DoS attack- Denial of service or DoS attack is an attempt made by attacker to slow down the target machine so that its intended users cannot access it. Ins DoS attack, target machine or server is flooded with TCP and UDP requests. Attackers mainly perform DoS attack to restrict victim’s access server or a particular resource by making the target machine unavailable for its intended user. In DoS attack, target system’s operations and functions are delayed so that an authorized and trusted user cannot access computer resources, meanwhile attacker compromised target system. DoS attacks are mainly performed to stop and compromise communication between two end-users, instead of crashing the victim’s machine (Tripathi & Mehtre, 2013). To launch such attacks, attackers mainly target default gateways, web applications and servers and personal computers. The main purpose of performing this attack is to compromise confidentiality of victim’s personal data, integrity and availability. In most of cases, attackers try to exploit and compromise availability of the systems as it does not require any administrative privileges s compared to system integrity and confidentiality. Weaknesses in the TCP/IP protocol define the type of DoS attacks including ICMP flood, UDP flood, TCP SYN flood, buffer overflow attacks, incomplete HTTP requests and smurfing, etc. In order to launch DoS attacks, attackers mainly use a single system.
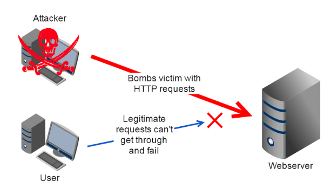
Figure 1: DoS attack using a single system
This figure illustrates that a legitimate user is trying to access a web server but at the same time an attacker is sending a flood of HTTP requests to the same web-server using a single machine, which shows that the intended user is not able to access their data or web applications (Suryateja, 2018). By doing so, attacker can steal all the information related to target user who is trying to access web server.
Methods of launching a DoS attack
A DoS attack can be launched in a number of ways as given below-
- Attackers can launch a DoS attack by consuming computational resources on the target system such as disk space, CPU time, and bandwidth.
- Another way to launch DoS attack is disruption of system configuration information such as routing information and physical network components.
A user can recognize DoS attack if:
- There is a rapid increase in the number of spam emails.
- A user is unable to access web-sites, web servers and other computational resources.
- If a user reported slow performance of network usually in opening and accessing the files (Suryateja, 2018).
What is a DDoS attack?
DDoS attack is a variant of DoS attack which is more complicated than DoS attack, in which attackers tries to shut down target system by overloading web server and web applications with a large number of requests. In a distributed denial of service (DDoS) attack, attacker uses multiple machines for targeting victim’s computational resources, with an intention to crash the targeted server (Obaid, 2020). In DDoS attacks, hundreds of thousands of zombie machines are used for sending fake network access requests to victims’ computational resources such as web servers, websites, etc.

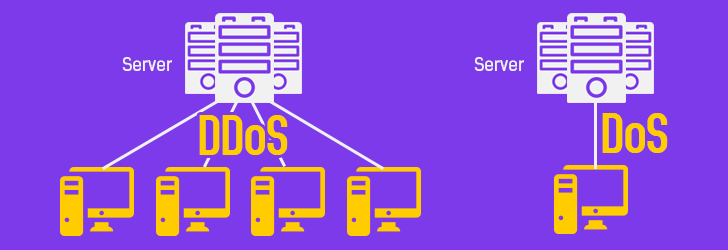
Figure 2: DDoS attack launched using multiple botnets
Source: https://cybernews.com/security/ddos-attacks-explained/
The above figure showed how a DDoS attack can be launched using botnets to compromise target systems. This attack is known as distributed because a large number of botnets or zombie machines are attacking on a target system. These bots are infected computers which include malware, virus, Trojans, etc. infections that can spread across multiple locations and in multiple computers to make them unavailable for its intended use. These bots or zombie machines are controlled centrally by an attacker but these bots can be located in different locations across the globe, owing to which they are difficult to detect and made DDoS more complicated than DoS attacks (BullGuard, 2022).
Methods to launch DDoS attacks
DDoS attacks can be launched in the same ways as DoS attacks, the only difference is that this attack is performed through a number of systems. There are three basic steps to be followed to launch this attack-
- Find a target system or service
- Exploit vulnerability and open port in the system
- Exploit vulnerability to overwhelm the service.
Types of DoS and DDoS attacks
Usually, DoS and DDoS attacks can be divided into categories given as follows:
- Volume-based attacks- This type of attack includes UDP flood, spoofed packet attacks, ping of death, etc., which are mainly performed to target bandwidth resources (Obaid, 2020). As a result of these types of attacks, entire system will cease or slow down the services.
- Protocol attacks- This kind of attack mainly consumes the resources of actual resources such as firewalls and load balancers. Protocol attacks include SYN flood attacks, Smurf DDoS attacks, fragmented packet attacks, ICMP flood, etc. attacks that are mainly performed to exploit vulnerabilities in layers 3&4 of OSI model.
- Application layer attacks- Attackers launch this kind of attack to crash the web server and web applications entirely, which includes fake network access requests that seem to be coming from a legitimate or trusted user. Such attacks include GET/POST attacks, Windows and OpenBSD weaknesses, Slowloris attack, etc. Application attacks have mainly targeted layer 7 of OSI model. In this type of attack, the attacker sends incomplete or partial HTTP requests, which make the network resources tie-up (Obaid, 2020).
Differences between DoS and DDoS attacks
| Parameters | DoS | DDoS |
| Definition | Denial of service attack is an attempt to make the target system’s resources unavailable for its intended users. | Distributed denial of service attack is an attempt to shut down or crash entire network or computational resources so as to access the target system by compromising it. |
| Sources of attack | DoS attack is launched by a single computer. | A large number of computers known as “Botnets” are used to attack the target system. |
| Ease of detection | It is easier to detect and mitigate as a single computer is used for launching attack, so the origin of the attacks and attacker’s system information can be located easily. | Since DDoS is launched with the help of thousands of botnets distributed globally, so it is more complex and difficult to detect. |
| Level of threat | Level of threat is low in case of a DoS attack as it can be mitigated and detected easily. | Level of threat in case of DDoS ranges from medium to high due to its complex nature and difficulty to mitigate. |
| Method of execution | DoS attack mainly uses a tool or script to attack target system. | DDoS attack is executed with the coordination of multiple botnets which are infected with viruses and malware. |
| Speed | Speed of deploying DoS attack is slow as it uses a single machine. | Speed of attack is very high, since attack originates from different locations using multiple botnets. |
| Protection and mitigation | System and computational resources can be protected by stopping it’s working. | Protection and mitigation of DDoS attacks are very difficult, nearly impossible. |
| Involvement of Malware | No malware is involved in the execution of DoS attack. | In DDoS attacks, botnets are infected with malware (KEARY, 2022). |
References:
- bullguard. (2022). What are DoS and DDoS attacks?. Bullguard.com. Retrieved 12 February 2022, from https://www.bullguard.com/bullguard-security-center/internet-security/internet-threats/what-are-dos-and-ddos-attacks.aspx.
- KEARY, T. (2022). DoS vs DDoS Attacks: The Differences and How To Prevent Them in 2022. Comparitech. Retrieved 12 February 2022, from https://www.comparitech.com/net-admin/dos-vs-ddos-attacks-differences-prevention/.
- Obaid, H. (2020). Denial of Service Attacks: Tools and Categories. International Journal Of Engineering Research & Technology (IJERT), 9(3). Retrieved 12 February 2022, from https://www.ijert.org/research/denial-of-service-attacks-tools-and-categories-IJERTV9IS030289.pdf.
- Tripathi, N., & Mehtre, B. (2013). DoS and DDoS Attacks: Impact, Analysis and Countermeasures. Advances In Computing, Networking And Security. Retrieved 12 February 2022, from https://www.researchgate.net/publication/259941506_DoS_and_DDoS_Attacks_Impact_Analysis_and_Countermeasures.