Abstract
Denial-of-Service attack or DoS attack is a cybersecurity attack in which the attacker makes the network or the system unavailable for the user temporarily or indefinitely until it has been resolved. In a Distributed Denial-of-Service attack or DDoS attack, attacker makes use of a network to stop the user from using the network or system. DoS and DDoS cybersecurity attacks are very dangerous in nature and attacker can steal user information or data and user might seem that there is probably something wrong with the internet connection or system is slowing down. The purpose of this blog is to demonstrate how an attacker can make use of DoS attack or DDoS attack and what vulnerabilities are being used by the attacker and how it can be resolved. The attack is performed inside a virtual machine so no machine has been actually targeted and is intended for learning purposes only. The virtual environment is created using Oracle Virtualbox and Ubuntu is used as the virtual machine.
Introduction
Distributed Denial-of-Service attack or infamously known as DDoS attack is a threatening attack where perpetrators slows down the network or system and then steal information from the user. Now a user might think that how slowing down or stoppage can result into an attack. Attackers try different methods like HTTP poisoning or ARP poisoning where they flood the network and while user is not able to do any task on the system and the attacker would penetrate inside the system. Recently in 2020, Amazon Web services were attacked by a brutal DDoS attack which lasted for three days. Thus, it is evident that DDoS attack is still at large and many big companies have been targeted and it is predicted to increase in coming years. This blog will present a simple way of how an attacker implements a DOS attack, what it does a system and how it can be stopped.
Implementation of DOS in Ubuntu
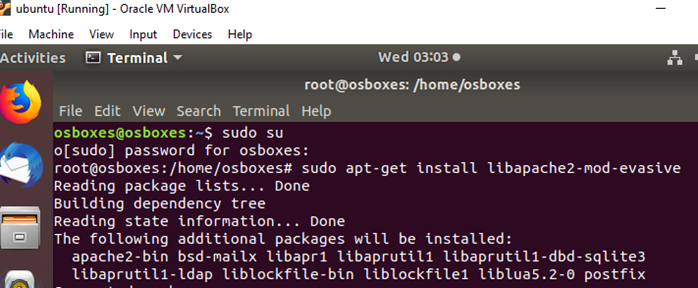
In order to implement DOS in ubuntu, the first requirement is to install Apache server with evasive mode. The Apache server is a free web server which powers up around 40% of websites. The evasive mode in Apache helps in protecting the server from various attacks like DoS, DDoS and brute force. In order to install Apache server in evasive mode, the command is ‘sudo apt-get install libapache2-mod-evasive’. If the reader is not familiar with commands in Linux, another blog can be read which depicts common commands in Kali Linux, which are very similar to Ubuntu. The screenshot below shows installation of Apache in Ubuntu.
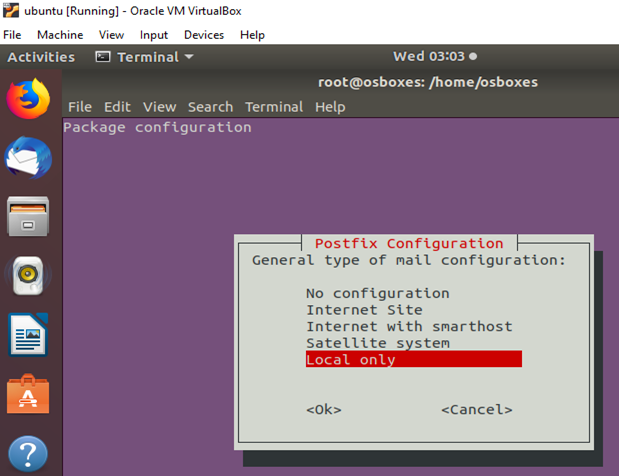
After the Apache server has been installed then it will ask for package configuration and in this ‘Local Only’ is used since the attack is only performed inside the virtual machine as shown below:
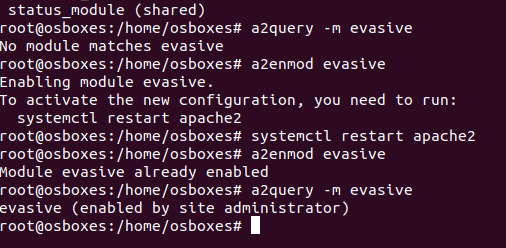
Further, when the completion of server takes place, then evasive mode needs to be enabled and in order to do that the command required is ‘a2enmod evasive’ as shown below.
Now, the configuration file of evasive mode can be opened which requires the command ‘a2query -m evasive’. This will open the following window.
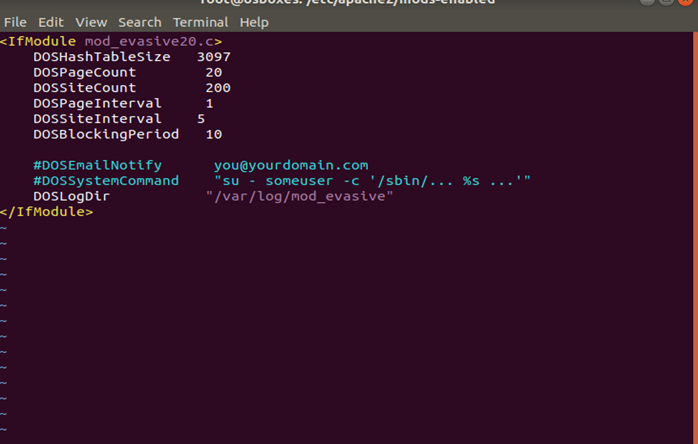
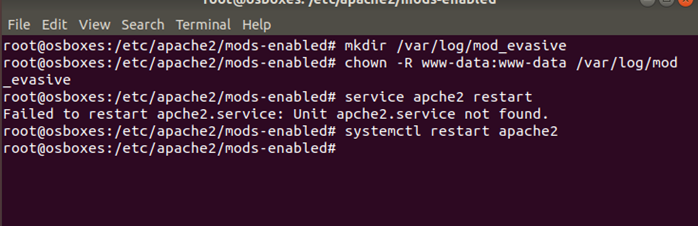
From the figure above, it is evident that the evasive mode has an option to create DoS hash tables. This will generate hash tables which will be running on the server and they will run a page count of 20 after every 5 seconds. This will slow down the server and then the connection will stop. In Apache server a directory can be created which would store logging information. In order to do that first directory is created using ‘mkdir’ command and then using command ‘chown’ permission is granted to read the directory as shown below:
Now initially, if the DoS attack was not implemented then when command ‘test.pl when ran, it will give the following results.
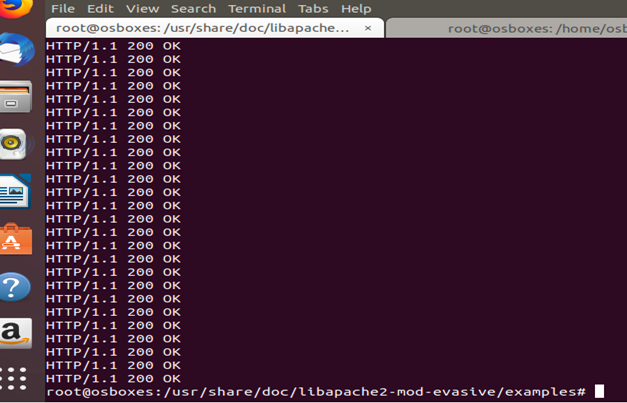
From the figure above, it is evident that the connection is established but after DOS hash table is generated then the following results are given:
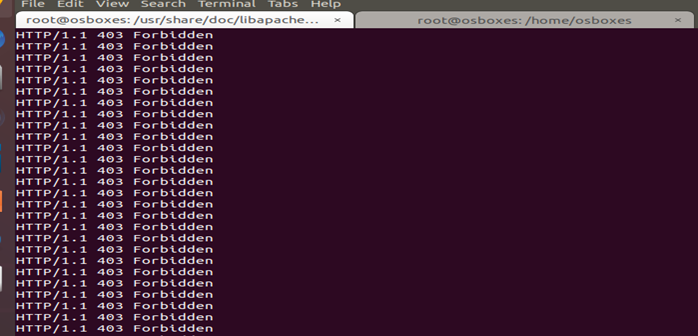
It is evident that the DoS hash table has stopped the connection to be established. Thus, DoS attack has been implemented successfully and connection has been cut off.
Prevention of DoS Attack
In order to prevent DoS attack, first the IP address of the attacker needs to be found. The log directory created before will help in figuring out about who is attacking the system. Now if the items are listed on the directory it will show the following results:
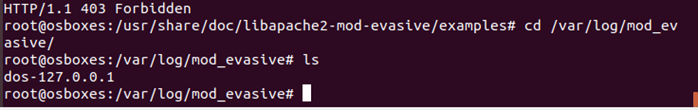
As clear from the figure that the attacker of DoS attack is ‘127.0.0.1’. Now if the IP address is blacklisted inside the configuration of the evasive mode then the attacker will not be able to attack the system anymore. Either the IP address can be blacklisted or DoS address can be whitelisted which would both block the IP address as shown below:
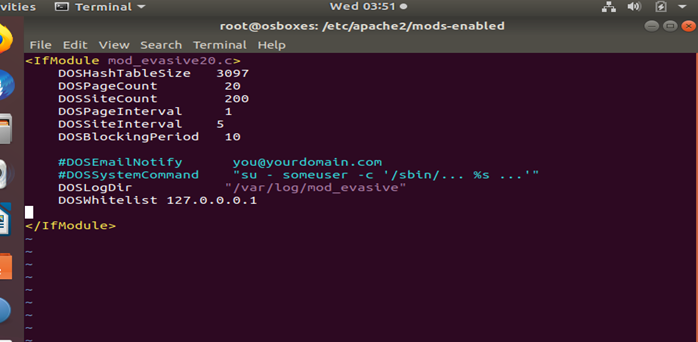
Now when the settings are saved then the attacker will not be able to attack anymore. From the image below, it is evident that again the connection has been re-established.
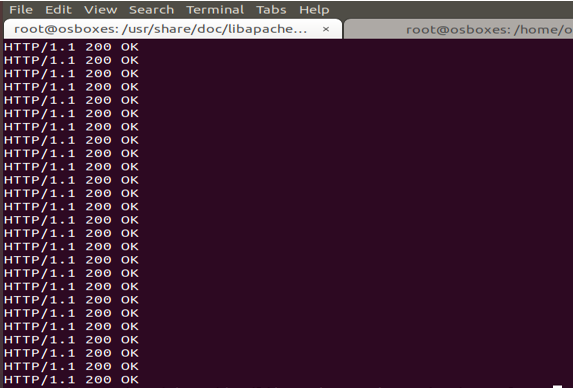
Now, the connection is back on and the attacker has been blocked. In case of DDoS attack, there will multiple network so it will be difficult to figure out the attacker.
Conclusion
DoS attack is widely used but DoS attack can be prevented but when it comes to DDoS attack it is really difficult to stop it. As shown, a single attacker was able to perform a heavy DoS attack and block the user to connect. There have been multiple DoS and DDoS attack and, in this blog, it was demonstrated how harmful they can be and how hard it is to prevent them. The evasive mode of Apache comes with different features where attackers can be blacklisted and thus stopping them. For learning purposes, hash tables can be generated inside the evasive mode of Apache. Recent DDoS attack on Amazon was really brutal and it is predicted that attacks will be continued in the future. Due to many ways a Dos or DDoS can be created, makes it hard to find it but maybe in future a better solution will be found.
