Hello Everyone i would like to discuss about DNS spoofing in Local Area Networks (LAN) which is a series of Cyber attacks. This blog will introduce the concepts of DNS and then take a deep drive into the security attacks
Abstract
Domain name system of Central protocol management system consists of Internet and service providers which are allocated to resolve all domain names, these are associated with critical communication of internet applications. DNS functionalities and positioning systems are introduced with the technique of query identification systems where the value of randomization is evaluated to analyze spoofing attacks. DNS spoofing management technologies are associated to analyze vulnerabilities in the existing DHCP server-side management where all the conflicts and data related functionalities are associated to detect the technique of all venerable actions. The application of proposed attackers is made easy to minimize a bandwidth compared to previous attacks and have a victim of client management systems where all the effects are initialized according to client management functionalities. Notarized data systems and DNS spoofing are associated with network protocol structures and detection and mitigation of risk technologies are authorized to improve the detection of attacks system.
Introduction
Domain name system management functionalities are efficiently used with Internet applications where the domain probability of corresponding IP addresses is associated with web server management where all the databases of resource functionalities and record maintenance structures are not only used with the hostname or IP address in but all the nameservers, mail exchanges are interrelated to create efficient output. The capability of denial of service attack will target the available resources and perform various tools and techniques which could launch the attacks according to the success criteria of targeting variable systems. The functionalities and capabilities of malicious applications and DNS cache server management capabilities are deployed according to query attacks and consist of a large number of client management functionalities where bandwidth and cloud fare DDoS functionalities are associated to create smooth business technologies with a runtime enterprise system. The capability of targeted DNS spoofing attacks is associated to send and receive the signal according to the positioning of cache server management. The functionalities and calculations of proposed attacks are exploited with loophole management functionalities where DHCP server IP addresses are associated according to o exploitation functions.
DNS spoofing attack
The DNS spoofing attack will analyze applications of end client management systems where positioning of catchy management functionalities is accessed according to loophole management systems where all the DHCP servers are integrated with the IP address conflict system. The virtualization-based 1 abilities of network access will increase the capability of routing configuration systems and all the malicious applications which enter into the network configuration are reduced to include all the parameters and used for future communication protocol.
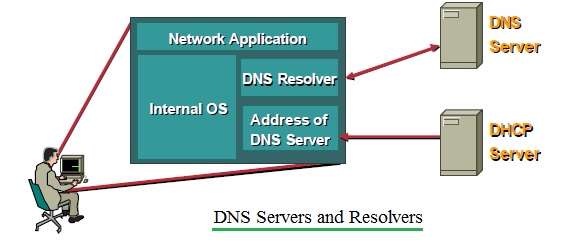
DHCP and DNS protocol
The DHCP and DNS protocol for integrated to create efficient network exchange between the servers and these are associated with DHCP client and DHCP server management to obtain all parameters of IP address in systems. The capability of the local DNS management system will resolve all the problems which are required with a domain name with the correspondent IP address. The application will resolve all domain names into IP addresses and all the queries which are acquired with DNS servers will create efficient communication which will have a server communication between the name of service and resolve all the problems acquired with network attacks.
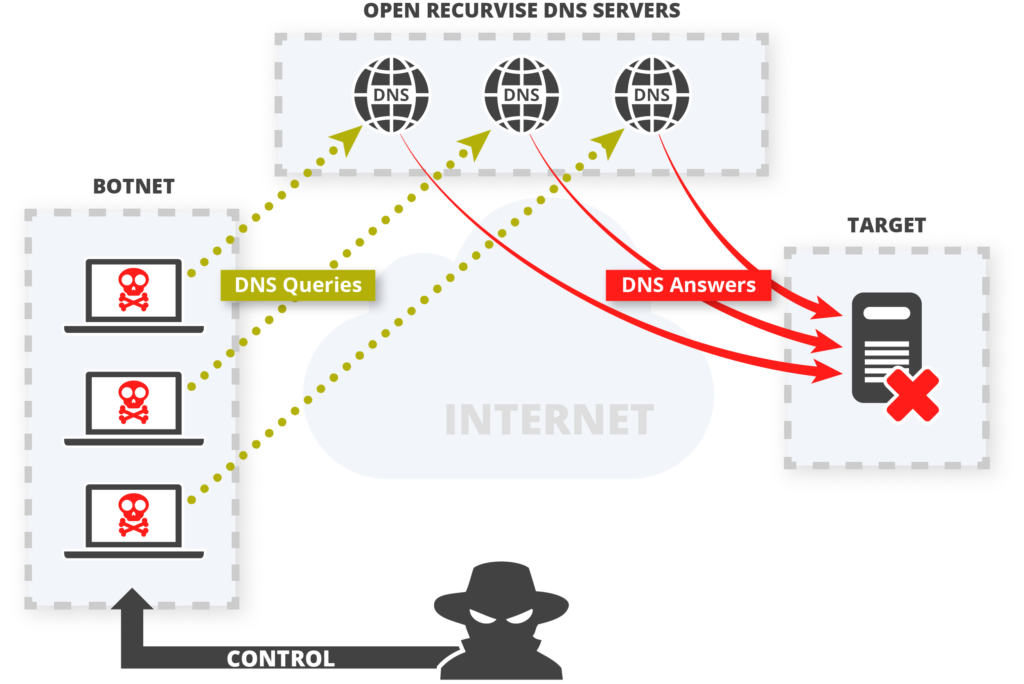
Attacks against DNS protocol
The DNS spoofing and DNS management systems are associated with various types of attacks.
- DNS catchy positioning systems will have efficient hijacking systems where the authorized nameserver record will force victims to use the name server to trigger route resolution of DNS server management technologies.
- The access point and credentials of response regarding nameservers are associated according to the authorization of the target domain management system.
DNS application attacks
The DNS applications are used with DDoS network attacks and create malicious client application technologies where several zombies will enter into the DNS system and force the propagation of IP address in the schema. The traffic interrelations and response of message transitions are acquired with query data transactions. The volume of network transitions and the response of messages are associated to deploy a query management functionality where open DNS management will resolve all the orders and network transitions and create efficient traffic flow functionalities according to cloud-based techniques where the mitigation of DNS management is also associated with network conduction.
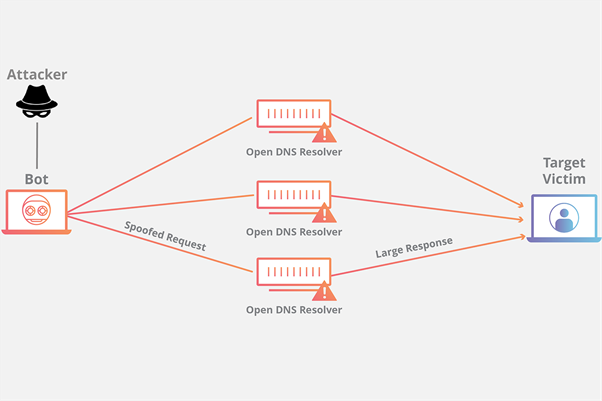
DNS query flooding
The DNS query flooding has created the amplification with all the attacks and has communication between a victim name server and a large number of DNS servers. All the applications and network protocols are associated to prolong threshold frequency switch not associated in network data transmission protocol.
Target of DNS spoofing
1. Attack description
- The attack description and network topology of the entire system configuration are associated according to DHCP server management where all the malicious clients and victim-related functionalities are interconnected to half various network transition applications.
- DHCP discover is one of the victim clients which will join the entire network credentials with broadcast management functionalities.
- Network transitions and the source of IP addresses and destination points are associated according to the application of the attacker’s description perspectives.
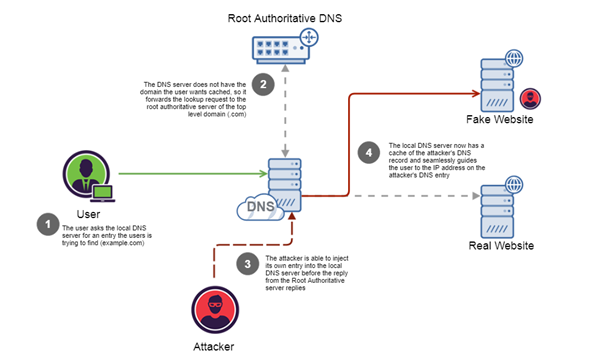
Spoofing and poisoning
DNS network applications and all the protocols are associated according to the security concern and all the applications and network routing systems are associated according to the significance of vulnerability issue management.
The DNS cache repositioning will resolve all the problems and produce accurate results according to the implementation of specific functionality. Designing of DNS system management are attackers created to have an authentication response according to the validation of fact. It is necessary to enhance all the functionalities and produce DNS resolution according to the request of catchy and spoofed management technologies.
All the DNS resolution and spoofing attacks are associated whenever we give incorrect information and recursive DNS environment.
Click here for any cyber security issues
DNS Resolution
The resolution of DNS servers is associated with Network authentication progression systems. The application of all performances is associated to analyse server fail methodologies and pick up a credential according to server management systems and high load line methods are deployed to handle all client and server requests according to the efficient interaction management system. The network application will minimize the risk associated with resolution factors and give high-end outputs.
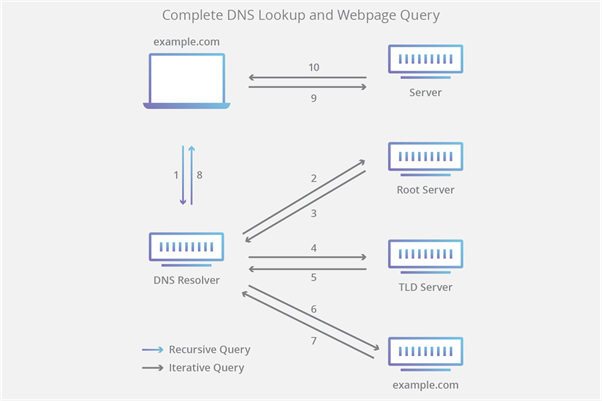
- The capability of client initiations and requests regarding DNS resolution are acquired through ISP or internet protocol routing the propagation with the URL management system.
- Locale resolvers and lookup catcher method are also associated according to the catcher request of URL functionalities where the IP address and schemas are deployed with local DNS server management.
- The capability and propagation of authorization service are associated with DNS management systems where all the functionalities are provided with local resolver methods.
If you have any queries leave your comments and will get back to you with another topic.