNs underwater cannot be recharged or replaced once they are exhausted.
Multimedia WSNs: This model has been suggested to allow for the surveillance and managing of multimedia events. These networks are made up of low-cost sensor nodes that are outfitted with recording devices. These nodes communicate with one another through a wireless link for data compression, extraction, and synchronization. Overconsumption of energy, increased bandwidth needs, data processing, and compression methods are among the problems of the multimedia WSN. Furthermore, multimedia information needs a large amount of bandwidth in order to be transmitted effectively and easily.
Mobile WSNs: As the name suggests, this model has the nodes that can be moved on their own and complete their designated job that is interaction with the surroundings. These nodes are capable of sense and communicate as well. M(obile) w(ireless) s(ensor) n(etworks) are far more adaptable than static sensor networks. Greater and enhanced coverage, better energy economy, superior channel capacity, and other benefits distinguish MWSN from static wireless sensor networks.
Attacks on WSNs:
After we know what WSNs are and how they work let us also understand the threats they face. Since these are networks, they are vulnerable to cyber-attacks. The attacks that are possible on these networks are classified as active and passive attacks.
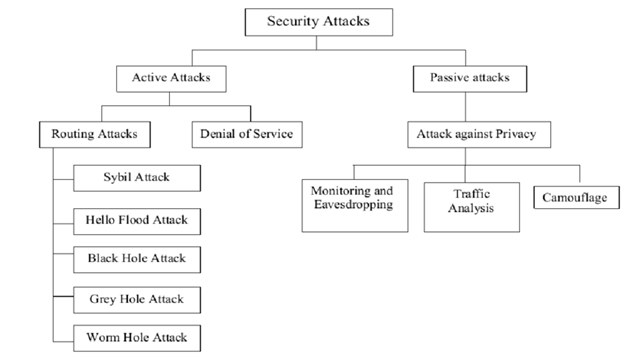
Active attacks are mainly when the attacker efforts to detach the transmitted data or modify it. An attacker can respond to previous messages while simultaneously inserting his own traffic to disrupt network operations or cause service failure. The passive attack might be limited to listening to and inspecting exchanged communications. As a result, this type of assault is more detectable. Because the attacker makes no changes to the data transmitted. The attacker’s objective is to obtain private relevant data from critical nodes inside the network by studying routing data.
