Everything about TCP/IP:
What is TCP/IP?
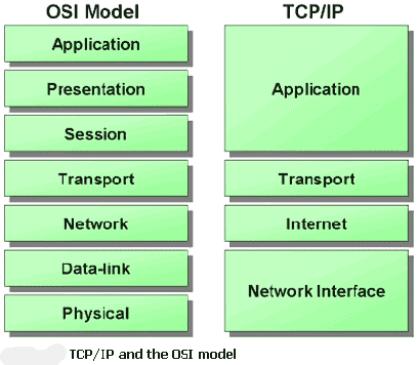
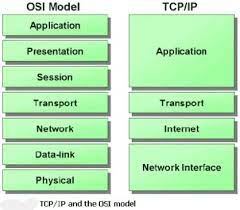
TCP/IP stands for Transmission Control Protocol/Internet Protocol. It is a set of communication protocols that are used to connect network devices over the internet. In a private computer network, TCP/IP is also used as a communications protocol (an intranet or extranet). The TCP/IP model came first, followed by the OSI model. It differs from the OSI model in some ways. The application layer, transport layer, network layer, data link layer, and physical layer are the five layers that make up this architecture. The first four levels, which correspond to the first four layers of the OSI model, include physical standards, network interface, internetworking, and transport services, and these four layers are represented in the TCP/IP paradigm by a single layer termed the application layer. TCP/IP is a hierarchical protocol made up of interacting modules, each of which has its own set of features.
The TCP/IP Model aids in determining how a particular computer should connect to the internet and how data should be sent between them. When many computer networks are linked together, it aids in the creation of a virtual network. The TCP/IP model was created to allow communication over long distances. Transmission Control Protocol/Internet Protocol (TCP/IP) is an acronym for Transmission Control Protocol/Internet Protocol. TCP/IP Stack is a model for providing a very reliable and end-to-end byte stream over an unreliable internetwork.
TCP/IP refers to the full IP suite, which includes a set of rules and procedures. TCP and IP are the two most common protocols, although the suite also includes others. Between internet applications and the routing and switching fabric, the TCP/IP protocol suite serves as an abstraction layer. This defines how data is exchanged over the internet by defining end-to-end communications that define how packets should be broken down, addressed, transported, routed, and received at their destination. TCP/IP is a network protocol that requires little central control and is meant to make networks more dependable by allowing them to automatically recover from the failure of any device on the network.
TCP/IP meaning:
The IP suite’s two primary protocols have distinct functions, TCP AND IP.
TCP describes how programmes can create channels of communication over a network, while UDP defines how applications can generate channels of communication across a network. It also controls how a message is broken down into smaller packets and sent over the internet, where it is reassembled in the correct order at the destination address.
IP specifies how each packet is addressed and routed to ensure that it reaches its intended destination. This IP address is checked by each gateway computer on the network to determine where the message should be forwarded. A subnet mask specifies which part of an IP address is used to represent the network and which part is used to identify hosts or other network devices on a computer or other network device. The virtualization of IP addresses is known as network address translation (NAT). NAT improves security while reducing the number of IP addresses required by an enterprise.
The following are the key features of the TCP IP protocol:
- A flexible TCP/IP architecture is supported.
- It’s simple to add extra systems to a network.
- The network remains intact in the TCP IP protocol suite until both the source and destination machines are operational.
- TCP (Transmission Control Protocol) is a connection-oriented protocol.
- TCP provides reliability by ensuring that data that arrives out of sequence is reordered.
- TCP allows for flow control, ensuring that the sender never overwhelms the receiver with data.
Benefits of TCP/IP:
Because of its original design for defence purposes, TCP/IP were actually design requirements, what we now call features or characteristics. The idea behind “Good Failure Recovery” was that the rest of its components would still function fully if some network were disables during an incursion or attack. The ability to add whole networks to the services already in place is also without any disturbance. The ability to handle high error rates was built so as to allow a mechanism to ensure that a packet of information was lost using the one route to reach its destination via another route. Independent platforms mean that networks and customers can include Windows, Unix, Macintosh or any other platform. It has a low overhead because TCP/IP is so efficient. For any network, performance is crucial. The speed and simplicity of TCP/IP is unparalleled. For interactive file transmission, TCP/IP can be utilised for network remote connection, email transmission, web site delivery and remote access to the file system of a server host. More generally, it represents how information changes when it travels from the physical concrete layer to the abstract application layer across a network. It details the fundamental communication protocols or methods.
Functions of TCP/IP model:
TCP/IP is separated into four layers, each of which has its own set of protocols:
TCP/IP is an architectural server layer in which each layer is defined by a particular function.
- Application Layer
- Transport Layer
- Internet Layer
- Network Interface
These four TCP IP layers work together, to transfer data from one layer to the next.
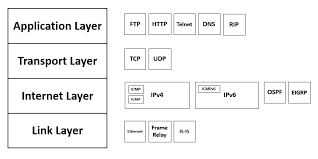
Let’s discuss what each layer does,
- Application layer: Application layer interacts with the highest level OSI model application programme. The application layer is the nearest OSI layer to the end-user. This means that the user interacts with other software applications using the OSI application layer. It offers standardised data exchange applications. HTTP, FTP, Post Office Protocol 3, Simple Mail Transfer Protocol, and a Simples Network Management Protocol form part of their protocols. The actual application data is payload here. This interacts to implement a communicating component with software applications. Data are always interpreted beyond the scope of the OSI model by the applicable program.
Example: file transfer, email, remote login, etc.
- Transport layer: The transportation layer builds on the network layer to deliver data transfer from a source system machine to a destination system process. It is hosted via single or multiple networks and maintains service quality. It determines where and at what rate the data should be sent. This layer builds on the message from the application layer. It helps to ensure error-free and successful delivery of data units. The transport layer ensures that end-to-end communications are maintained across the network. TCP manages inter-host communication and offers flow control, multiplexing and reliability.
Example: TCP.
- Internet layer: The second layer of TCP/IP layers of the TCP/IP model is an Internet layer. The network layer is also called. The main task of this layer is to send packets from all networks, whatever the route they go to, and any computer they still reach. In order to transfer variable data sequences from one node to the other via different networks, this internet layer offers the method of functionality and procedure. The network layer, known as the internet layer, handles packets and connects independent networks for transportation of packets across network frontiers. The IP and Internet Control Message Protocols for network layer protocols are for error reporting purposes.
Example: Error reporting
- Physical layer: This four-layer TCP/IP model layer is the network interface layer. The network access layer is also known as this. You can define how data should be sent over the network in detail. It also includes the use of hardware devices that interface directly with network media such as coaxial, optical, coaxial, fibre or twisted-pair cables as a means to signalise bit. A network layer is a data line combination and is defined in the reference model OSI article. This layer defines the physical transmission of the data over the network. The data transfer between two devices on the same network is carried out via the same layer.
Example: Ethernet
Advantages of TCP IP:
- It helps you to connect different computer types and settle them.
- Contributes to connecting different computer types;
- Works independently of the OS; it supports many routeing protocols
- Uses highly scalable client-server architecture
- Can be operated independently of the operating system.
- It supports several protocols for routeing.
- It allows for the inter-organisation internet.
- The model TCP/IP has a client-server architecture that is very scalable.
- It can be independently operated.
- Supports several protocols for routeing.
- The device can be used to connect two computers.
Disadvantages of TCP IP:
- TCP/IP is a complex model for configuration and management.
- TCP/IP is shallow/overhead above IPX (Internetwork Packet Exchange).
- Configuration and management is complicated; the transport layer does not guarantee packet delivery; TCP/IP protocols cannot be easily replicated; services, interface and protocol concepts are not clearly distinguished, so new technologies cannot be described in new networks; and they are particularly vulnerable to a synchronised attack, which is a type of denial-of-service attack.
- The transport layer model does not ensure that packets are delivered in this way.
- It is not easy to substitute protocol with TCP/IP.
Conclusion:
TCP/IP is the older and more well-known of the two techniques of data transfer. The OSI model is a tried-and-true paradigm that may be utilised as a foundation for most new applications, or at the very least taken into account when enhancing or expanding existing infrastructure. It will be utilised as a standard for all communications applications for many years to come. Because of its ongoing improvements and low failure rate, TCP/IP will continue to rule the internet. The Internet Protocol Suite is a protocol stack that is used on the web. TCP/IP is the name given to it in honor of two of the most well-known protocols, but there are others. The TCP/IP approach for networking is based on a five-layer concept. The physical, data link, network, transport, and application layers are listed in order from bottom to top (link to user application). Because the model does not entirely define all layers, other standards and protocols are used to fill in the gaps. The layers have names but no numbers, and although Layer 2 and Layer 3 are sometimes used, they are not TCP/IP words.
Now it’s up to you to choose which algorithm to utilise and which will produce better results in various instances. So keep experimenting and getting your hands dirty in the clustering world. If you’re having trouble making decisions or using data cluster analysis, there’s an experienced team right here for us, “BENCHMARK IT SERVICES,” where we can get all of the answers to our problems, whether it’s a major business problem or a single data problem. you can access the website here.

If you need to know more information or help about using this process to your organization, you can easily get “Computer Repair Onsite (CROS)” help by clicking here.